A new variant of the Agent Tesla malware has been observed delivered by using a lure file with the ZPAQ compression structure to harvest information from numerous email purchasers and nearly 40 web browsers.
“ZPAQ is a file compression structure that delivers a greater compression ratio and journaling function in contrast to greatly utilised formats like ZIP and RAR,” G Details malware analyst Anna Lvova said in a Monday investigation.
“That suggests that ZPAQ archives can be smaller sized, saving storage area and bandwidth when transferring information. Nonetheless, ZPAQ has the greatest drawback: confined software assist.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Initially appearing in 2014, Agent Tesla is a keylogger and remote accessibility trojan (RAT) published in .NET that’s provided to other danger actors as portion of a malware-as-a-assistance (MaaS) design.
It truly is often utilised as a to start with-phase payload, supplying remote accessibility to a compromised technique and utilized to down load much more innovative 2nd-phase applications this sort of as ransomware.
Agent Tesla is generally delivered through phishing email messages, with current campaigns leveraging a six-calendar year-outdated memory corruption vulnerability in Microsoft Office’s Equation Editor (CVE-2017-11882).
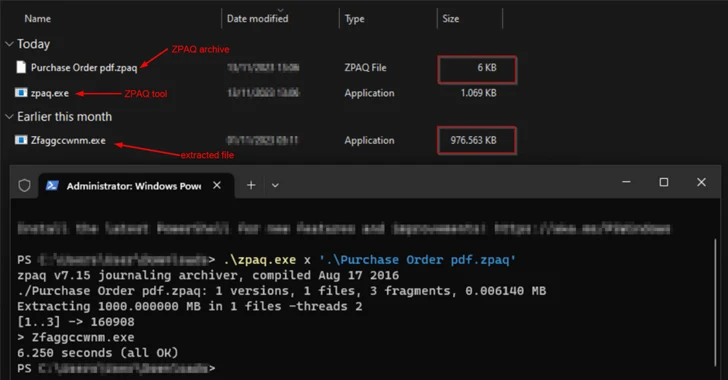
The most current attack chain starts with an email that contains a ZPAQ file attachment that purports to be a PDF document, opening which extracts a bloated .NET executable that’s largely padded with zero bytes to artificially inflate the sample dimension to 1 GB in an work to bypass standard security measures.
“The principal function of the unarchived .NET executable is to down load a file with .wav extension and decrypt it,” Lvova defined. “Employing frequently utilized file extensions disguises the targeted visitors as ordinary, creating it far more difficult for network security alternatives to detect and prevent malicious exercise.”

The finish aim of the attack is to infect the endpoint with Agent Teslathat’s obfuscated with .NET Reactor, a genuine code defense computer software. Command-and-control (C2) communications is attained by means of Telegram.
The progress is a signal that menace actors are experimenting with unheard of file formats for malware shipping, necessitating that consumers be on the lookout for suspicious e-mail and preserve their systems up-to-date.
“The utilization of the ZPAQ compression structure raises much more questions than solutions,” Lvova stated. “The assumptions in this article are that both menace actors target a certain group of persons who have complex awareness or use a lot less broadly known archive instruments, or they are screening other methods to distribute malware a lot quicker and bypass security application.”
Located this posting intriguing? Stick to us on Twitter and LinkedIn to study much more exclusive material we submit.
Some parts of this short article are sourced from:
thehackernews.com


 How Multi-Stage Phishing Attacks Exploit QRs, CAPTCHAs, and Steganography
How Multi-Stage Phishing Attacks Exploit QRs, CAPTCHAs, and Steganography