A big-scale attack campaign learned in the wild has been exploiting Kubernetes (K8s) Purpose-Based Obtain Manage (RBAC) to generate backdoors and operate cryptocurrency miners.
“The attackers also deployed DaemonSets to consider more than and hijack assets of the K8s clusters they attack,” cloud security organization Aqua reported in a report shared with The Hacker Information. The Israeli organization, which dubbed the attack RBAC Buster, reported it observed 60 uncovered K8s clusters that have been exploited by the menace actor driving this marketing campaign.
The attack chain commenced with the attacker gaining original accessibility by means of a misconfigured API server, adopted by examining for evidence of competing miner malware on the compromised server and then employing RBAC to set up persistence.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“The attacker designed a new ClusterRole with around admin-degree privileges,” the firm explained. “Following, the attacker created a ‘ServiceAccount’, ‘kube-controller’ in the ‘kube-system’ namespace. Lastly, the attacker developed a ‘ClusterRoleBinding’, binding the ClusterRole with the ServiceAccount to produce a sturdy and inconspicuous persistence.”
In the intrusion observed versus its K8s honeypots, the attacker tried to weaponize the exposed AWS accessibility keys to get hold of an entrenched foothold into the environment, steal data, and escape the confines of the cluster.
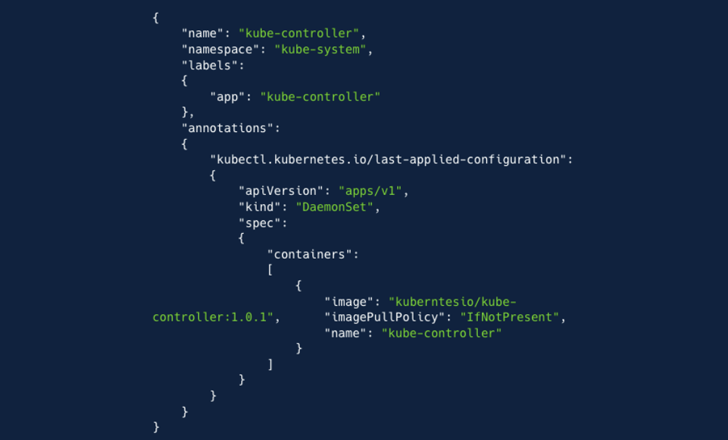
The closing step of the attack entailed the risk actor making a DaemonSet to deploy a container graphic hosted on Docker (“kuberntesio/kube-controller:1..1”) on all nodes. The container, which has been pulled 14,399 moments since its add five months in the past, harbors a cryptocurrency miner.
Impending WEBINARZero Trust + Deception: Learn How to Outsmart Attackers!
Find how Deception can detect advanced threats, quit lateral motion, and enrich your Zero Have faith in approach. Be a part of our insightful webinar!
Help you save My Seat!
“The container graphic named ‘kuberntesio/kube-controller’ is a circumstance of typosquatting that impersonates the authentic ‘kubernetesio’ account,” Aqua reported. “The picture also mimics the well-known ‘kube-controller-manager’ container impression, which is a critical ingredient of the regulate plane, managing in a Pod on each learn node, dependable for detecting and responding to node failures.”
Apparently, some of the methods explained in the campaign bear similarities to a further illicit cryptocurrency mining procedure that also took benefit of DaemonSets to mint Dero and Monero. It is really presently not apparent no matter whether the two sets of attacks are associated.
Discovered this write-up exciting? Stick to us on Twitter and LinkedIn to study a lot more exclusive content we submit.
Some areas of this write-up are sourced from:
thehackernews.com


 GhostToken Flaw Could Let Attackers Hide Malicious Apps in Google Cloud Platform
GhostToken Flaw Could Let Attackers Hide Malicious Apps in Google Cloud Platform