The infamous North Korean point out-backed hacking group Lazarus uploaded 4 deals to the Python Package deal Index (PyPI) repository with the target of infecting developer devices with malware.
The packages, now taken down, are pycryptoenv, pycryptoconf, quasarlib, and swapmempool. They have been collectively downloaded 3,269 periods, with pycryptoconf accounting for the most downloads at 1,351.
“The package names pycryptoenv and pycryptoconf are comparable to pycrypto, which is a Python deal employed for encryption algorithms in Python,” JPCERT/CC researcher Shusei Tomonaga explained. “As a result, the attacker possibly organized the malware-containing destructive packages to target users’ typos in putting in Python packages.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The disclosure will come days right after Phylum uncovered several rogue deals on the npm registry that have been utilized to one out computer software developers as component of a campaign codenamed Contagious Job interview.

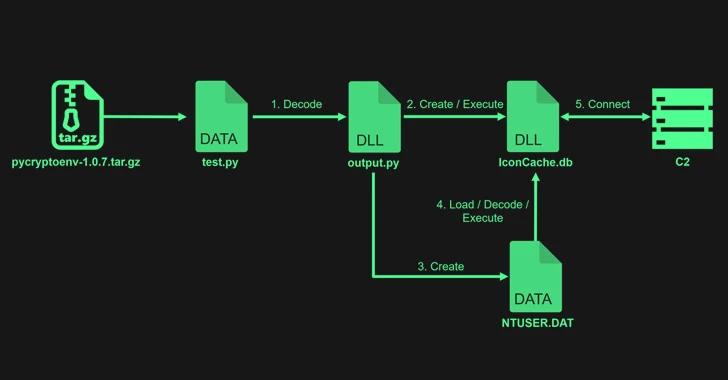
An attention-grabbing commonality among the two sets of attacks is that the malicious code is concealed in the exam script (“exam.py”). In this case, however, the check file is basically a smokescreen for what is actually an XOR-encoded DLL file, which, in turn, produces two DLL data files named IconCache.db and NTUSER.DAT.
The attack sequence then uses NTUSER.DAT to load and execute IconCache.db, a malware known as Comebacker that is liable for setting up connections with a command-and-handle (C2) server to fetch and operate a Windows executable file.
JPCERT/CC explained the offers are a continuation of a campaign that Phylum initial detailed in November 2023 as leveraging crypto-themed npm modules to deliver Comebacker.
“Attackers may perhaps be targeting users’ typos to have the malware downloaded,” Tomonaga reported. “When you install modules and other forms of computer software in your progress ecosystem, you should do so carefully to stay away from putting in unwelcome deals.”
Discovered this report attention-grabbing? Stick to us on Twitter and LinkedIn to examine more unique content material we submit.
Some pieces of this report are sourced from:
thehackernews.com

 Chinese Hackers Exploiting Ivanti VPN Flaws to Deploy New Malware
Chinese Hackers Exploiting Ivanti VPN Flaws to Deploy New Malware