Chinese users searching for respectable application these types of as Notepad++ and VNote on lookup engines like Baidu are getting qualified with destructive ads and bogus links to distribute trojanized versions of the application and eventually deploy Geacon, a Golang-dependent implementation of Cobalt Strike.
“The malicious web-site uncovered in the notepad++ search is dispersed by means of an advertisement block,” Kaspersky researcher Sergey Puzan stated.
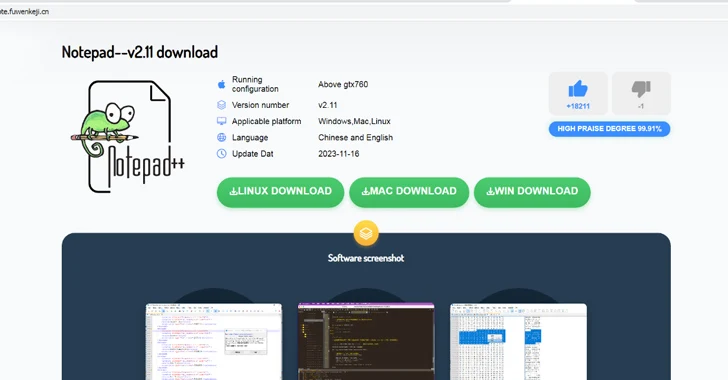
“Opening it, an attentive consumer will straight away recognize an amusing inconsistency: the web site tackle includes the line vnote, the title offers a down load of Notepad‐‐ (an analog of Notepad++, also dispersed as open up-supply software), even though the picture proudly shows Notepad++. In truth, the offers downloaded from in this article comprise Notepad‐‐.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The website, named vnote.fuwenkeji[.]cn, has download backlinks to Windows, Linux, and macOS variations of the software program, with the website link to the Windows variant pointing to the official Gitee repository that contains the Notepad– installer (“Notepad–v2.10.-plugin-Installer.exe”).
The Linux and macOS versions, on the other hand, direct to malicious set up packages hosted on vnote-1321786806.cos.ap-hongkong.myqcloud[.]com.
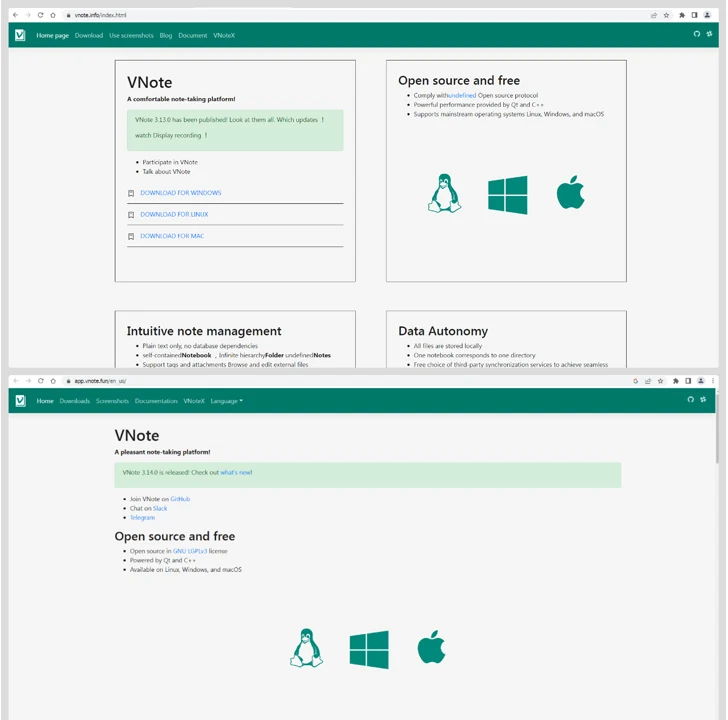
In a very similar style, the phony appear-alike websites for VNote (“vnote[.]details” and “vnotepad[.]com”) direct to the very same set of myqcloud[.]com back links, in this scenario, also pointing to a Windows installer hosted on the domain. That reported, the back links to the probably malicious variations of VNote are no longer active.
An assessment of the modified Notepad– installers reveals that they are made to retrieve a subsequent-stage payload from a remote server, a backdoor that reveals similarities with Geacon.

It is really capable of making SSH connections, executing file functions, enumerating procedures, accessing clipboard written content, executing data files, uploading and downloading documents, taking screenshots, and even moving into into sleep method. Command-and-manage (C2) is facilitated by usually means of HTTPS protocol.
The advancement comes as malvertising campaigns have also acted as a conduit for other malware this sort of as FakeBat (aka EugenLoader) malware with the assistance of MSIX installer information masquerading as Microsoft OneNote, Idea, and Trello.
Found this write-up exciting? Abide by us on Twitter and LinkedIn to examine more special content material we write-up.
Some pieces of this posting are sourced from:
thehackernews.com

 LockBit Ransomware Hacker Ordered to Pay $860,000 After Guilty Plea in Canada
LockBit Ransomware Hacker Ordered to Pay $860,000 After Guilty Plea in Canada