Malicious Android applications masquerading as Google, Instagram, Snapchat, WhatsApp, and X (formerly Twitter) have been noticed to steal users’ credentials from compromised devices.
“This malware uses famed Android application icons to mislead customers and trick victims into putting in the malicious app on their gadgets,” the SonicWall Seize Labs threat research workforce mentioned in a current report.
The distribution vector for the campaign is presently unclear. Nonetheless, at the time the application is set up on the users’ telephones, it requests them to grant it permissions to the accessibility products and services and the machine administrator API, a now-deprecated aspect that offers unit administration capabilities at the technique level.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Getting these permissions will allow the rogue application to achieve management over the product, building it possible to have out arbitrary actions ranging from information theft to malware deployment devoid of the victims’ understanding.
The malware is intended to build connections with a command-and-command (C2) server to obtain instructions for execution, making it possible for it to entry get hold of lists, SMS messages, call logs, the listing of set up apps send out SMS messages open up phishing internet pages on the web browser, and toggle the digicam flashlight.

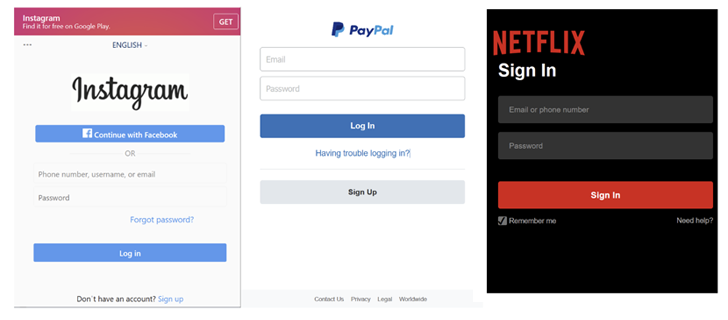
The phishing URLs mimic the login pages of nicely-identified providers like Facebook, GitHub, Instagram, LinkedIn, Microsoft, Netflix, PayPal, Proton Mail, Snapchat, Tumblr, X, WordPress, and Yahoo.
The advancement will come as Broadcom-owned Symantec warned of a social engineering campaign that employs WhatsApp as a supply vector to propagate a new Android malware by posing as a defense-related application.
“Upon thriving supply, the software would set up alone beneath the guise of a Contacts software,” Symantec reported. “Upon execution, the app would ask for permissions for SMS, Contacts, Storage, and Telephone and subsequently clear away by itself from look at.”
It also follows the discovery of malware strategies distributing Android banking trojans like Coper, which is capable of harvesting sensitive information and facts and exhibiting phony window overlays, deceiving users into unknowingly surrendering their qualifications.
Final week, Finland’s Nationwide Cyber Security Centre (NCSC-FI) unveiled that smishing messages are becoming utilised to direct users to Android malware that steals banking details.
The attack chain leverages a procedure identified as telephone-oriented attack delivery (TOAD), whereby the SMS messages urge the recipients to call a variety in relationship with a credit card debt selection assert.
When the phone is made, the scammer on the other conclude informs the victim that the concept is fraudulent and that they need to install an antivirus application on their phone for defense.
They also instruct the caller to click on on a link sent in a second textual content information to install the purported security software, but in actuality, is malware engineered to steal online banking account qualifications and eventually complete unauthorized fund transfers.
Although the specific Android malware pressure utilised in the attack was not discovered by NCSC-FI, it is suspected to be Vultr, which was in-depth by NCC Team early very last month as leveraging a nearly equivalent procedure to infiltrate products.

Android-centered malware this kind of as Tambir and Dwphon have also been detected in the wild in latest months with different device accumulating features, with the latter concentrating on cell telephones by Chinese handset makers and mostly meant for the Russian marketplace.
“Dwphon arrives as a element of the system update software and displays numerous features of pre-installed Android malware,” Kaspersky reported.
“The precise an infection path is unclear, but there is an assumption that the contaminated application was integrated into the firmware as a consequence of a achievable supply chain attack.”
Telemetry details analyzed by the Russian cybersecurity organization reveals that the range of Android users attacked by banking malware increased by 32% when compared to the past year, leaping from 57,219 to 75,521. A bulk of the bacterial infections have been described in Turkey, Saudi Arabia, Spain, Switzerland, and India.
“Despite the fact that the quantity of customers influenced by Computer system banking malware carries on to drop, […] the yr 2023 observed the variety of users encountering cellular banking Trojans improve appreciably,” Kaspersky observed.
Uncovered this write-up attention-grabbing? Stick to us on Twitter and LinkedIn to go through far more exclusive content we publish.
Some components of this short article are sourced from:
thehackernews.com


 Researchers Uncover ‘LLMjacking’ Scheme Targeting Cloud-Hosted AI Models
Researchers Uncover ‘LLMjacking’ Scheme Targeting Cloud-Hosted AI Models