Cybersecurity researchers on Wednesday took the wraps off a “basic but amazing” malware loader for destructive Windows binaries targeting Central Europe, North The us and the Middle East.
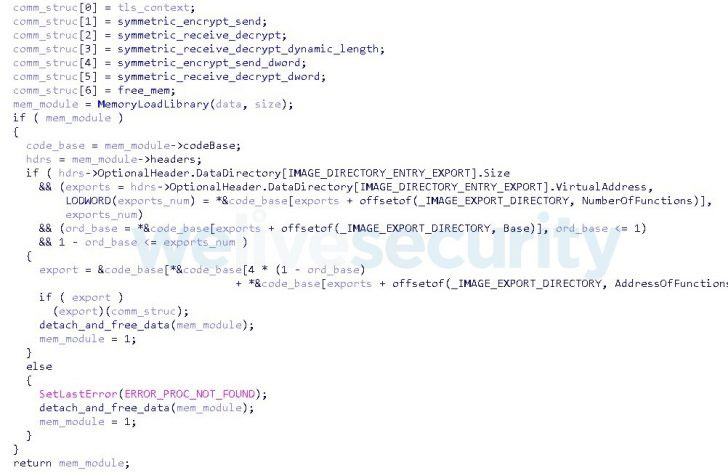
Codenamed “Wslink” by ESET, this previously undocumented malware stands aside from the relaxation in that it operates as a server and executes received modules in memory. There are no particulars offered on the original compromise vector and there are no code or operational overlaps that tie this resource to a recognised menace actor team.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The Slovak cybersecurity company pointed out that it has noticed only a handful of detections in the previous two several years, suggesting that it could be made use of in extremely-targeted cyber infiltrations.
Wslink is built to run as a provider and can settle for encrypted portal executable (PE) files from a particular IP deal with, which is then decrypted and loaded into memory prior to the execution. To achieve this, the customer (i.e., the target) and the server complete a handshake that includes the trade of cryptographic keys vital to encrypt the modules making use of AES.
“Interestingly, the modules reuse the loader’s functions for interaction, keys and sockets as a result they do not have to initiate new outbound connections,” ESET researcher Vladislav Hrčka stated. “Wslink additionally features a properly-developed cryptographic protocol to shield the exchanged details.”
The results come as researchers from Zscaler and Cisco Talos disclosed nevertheless another malware loader identified as SQUIRRELWAFFLE which is distributed by using spam email campaigns to deploy Qakbot and Cobalt Strike on compromised units.
Uncovered this short article intriguing? Observe THN on Fb, Twitter and LinkedIn to examine additional special content material we write-up.
Some elements of this write-up are sourced from:
thehackernews.com


 Malicious NPM Libraries Caught Installing Password Stealer and Ransomware
Malicious NPM Libraries Caught Installing Password Stealer and Ransomware