Cyber attacks making use of contaminated USB an infection drives as an preliminary entry vector have witnessed a a few-fold boost in the very first 50 percent of 2023,
That’s in accordance to new results from Mandiant, which thorough two this kind of campaigns – SOGU and SNOWYDRIVE – focusing on both community and non-public sector entities across the environment.
SOGU is the “most common USB-primarily based cyber espionage attack using USB flash drives and 1 of the most intense cyber espionage strategies focusing on equally general public and non-public sector businesses globally throughout sector verticals,” the Google-owned risk intelligence business mentioned.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The action has been attributed to a China-based cluster identified as TEMP.Hex, which is also tracked under the names Camaro Dragon, Earth Preta, and Mustang Panda. Targets incorporate development and engineering, company companies, govt, wellness, transportation, and retail in Europe, Asia, and the U.S.
The infection chain thorough by Mandiant exhibits tactical commonalities with an additional marketing campaign specific by Check Position, which took the wraps off a pressure of self-propagating malware named WispRider that spreads by way of compromised USB drives and possibly breach air-gapped techniques.
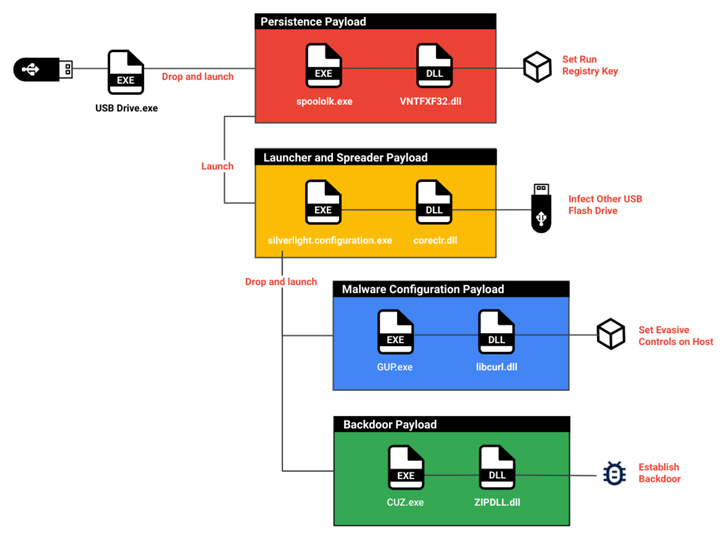
It all commences with a malicious USB flash generate plugged into a laptop, major to the execution of PlugX (aka Korplug), which then decrypts and launches a C-primarily based backdoor known as SOGU that exfiltrates documents of curiosity, keystrokes, and screenshots.
SNOWYDRIVE Targets Oil and Fuel Companies in Asia
The next cluster to leverage the USB infiltration system is UNC4698, which has singled out oil and gasoline companies in Asia to deliver the SNOWYDRIVE malware to execute arbitrary payloads on the hacked units.
Upcoming WEBINARShield Towards Insider Threats: Learn SaaS Security Posture Management
Nervous about insider threats? We’ve acquired you protected! Be a part of this webinar to check out useful tactics and the strategies of proactive security with SaaS Security Posture Management.
Join Currently
“As soon as SNOWYDRIVE is loaded, it produces a backdoor on the host system, offering attackers the ability to remotely issue program instructions,” Mandiant scientists Rommel Joven and Ng Choon Kiat said. “It also spreads to other USB flash drives and propagates through the network.”
In these attacks, the target is lured into clicking on a booby-trapped file that masquerades as a legitimate executable, thus activating a chain of malicious steps, setting up with a dropper that establishes a foothold, followed by executing the SNOWYDRIVE implant.
Some of the functionalities of the backdoor consist of carrying out file and listing lookups, uploading and downloading documents, and launching a reverse shell.
“Businesses must prioritize implementing restrictions on accessibility to exterior units such as USB drives,” the researchers reported. “If this is not doable, they should at minimum scan these products for malicious data files or code prior to connecting them to their interior networks.”
Found this posting attention-grabbing? Adhere to us on Twitter and LinkedIn to study far more exclusive articles we publish.
Some sections of this article are sourced from:
thehackernews.com


 Cybercriminals Exploit Microsoft Word Vulnerabilities to Deploy LokiBot Malware
Cybercriminals Exploit Microsoft Word Vulnerabilities to Deploy LokiBot Malware