Microsoft Term files exploiting regarded distant code execution flaws are getting utilised as phishing lures to drop malware called LokiBot on compromised programs.
“LokiBot, also regarded as Loki PWS, has been a well-known facts-stealing Trojan active since 2015,” Fortinet FortiGuard Labs researcher Cara Lin stated. “It mainly targets Windows programs and aims to acquire sensitive data from contaminated equipment.”
The cybersecurity company, which spotted the campaign in Might 2023, mentioned the attacks just take advantage of CVE-2021-40444 and CVE-2022-30190 (aka Follina) to reach code execution.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The Phrase file that weaponizes CVE-2021-40444 is made up of an exterior GoFile url embedded inside of an XML file that sales opportunities to the obtain of an HTML file, which exploits Follina to download a next-phase payload, an injector module written in Visual Simple that decrypts and launches LokiBot.
The injector also features evasion tactics to examine for the presence of debuggers and determine if it is really managing in a virtualized natural environment.
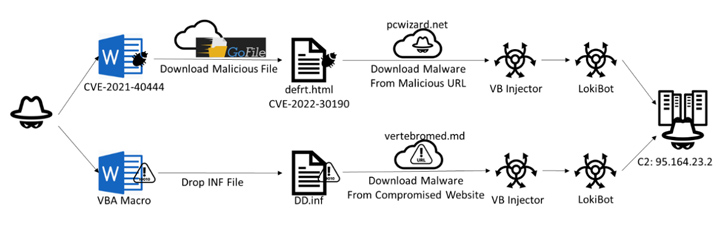
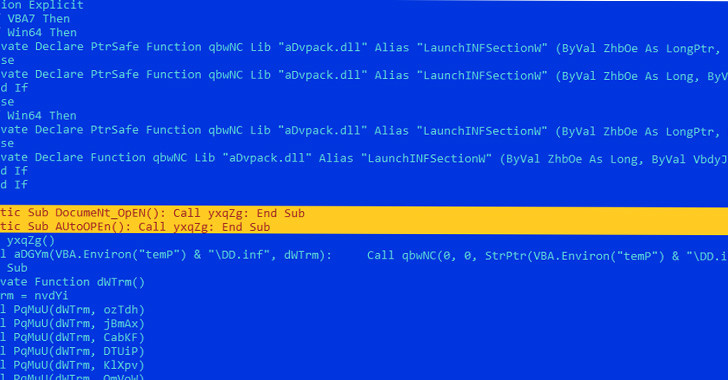
An different chain learned towards the close of May possibly begins with a Word doc incorporating a VBA script that executes a macro instantly upon opening the document using the “Vehicle_Open up” and “Doc_Open up” capabilities.
The macro script subsequently functions as a conduit to provide an interim payload from a distant server, which also capabilities as an injector to load LokiBot and connect to a command-and-control (C2) server.
Forthcoming WEBINARShield In opposition to Insider Threats: Master SaaS Security Posture Administration
Fearful about insider threats? We’ve bought you coated! Be a part of this webinar to check out sensible techniques and the tricks of proactive security with SaaS Security Posture Management.
Sign up for Nowadays
LokiBot, not to be perplexed with an Android banking trojan of the same name, will come with capabilities to log keystrokes, capture screenshots, collect login credential data from web browsers, and siphon details from a assortment of cryptocurrency wallets.
“LokiBot is a extensive-standing and widespread malware energetic for lots of a long time,” Lin claimed. “Its functionalities have matured more than time, creating it uncomplicated for cybercriminals to use it to steal delicate details from victims. The attackers guiding LokiBot constantly update their preliminary entry methods, allowing for their malware campaign to locate a lot more efficient ways to unfold and infect units.”
Located this short article interesting? Comply with us on Twitter and LinkedIn to browse far more special content material we submit.
Some areas of this write-up are sourced from:
thehackernews.com

 CERT-UA Uncovers Gamaredon’s Rapid Data Exfiltration Tactics Following Initial Compromise
CERT-UA Uncovers Gamaredon’s Rapid Data Exfiltration Tactics Following Initial Compromise