Microsoft on Wednesday said that a person containment characteristic in Microsoft Defender for Endpoint helped thwart a “large-scale remote encryption attempt” built by Akira ransomware actors targeting an mysterious industrial business in early June 2023.
The tech giant’s risk intelligence team is tracking the operator as Storm-1567.
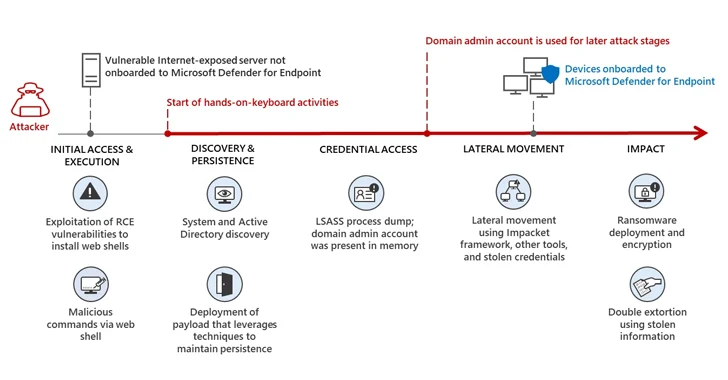
The attack leveraged gadgets that have been not onboarded to Microsoft Defender for Endpoint as a protection evasion tactic, although also conducting a series of reconnaissance and lateral motion actions prior to encrypting the gadgets utilizing a compromised consumer account.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
But the new automated attack disruption capability meant that the breached accounts are prevented from “accessing endpoints and other sources in the network, limiting attackers’ potential to move laterally regardless of the account’s Active Directory condition or privilege level.”

In other words, the concept is to minimize off all inbound and outbound conversation and prohibit human-operated attacks from accessing other equipment in the network.
Redmond also stated its organization endpoint security system disrupted lateral movement makes an attempt from a healthcare investigate lab in August 2023, in which the adversary reset the password for a default domain administrator account for observe-on actions.

“Remarkably privileged consumer accounts are arguably the most vital belongings for attackers,” Microsoft claimed. “Compromised domain admin-level accounts in environments that use traditional remedies present attackers with access to Lively Listing and could subvert standard security mechanisms.”
“Pinpointing and made up of these compromised person accounts, for that reason, stops attacks from progressing, even if attackers achieve original accessibility.”
Identified this post exciting? Abide by us on Twitter and LinkedIn to go through much more exclusive content material we put up.
Some pieces of this posting are sourced from:
thehackernews.com

 Researchers Uncover Malware Posing as WordPress Caching Plugin
Researchers Uncover Malware Posing as WordPress Caching Plugin