Substantial-profile governing administration and telecom entities in Asia have been qualified as section of an ongoing marketing campaign given that 2021 that’s created to deploy simple backdoors and loaders for providing upcoming-phase malware.
Cybersecurity business Look at Position is monitoring the exercise beneath the name Stayin’ Alive. Targets contain organizations found in Vietnam, Uzbekistan, Pakistan, and Kazakhstan.
“The simplistic character of the equipment […] and their huge variation suggests they are disposable, primarily utilized to down load and operate extra payloads,” it said in a report published Wednesday. “These applications share no very clear code overlaps with products established by any known actors and do not have much in popular with every single other.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

What is noteworthy about the campaign is that the infrastructure shares overlaps with that employed by ToddyCat, a China-linked menace actor recognised for orchestrating cyber assaults in opposition to federal government and armed service companies in Europe and Asia due to the fact at the very least December 2020.
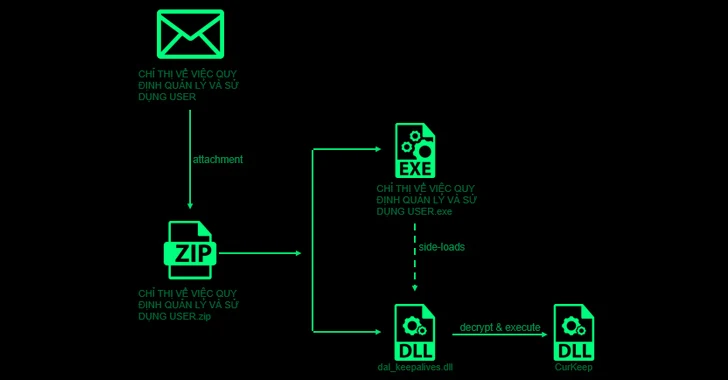
Attack chains start with a spear-phishing email that incorporates a ZIP file attachment with a respectable executable that leverages DLL aspect-loading to load a backdoor named CurKeep by usually means of a rogue DLL dal_keepalives.dll current in just the archive.
CurlKeep is designed to mail details about the compromised host to a remote server, execute commands despatched by the server, and produce server responses to a file on the technique.

A closer evaluation of the command-and-control (C2) infrastructure has unveiled a constantly evolving arsenal of loader variants dubbed CurLu, CurCore, and CurLog that are capable of obtaining DLL files, executing distant instructions, and launch a course of action related with a recently created file to which details from the server is penned to.

Also learned is a passive implant named StylerServ that listens on five distinctive ports (60810, 60811, 60812, 60813, and 60814) to accept a remote link and acquire an encrypted configuration file.
Although there is no conclusive evidence to join Stayin’ Alive to ToddyCat, the findings clearly show that the two intrusion sets use the identical infrastructure to go after a equivalent established of targets.
“The use of disposable loaders and downloaders, as observed in this marketing campaign, is turning out to be a lot more common even among the innovative actors,” it said. “The use of disposable resources will make both equally detection and attribution efforts far more tough, as they are changed normally, and probably written from scratch.”
Discovered this posting attention-grabbing? Stick to us on Twitter and LinkedIn to go through a lot more exclusive information we put up.
Some sections of this report are sourced from:
thehackernews.com

 Two High-Risk Security Flaws Discovered in Curl Library – New Patches Released
Two High-Risk Security Flaws Discovered in Curl Library – New Patches Released