Getty Photographs
Microsoft has introduced it will disable all Visible Fundamental Software (VBA) macros acquired from the internet in Business office documents by default in a bid to tackle common exploitation of the technique applied for malware and ransomware shipping.
Cyber security experts have prolonged termed on Microsoft to change its approach to VBA macros and the transfer has been greeted positively by practically all corners of the industry. The default setting will be applied to five Microsoft Office environment solutions – Term, Excel, Powerpoint, Visio, and Entry – and will start out rolling out to Windows people in April 2022 with the Model 2203 update by way of the Present Channel (preview).

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The alter will be obtainable in other update channels at an unspecified later on date, like in Current Channel, Monthly Business Channel, and Semi-Annual Enterprise Channel. Office LTSC, Workplace 2021, Place of work 2019, Office 2016, and Workplace 2013 will also ultimately all receive the update.
VBA macros are usually applied in Microsoft business office merchandise to automate repeat manual features and are particularly commonplace in industries like accounting and finance to expedite duties in spreadsheets, for example.
Cyber attackers are also commonly drawn to the element to aid the launch of cyber attacks or distribute malware, a approach most generally used in phishing attacks. A prevalent state of affairs would see an attacker mail a phishing email to an individual’s function account containing a seemingly innocuous Workplace document connected.

Microsoft
Once the document is downloaded and opened, the consumer would be offered with a doc with a notification in the toolbar furnishing the consumer to ‘enable content’ which would see the macro operate and whatever destructive payload connected with it downloaded and installed.
Figures from Netskope’s January Cloud Risk Report uncovered that the use of Microsoft Business documents related to malware downloads greater to 37% by the stop of 2021, in comparison to 19% at the start of 2020.
“A extensive assortment of risk actors go on to target our customers by sending files and luring them into enabling destructive macro code,” said Tom Gallagher, associate group engineering manager at Business Security. “Normally, the destructive code is element of a doc that originates from the internet (email attachment, connection, internet download, etc.). At the time enabled, the destructive code gains entry to the identity, documents, and network of the human being who enabled it.”
Microsoft is modifying the default behaviour of macros in five Workplace applications so that end users will no longer be capable to help them with just one simply click of a mouse. As a substitute, end users will now be introduced with a button encouraging them to click on and master extra about the opportunity impacts of enabling macros, and what destructive kinds can attain on a corporate network.
“The default is extra safe and is expected to maintain extra end users secure like home users and info employees in managed organisations,” Microsoft mentioned.
Neighborhood reaction
The cyber security group has arrive out in droves to aid the move from Microsoft, a go that some corners of the sector have requested for some time. As just lately as the weekend, the matter resurfaced on social media with specialists contacting for a modify in technique to macros.
At some point you identify some attributes just aren’t safe and sound ample to go away enabled by defaultSomeone on the Windows crew recognized that and manufactured a challenging choiceSomeone on the Business workforce demands to be changed with an individual who can comprehend and make a complicated selection
— Nathan McNulty (@NathanMcNulty) February 5, 2022
Malware strategies introduced by means of phishing attacks are ordinarily the chief exploiters of VBA macros, these kinds of as the recently resurfaced Emotet campaign which relies on the method as a key entry place. Experts feel the move is anticipated to lower the selection of cyber attacks in organizations considerably.
“The implications of turning Macros off by default is a large get for security as it drastically lessens the likely victim scope of macro-centered attacks for cybercriminals,” said Joseph Carson, chief security scientist at Delinea to IT Pro.
“In the earlier, we relied intensely on consumers to make security choices on macros with a warning – this can potentially lower the dangers from curious employees who may possibly just take the warning and run the macro that could result in stolen credentials or a thoroughly compromised equipment. The issue lies in how quickly organisations can up grade to this version as place of work updates can normally just take a very long time, however at minimum all those who have moved to cloud alternatives should reward quicker.”
Other authorities have reported destructive macros account for “about 25% of all ransomware entry” – a figure they explain as “conservative” mainly connected to larger sized ransomware organisations like the kinds most a short while ago specific by global legislation enforcement.
Serious-world applicability
Some corners of the field have lifted worries about how very easily it will be for enterprises to enforce the new default guidelines for Office files presented the entrenched culture of macros use in specific industries.
Security experts have mentioned specific customers who rely on macros for major parts of their position, this sort of as accountants, will very likely complain to IT departments asking for the default to be reverted back again to the a person-simply click performance of just before, even with the pitfalls.
Other folks disagree, saying the change will only add a small layer of friction to regular processes. Magni Reynir Sigurðsson, senior supervisor of detection systems at Cyren explained: “this will not have an affect on industries that rely on files using macros, they will just have to consider the more step of enabling them file by file for precise information they do trust”.
“For all those industries that intensely rely on macros these kinds of as fiscal or accounting industries, the hope is that Microsoft will, at final, make it straightforward sufficient for folks to change it on for on-demand from customers reasons on accredited files and scanned files,” included Carson.
Administrator possibilities
There are a amount of policies readily available to process administrators who wish to permit the new macro options in a custom made way, 1 that is suitable for their organization. These kinds of procedures include things like:
- Blocking macros from running in Place of work files from the Internet – Microsoft recommends enabling this policy and the organisation will not be influenced by the default modify
- Opening documents from a Trusted Location
- Opening documents with digitally signed macros and providing the certification to the user, who then installs it as a Reliable Publisher on their community machine
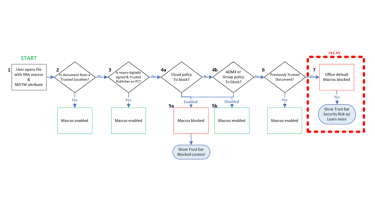
Microsoft
The impression previously mentioned outlines the evaluation stream for Office documents with VBA macros and Mark of the Web (MOTW) – an attribute added to information by Windows when it is sourced from an untrusted location.
Administrators can read extra about how the change impacts the environments in Microsoft’s devoted posting for Business admins.
Some sections of this article are sourced from:
www.itpro.co.uk


 Online Safety Bill will require porn sites to verify age of UK users
Online Safety Bill will require porn sites to verify age of UK users