Microsoft is urging clients to continue to keep their Trade servers up to date as effectively as get methods to bolster the setting, this sort of as enabling Windows Prolonged Protection and configuring certification-primarily based signing of PowerShell serialization payloads.
“Attackers looking to exploit unpatched Trade servers are not likely to go away,” the tech giant’s Trade Group said in a put up. “There are as well many features of unpatched on-premises Trade environments that are valuable to bad actors on the lookout to exfiltrate data or commit other malicious functions.”
Microsoft also emphasised mitigations issued by the business are only a stopgap answer and that they can “grow to be inadequate to shield in opposition to all versions of an attack,” necessitating that consumers install necessary security updates to safe the servers.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Exchange Server has been verified to be a rewarding attack vector in new a long time, what with a variety of security flaws in the application weaponized as zero-times to hack into devices.
In the earlier two decades by yourself, numerous sets of vulnerabilities have been identified in Exchange Server – including ProxyLogon, ProxyOracle, ProxyShell, ProxyToken, ProxyNotShell, and a ProxyNotShell mitigation bypass known as OWASSRF – some of which have occur less than widespread exploitation in the wild.
Bitdefender, in a complex advisory printed this week, explained Trade as an “suitable concentrate on,” when also chronicling some of the actual-environment attacks involving the ProxyNotShell / OWASSRF exploit chains because late November 2022.
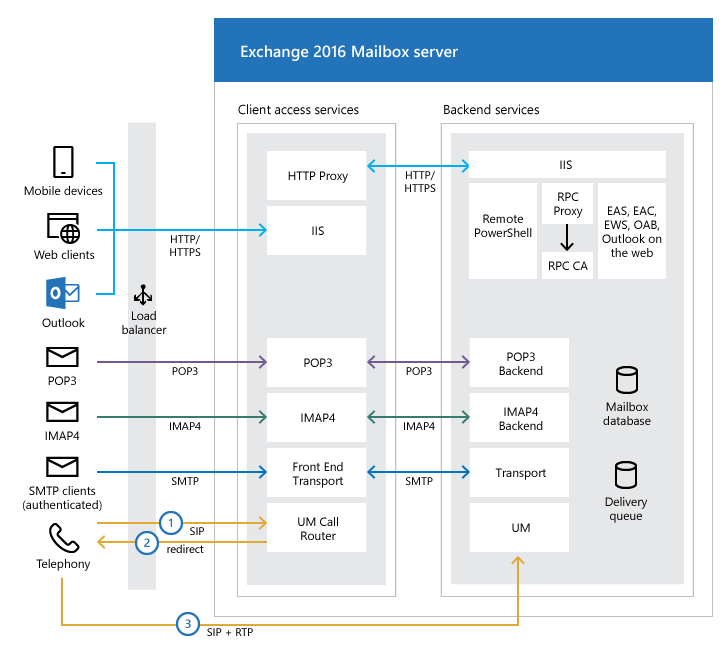
“There is a sophisticated network of frontend and backend companies [in Exchange], with legacy code to provide backward compatibility,” Bitdefender’s Martin Zugec observed. “Backend companies belief the requests from the front-end [Client Access Services] layer.”
One more reason is the fact that many backend providers operate as Exchange Server alone, which arrives with Method privileges, and that the exploits could grant the attacker malicious access to the distant PowerShell service, successfully paving the way for the execution of malicious instructions.
To that conclusion, attacks weaponizing the ProxyNotShell and OWASSRF flaws have targeted arts and enjoyment, consulting, regulation, producing, authentic estate, and wholesale industries positioned in Austria, Kuwait, Poland, Turkey, and the U.S.
“These types of server-facet ask for forgery (SSRF) attacks enable an adversary to mail a crafted ask for from a vulnerable server to other servers to access means or information and facts that are normally not specifically available,” the Romanian cybersecurity company explained.
Most of the attacks are stated to be opportunistic instead than centered and specific, with the infections culminating in the tried deployment of web shells and remote checking and administration (RMM) software package this sort of as ConnectWise Control and GoTo Take care of.
Web shells not only offer you a persistent distant accessibility system, but also enable the criminal actors to perform a vast variety of abide by-on routines and even offer the accessibility to other hacker teams for revenue.
In some scenarios, the staging servers utilised to host the payloads ended up compromised by Microsoft Exchange servers them selves, suggesting that the similar system might have been used to broaden the scale of the attacks.
Also observed ended up unsuccessful attempts undertaken by adversaries to obtain Cobalt Strike as well as a Go-centered implant codenamed GoBackClient that will come with capabilities to collect procedure information and facts and spawn reverse shells.
The abuse of Microsoft Exchange vulnerabilities has also been a recurring tactic used by UNC2596 (aka Tropical Scorpius), the operators of Cuba (aka COLDDRAW) ransomware, with just one attack leveraging the ProxyNotShell exploit sequence to drop the BUGHATCH downloader.
“Though the first infection vector keeps evolving and danger actors are rapid to exploit any new chance, their put up-exploitation functions are familiar,” Zugec explained. “The best safety towards modern-day cyber-attacks is a defense-in-depth architecture.”
Uncovered this write-up fascinating? Abide by us on Twitter and LinkedIn to browse much more exceptional written content we put up.
Some components of this article are sourced from:
thehackernews.com


 Eliminating SaaS Shadow IT is Now Available via a Self-Service Product, Free of Charge
Eliminating SaaS Shadow IT is Now Available via a Self-Service Product, Free of Charge