The danger actors related with the Gootkit malware have made “notable improvements” to their toolset, including new factors and obfuscations to their infection chains.
Google-owned Mandiant is checking the action cluster less than the moniker UNC2565, noting that the usage of the malware is “special to this group.”
Gootkit, also identified as Gootloader, is distribute by way of compromised internet sites that victims are tricked into visiting when hunting for business enterprise-related files like agreements and contracts by using a strategy called look for engine optimization (Website positioning) poisoning.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The purported files choose the kind of ZIP archives that harbor the JavaScript malware, which, when released, paves the way for further payloads this kind of as Cobalt Strike Beacon, FONELAUNCH, and SNOWCONE.
FONELAUNCH is a .NET-based loader developed to load an encoded payload into memory, and SNOWCONE is a downloader that is tasked with retrieving up coming-stage payloads, usually IcedID, by means of HTTP.
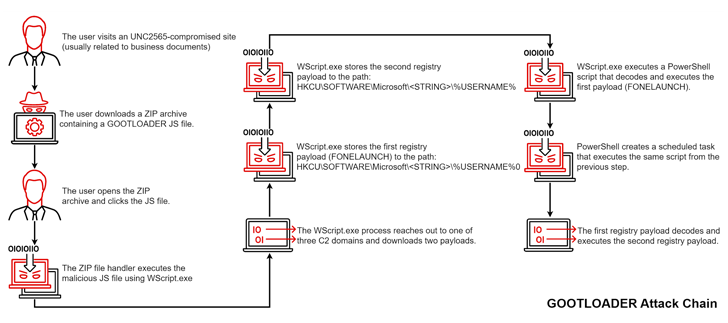
Although the overarching goals of Gootkit have remained unchanged, the attack sequence in by itself has acquired sizeable updates, whereby the JavaScript file in the ZIP archive is trojanized and is made up of yet another obfuscated JavaScript file that consequently proceeds to execute the malware.
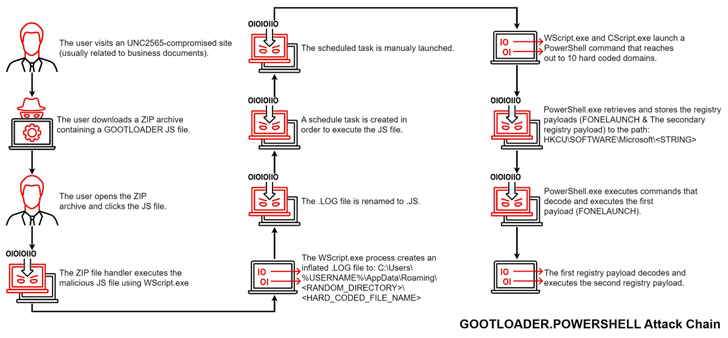
The new variant, which was spotted by the danger intelligence firm in November 2022, is remaining tracked as GOOTLOADER.POWERSHELL. It can be value noting that the revamped an infection chain was also documented by Craze Micro previously this month, detailing Gootkit attacks concentrating on the Australian health care sector.
What is actually extra, the malware authors are said to have taken 3 distinct strategies to obscure Gootkit, which includes concealing the code within just altered versions of respectable JavaScript libraries this sort of as jQuery, Chroma.js, and Underscore.js, in an attempt to escape detection.
It can be not just Gootkit, as 3 diverse flavors of FONELAUNCH – FONELAUNCH.FAX, FONELAUNCH.PHONE, and FONELAUNCH.DIALTONE – have been set to use by UNC2565 given that Might 2021 to execute DLLs, .NET binaries, and PE documents, indicating that the malware arsenal is remaining consistently maintained and updated.
“These modifications are illustrative of UNC2565’s energetic enhancement and progress in capabilities,” Mandiant scientists Govand Sinjari and Andy Morales reported.
Discovered this posting exciting? Abide by us on Twitter and LinkedIn to read through more distinctive content we write-up.
Some pieces of this post are sourced from:
thehackernews.com


 Microsoft Urges Customers to Secure On-Premises Exchange Servers
Microsoft Urges Customers to Secure On-Premises Exchange Servers