Researchers are warning about a spike in exploitation makes an attempt weaponizing a critical remote code execution flaw in Realtek Jungle SDK considering that the commence of August 2022.
According to Palo Alto Networks Device 42, the ongoing marketing campaign is explained to have recorded 134 million exploit tries as of December 2022, with 97% of the attacks developing in the earlier 4 months.
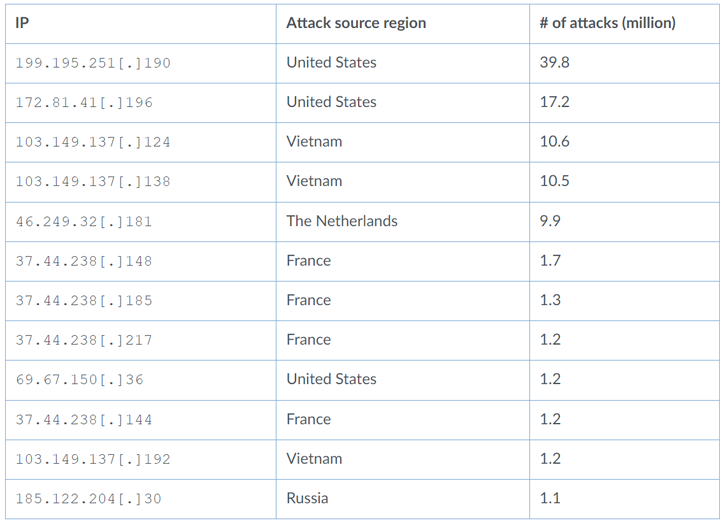
Shut to 50% of the attacks originated from the U.S. (48.3%), followed by Vietnam (17.8%), Russia (14.6%), The Netherlands (7.4%), France (6.4%), Germany (2.3%, and Luxembourg (1.6%).

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
What is more, 95% of the attacks leveraging the security shortcoming that emanated from Russia singled out organizations in Australia.
“Quite a few of the attacks we observed tried to deliver malware to infect susceptible IoT devices,” Device 42 researchers mentioned in a report, adding “danger teams are making use of this vulnerability to carry out huge-scale attacks on sensible equipment around the planet.”
The vulnerability in query is CVE-2021-35394 (CVSS score: 9.8), a established of buffer overflows and an arbitrary command injection bug that could be weaponized to execute arbitrary code with the best amount of privilege and acquire more than afflicted appliances.
The issues had been disclosed by ONEKEY (beforehand IoT Inspector) in August 2021. The vulnerability impacts a large vary of units from D-Website link, LG, Belkin, Belkin, ASUS, and NETGEAR.
Device 42 mentioned it found out 3 distinct forms of payloads distributed as a result of in-the-wild exploitation of the flaw –
- A script executes a shell command on the specific server to obtain more malware
- An injected command that writes a binary payload to a file and executes it, and
- An injected command that straight reboots the qualified server to cause a denial-of-service (DoS) ailment
Also sent by way of the abuse of CVE-2021-35394 are recognized botnets like Mirai, Gafgyt, and Mozi, as very well as a new Golang-centered dispersed denial-of-assistance (DDoS) botnet dubbed RedGoBot.
1st observed in September 2022, the RedGoBot marketing campaign entails dropping a shell script which is designed to down load a range of botnet consumers tailor-made to distinctive CPU architectures. The malware, when released, is equipped to run working procedure instructions and mount DDoS attacks.
The findings after all over again underscore the significance of updating software package in a well timed manner to avoid publicity to likely threats.
“The surge of attacks leveraging CVE-2021-35394 reveals that danger actors are pretty intrigued in source chain vulnerabilities, which can be tough for the regular user to determine and remediate,” the scientists concluded. “These issues can make it hard for the influenced person to discover the specific downstream solutions that are currently being exploited.”
Located this posting intriguing? Abide by us on Twitter and LinkedIn to browse a lot more unique written content we put up.
Some pieces of this post are sourced from:
thehackernews.com


 Gootkit Malware Continues to Evolve with New Components and Obfuscations
Gootkit Malware Continues to Evolve with New Components and Obfuscations