Microsoft on Tuesday disclosed that a large-scale phishing campaign specific in excess of 10,000 organizations because September 2021 by hijacking Office environment 365’s authentication method even on accounts secured with multi-factor authentication (MFA).
“The attackers then employed the stolen qualifications and session cookies to accessibility afflicted users’ mailboxes and perform stick to-on business email compromise (BEC) strategies in opposition to other targets,” the company’s cybersecurity teams noted.
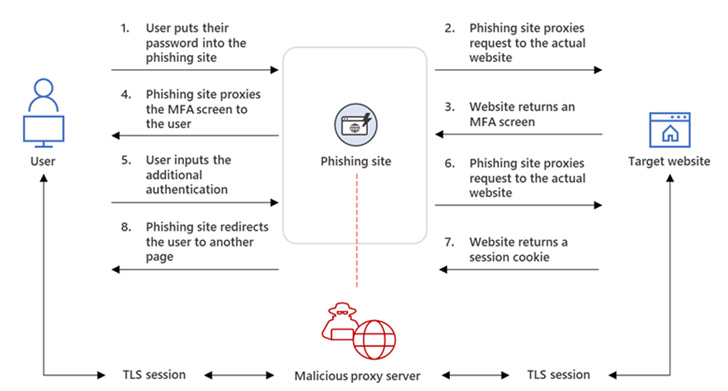
The intrusions entailed placing up adversary-in-the-middle (AitM) phishing web sites, whereby the attacker deploys a proxy server between a opportunity sufferer and the targeted web site so that recipients of a phishing email are redirected to lookalike landing webpages created to capture credentials and MFA facts.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“The phishing web page has two distinct Transportation Layer Security (TLS) sessions — a person with the goal and another with the precise web site the target would like to access,” the company discussed.
“These classes imply that the phishing site nearly functions as an AitM agent, intercepting the total authentication approach and extracting precious knowledge from the HTTP requests these kinds of as passwords and, more importantly, session cookies.”
Once in possession of this data, the attackers injected the cookies into their very own browsers to circumvent the authentication approach, irrespective of regardless of whether the victim had enabled MFA protections.
“The session cookie is proof for the web server that the person has been authenticated and has an ongoing session on the website,” Microsoft defined. “In AitM phishing, an attacker makes an attempt to acquire a focus on user’s session cookie so they can skip the total authentication approach and act on the latter’s behalf.”
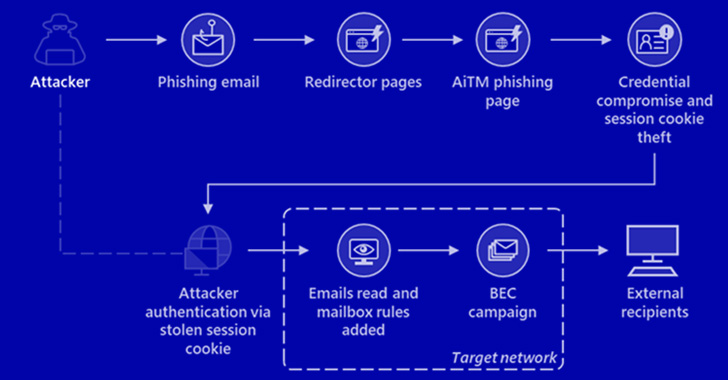
The phishing marketing campaign spotted by Microsoft was orchestrated to single out Office 365 customers by spoofing the Office on the net authentication web page, with the actors employing the Evilginx2 phishing package for carrying out the AitM attacks.
This included sending email messages containing voice message-themed lures that have been marked with large importance, tricking the recipients into opening malware-laced HTML attachments that redirected to the credential-thieving landing web pages.
To complete the ruse, the end users have been eventually routed to the authentic office environment[.]com web-site article-authentication, but not prior to the attackers leveraged the aforementioned AitM technique to siphon the session cookies and get hold of handle more than the compromised account.
The attacks didn’t conclude there, for the danger actors abused their mailbox accessibility to complete payment fraud by applying a strategy named email thread hijacking to dupe functions on the other finish of the dialogue to illicitly wire resources to accounts below their handle.
To further more mask their communications with the fraud target, the risk actors also created mailbox principles that mechanically moved every single incoming email containing the pertinent domain title to the “Archive” folder and marked it as “read through.”

“It took as minimal time as 5 minutes soon after credential and session theft for an attacker to launch their adhere to-on payment fraud,” Microsoft famous.
The attackers are claimed to have employed Outlook Web Entry (OWA) on a Chrome browser to perform the fraudulent things to do, although also deleting from the account’s Inbox folder the authentic phishing email as well as the follow-on communications with the goal from equally the Archive and Despatched Objects folders to erase traces.
“This AiTM phishing campaign is an additional instance of how threats continue to evolve in reaction to the security steps and policies companies place in put to defend by themselves in opposition to potential attacks,” the researchers reported.
“Even though AiTM phishing attempts to circumvent MFA, it really is crucial to underscore that MFA implementation continues to be an necessary pillar in id security. MFA is however very efficient at halting a broad variety of threats its performance is why AiTM phishing emerged in the first position.”
The findings appear as a group of researchers from Stony Brook College and Palo Alto Networks demonstrated late past calendar year a new fingerprinting approach that will make it attainable to discover AitM phishing kits in the wild making use of a resource identified as PHOCA.
“Attacks like this are turning into more typical as companies and people help multi-factor authentication (MFA) on accounts in order to superior protected them,” Erich Kron, security recognition advocate at KnowBe4, said in a assertion.
“To defend in opposition to the phishing e-mail that trick the victims into clicking on a url, companies should educate staff members how to discover and report phishing and must examination them regularly with simulated phishing attacks that permit them to exercise these techniques. In addition, educating people on how to detect phony login web pages will drastically minimize the risk of supplying up the qualifications and session cookies.”
Observed this write-up exciting? Adhere to THN on Facebook, Twitter and LinkedIn to examine additional exclusive content we put up.
Some parts of this write-up are sourced from:
thehackernews.com

 5 Questions You Need to Ask About Your Firewall Security
5 Questions You Need to Ask About Your Firewall Security