North Korean danger actors are actively exploiting a critical security flaw in JetBrains TeamCity to opportunistically breach vulnerable servers, in accordance to Microsoft.
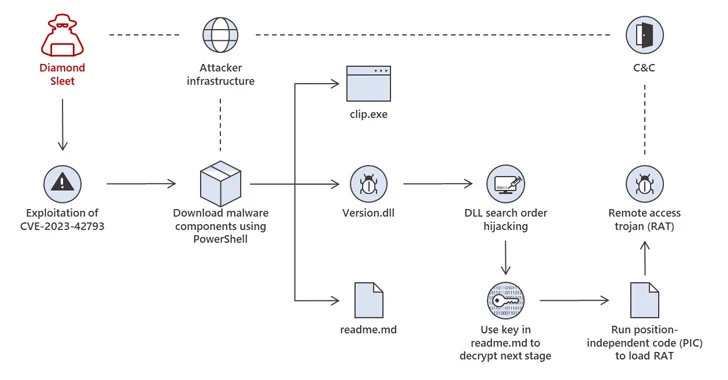
The attacks, which entail the exploitation of CVE-2023-42793 (CVSS rating: 9.8), have been attributed to Diamond Sleet (aka Labyrinth Chollima) and Onyx Sleet (aka Andariel or Silent Chollima).
It’s really worth noting that each the risk action clusters are element of the infamous North Korean country-condition actor known as Lazarus Team.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
In one particular of the two attack paths utilized by Diamond Sleet, a effective compromise of TeamCity servers is followed by the deployment of a recognised implant called ForestTiger from genuine infrastructure earlier compromised by the risk actor.
A 2nd variant of the attacks leverages the initial foothold to retrieve a destructive DLL (DSROLE.dll aka RollSling or Variation.dll or FeedLoad) that is loaded by signifies of a technique referred to as DLL research-order hijacking to both execute a upcoming-stage payload or a distant entry trojan (RAT).

Microsoft said it witnessed the adversary leveraging a mixture of instruments and approaches from the two attack sequences in sure occasions.
The intrusions mounted by Onyx Sleet, on the other hand, use the entry afforded by the exploitation of the JetBrains TeamCity bug to produce a new user account named krtbgt that is very likely supposed to impersonate the Kerberos Ticket Granting Ticket.
“Immediately after developing the account, the threat actor provides it to the Local Directors Team as a result of net use,” Microsoft stated. “The menace actor also operates various technique discovery commands on compromised units.”
The attacks subsequently guide to the deployment of a custom made proxy software dubbed HazyLoad that helps set up a persistent link in between the compromised host and attacker-controlled infrastructure.
An additional noteworthy put up-compromise action is the use of the attacker-controlled krtbgt account to indication into the compromised gadget through remote desktop protocol (RDP) and terminating the TeamCity services in a bid to protect against accessibility by other menace actors.
More than the many years, the Lazarus group has proven alone as one particular of the most pernicious and complex advanced persistent threat (APT) groups currently active, orchestrating financial crime and espionage attacks in equal measure via cryptocurrency heists and source chain attacks.
“We unquestionably believe that that North Korean hacking of cryptocurrency around infrastructure, all around the world – together with in Singapore, Vietnam, and Hong Kong – is a big resource of revenue for the regime that’s utilized to finance the advancing of the missile application and the considerably better amount of launches we have found in the previous calendar year,” U.S. Deputy National Security Advisor, Anne Neuberger, stated.
The progress will come as the AhnLab Security Emergency Reaction Centre (ASEC) detailed the Lazarus Group’s use of malware families this kind of as Volgmer and Scout that act as a conduit for serving backdoors for managing the infected systems.

“The Lazarus group is one particular of the pretty perilous teams that are extremely active throughout the world, utilizing various attack vectors such as spear-phishing and provide chain attacks,” the South Korean cybersecurity agency mentioned, implicating the hacking crew to yet another campaign codenamed Operation Aspiration Magic.
This will involve mounting watering hole attacks by inserting a rogue url within a certain write-up on an unspecified news web page that weaponizes security flaws in INISAFE and MagicLine goods to activate the bacterial infections, a tactic beforehand affiliated with the Lazarus Group.
In a additional signal of North Korea’s evolving offensive programs, ASEC has attributed a further risk actor regarded as Kimsuky (aka APT43) to a fresh new established of spear-phishing attacks that make the most of the BabyShark malware to install a motley slate of remote desktop instruments and VNC software (i.e., TightVNC and TinyNuke) to commandeer victim devices and exfiltrate details.
Discovered this short article appealing? Observe us on Twitter and LinkedIn to browse far more distinctive articles we article.
Some elements of this post are sourced from:
thehackernews.com

 Google TAG Detects State-Backed Threat Actors Exploiting WinRAR Flaw
Google TAG Detects State-Backed Threat Actors Exploiting WinRAR Flaw