A complex botnet identified as MyloBot has compromised hundreds of devices, with most of them situated in India, the U.S., Indonesia, and Iran.
Which is according to new results from BitSight, which explained it is “presently seeing extra than 50,000 exclusive infected systems each individual working day,” down from a high of 250,000 exclusive hosts in 2020.
Furthermore, an evaluation of MyloBot’s infrastructure has identified connections to a residential proxy provider known as BHProxies, indicating that the compromised equipment are being utilised by the latter.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
MyloBot, which emerged on the threat landscape in 2017, was to start with documented by Deep Instinct in 2018, calling out its anti-examination approaches and its skill to purpose as a downloader.
“What helps make Mylobot risky is its capability to down load and execute any kind of payload after it infects a host,” Lumen’s Black Lotus Labs claimed in November 2018. “This usually means at any time it could download any other kind of malware the attacker wishes.”
Past yr, the malware was observed sending extortion e-mail from hacked endpoints as aspect of a financially enthusiastic campaign searching for around $2,700 in Bitcoin.
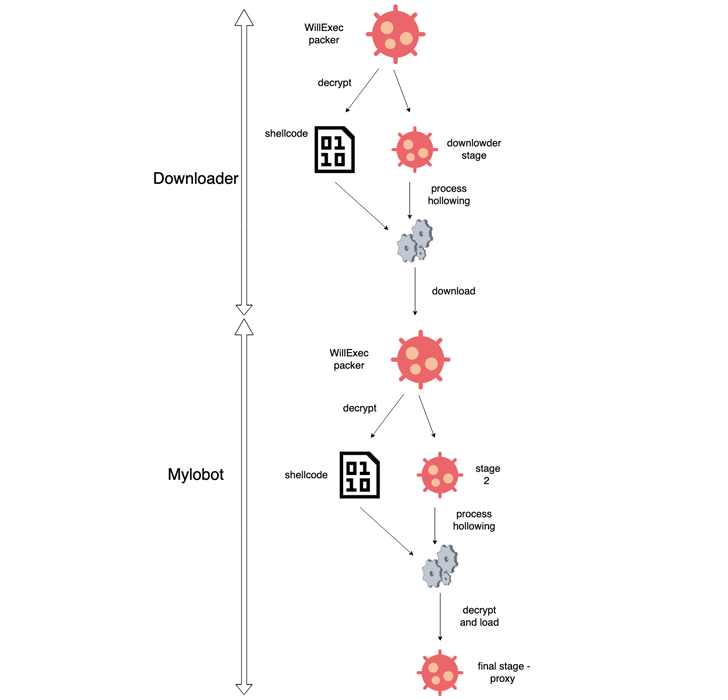
MyloBot is known to utilize a multi-stage sequence to unpack and start the bot malware. Notably, it also sits idle for 14 days prior to trying to get hold of the command-and-handle (C2) server to sidestep detection.
The primary purpose of the botnet is to set up a connection to a difficult-coded C2 area embedded inside the malware and await even more recommendations.
“When Mylobot receives an instruction from the C2, it transforms the infected laptop into a proxy,” BitSight said. “The contaminated equipment will be ready to deal with a lot of connections and relay website traffic despatched by the command-and-handle server.”
Subsequent iterations of the malware have leveraged a downloader that, in switch, contacts a C2 server, which responds with an encrypted information that contains a hyperlink to retrieve the MyloBot payload.
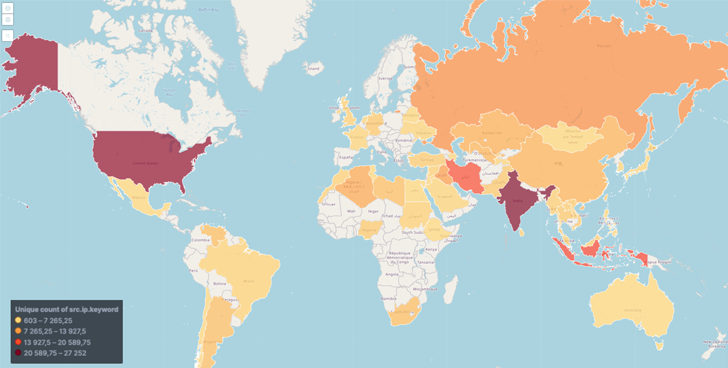
The proof that MyloBot could be a part of a little something even larger stems from a reverse DNS lookup of a person of the IP addresses affiliated with the botnet’s C2 infrastructure has unveiled ties to a domain named “shoppers.bhproxies[.]com.”
The Boston-centered cybersecurity firm said it started sinkholing MyloBot in November 2018 and that it proceeds to see the botnet evolve about time.
Observed this report appealing? Stick to us on Twitter and LinkedIn to read a lot more exceptional information we write-up.
Some sections of this short article are sourced from:
thehackernews.com

 The Future of Network Security: Predictive Analytics and ML-Driven Solutions
The Future of Network Security: Predictive Analytics and ML-Driven Solutions