The sudden fall in destructive action connected with the Mozi botnet in August 2023 was because of to a destroy change that was dispersed to the bots.
“1st, the drop manifested in India on August 8,” ESET reported in an assessment published this 7 days. “A week afterwards, on August 16, the identical thing took place in China. Whilst the mysterious management payload – aka eliminate switch – stripped Mozi bots of most operation, they preserved persistence.”
Mozi is an Internet of Points (IoT) botnet that emerged from the resource code of a number of known malware family members, this sort of as Gafgyt, Mirai, and IoT Reaper. Very first spotted in 2019, it can be regarded to exploit weak and default distant accessibility passwords as effectively as unpatched security vulnerabilities for initial obtain.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

In September 2021, cybersecurity agency Netlab scientists disclosed the arrest of the botnet operators by Chinese authorities.
But the precipitous drop in Mozi activity – from all over 13,300 hosts on August 7 to 3,500 on August 10 – is said to be the consequence of an not known actor transmitting a command instructing the bots to down load and set up an update designed to neutralize the malware.
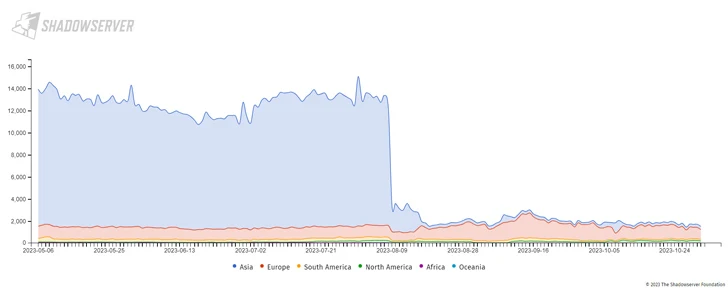 Shadowserver Foundation
Shadowserver Foundation
Especially, the destroy change demonstrated abilities to terminate the malware’s system, disable system expert services these as SSHD and Dropbear, and in the end switch Mozi with itself.
“Regardless of the drastic reduction in functionality, Mozi bots have taken care of persistence, indicating a deliberate and calculated takedown,” security researchers Ivan Bešina, Michal Škuta, and Miloš Čermák said.

A 2nd variant of the management payload came fitted with small modifications, together with a characteristic to ping a distant server, probably for statistical uses. What is extra, the get rid of swap reveals a robust overlap with the botnet’s initial source code and is signed with the suitable non-public essential,
“There are two probable instigators for this takedown: the initial Mozi botnet creator or Chinese legislation enforcement, maybe enlisting or forcing the cooperation of the original actor or actors,” Bešina explained.
“The sequential focusing on of India and then China suggests that the takedown was carried out deliberately, with 1 nation targeted first and the other a 7 days later on.”
Found this write-up fascinating? Adhere to us on Twitter and LinkedIn to read through additional exceptional content we submit.
Some pieces of this report are sourced from:
thehackernews.com


 SaaS Security is Now Accessible and Affordable to All
SaaS Security is Now Accessible and Affordable to All