This new product features SaaS discovery and risk assessment coupled with a totally free user obtain assessment in a one of a kind “freemium” model
Securing employees’ SaaS use is turning out to be more and more very important for most cloud-based mostly organizations. Though various equipment are available to deal with this want, they typically employ distinctive methods and technologies, main to needless confusion and complexity. Enter Wing Security’s new “Necessary SSPM” (SaaS Security Posture Administration) instrument, which aims to simplify the course of action of securing SaaS usage across the corporation. Its business enterprise approach is simple: self-onboard, attempt the product, and if amazed, upgrade to unlock extra crucial security abilities.
What is actually vital SaaS security?
According to Wing, 3 simple however basic abilities are essential for businesses aiming to protected their SaaS: discovery, evaluation, and management. These align with regulatory security standards these types of as ISO 27001 and SOC, which emphasize vendor and third-party risk assessment programs, as perfectly as controlling user accessibility to critical organization equipment.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
1. Uncover: You are unable to safe what you are unable to see
Shadow IT is not a novel issue but somewhat an evolving one particular. With the continuous boost in SaaS use and the skill for users to bypass security policies like MFA and SSO when onboarding SaaS purposes, the new deal with of shadow IT is SaaS-dependent. The process is uncomplicated: staff require to total a business task and typically involve a software to facilitate it. They search for a alternative on-line, utilizing business qualifications to log in, significantly when most products and services you should not have to have credit history card information to get started. SaaS, staying the modern source chain, obviously needs a security alternative because of to its decentralized and ungoverned character.
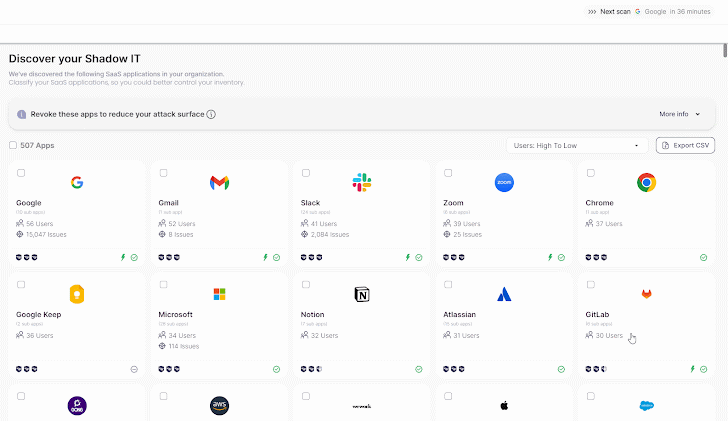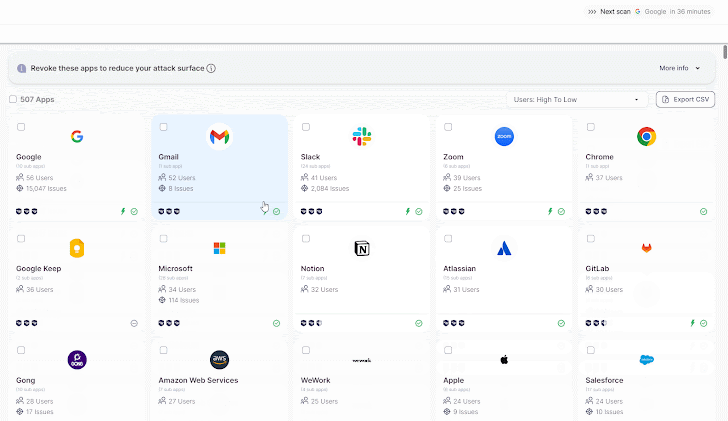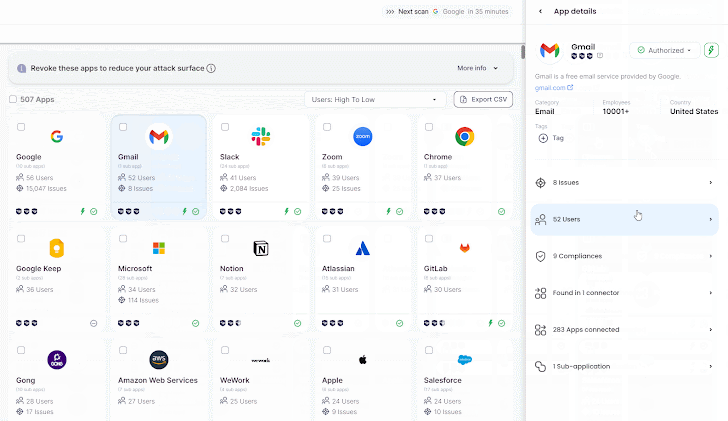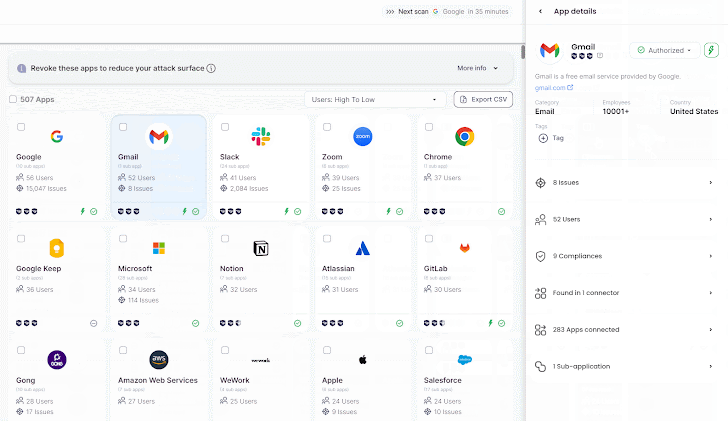 Wing’s SaaS discovery
Wing’s SaaS discovery
2. Assess risk: Not all threats are equivalent, save useful time
The moment the shadow ingredient is settled, corporations are still left with an substantial list of apps, often numbering in the countless numbers. This begs the problem: what now? Without having an automatic method for evaluating the pitfalls linked with all the SaaS purposes joined to the corporation, uncovering shadow SaaS can be additional baffling and burdensome than practical. This highlights the value of examining the security status of these applications and analyzing a threshold that demands attention.
SaaS discovery need to go hand in hand with some degree of vendor or 3rd-party risk assessment. Wing’s new products tier brings together SaaS discovery with an automated processes for determining an application’s SaaS security score. This risk information is extracted from a broad SaaS database of around 280,000 SaaS on history, cross-checked with the facts from hundreds of Wing’s consumers and their SaaS environments. Shelling out consumers benefit from broader and further SaaS risk assessments, like around-actual-time threat intelligence alerts.
3. Management: Ensure end users only have necessary access
Exploring all SaaS in use (and not in use) and knowledge their pitfalls is only 50 % the fight the other 50 % will involve SaaS consumers. They grant purposes obtain and permissions to organization knowledge, making possibilities concerning read through/publish permissions for the quite a few apps they use. On average, every personnel utilizes 28 SaaS purposes at any provided time, which translates to hundreds, if not 1000’s, of SaaS purposes with entry to business data.
Conducting periodic person accessibility testimonials throughout necessary organization programs is not just a regulatory requirement but also hugely advised for sustaining a protected posture. Controlling who has accessibility to which software can reduce delicate information from slipping into the improper palms and significantly lessen the potential attack surface, as personnel are generally the initially targets for malicious actors. A very long list of people and their permissions and roles throughout a variety of applications can be too much to handle, which is why Wing aids in prioritizing end users centered on their permissions, their roles and by encouraging the minimum privilege thought. This ensures that all people, besides authorised admins, have only basic obtain to SaaS purposes.
 Wing’s Person Accessibility Evaluate
Wing’s Person Accessibility Evaluate
In summary – These 3 abilities are vital for setting up a correct SaaS security method, but they do not warranty entire coverage or handle. Mature security organizations will have to have extra. Info security characteristics, automatic remediation paths and extra management around consumer privileges and behaviors are only achievable with Wing’s comprehensive remedy. That mentioned, these are an essential setting up place for those people organizations who don’t still have SaaS security in place or are thinking about which instruments and methods to get begun with.
How is this various from a POC or interactive demo?
This new “test 1st, pay out later on” technique differs from the average POC primarily in its completely no-contact nature. Users can self-onboard the item by agreeing to Wing’s authorized conditions, without having the require to interact with a human agent or sales personnel, except they decide on to. When the free merchandise is deliberately limited in functions and capabilities, it offers a starting off point for people curious about or in search of SaaS security. In contrast to on-line demos, this system entails the genuine processing of your data and can genuinely increase your security posture by supplying visibility into your company’s actual SaaS utilization and by enabling you to assess the magnitude of your SaaS attack surface. A freemium method in security-similar merchandise is uncommon, making this an option for all those who wish to take a look at the item prior to committing.
Found this post interesting? Follow us on Twitter and LinkedIn to study a lot more distinctive written content we put up.
Some sections of this report are sourced from:
thehackernews.com


 Iran’s MuddyWater Targets Israel in New Spear-Phishing Cyber Campaign
Iran’s MuddyWater Targets Israel in New Spear-Phishing Cyber Campaign