The Iranian nation-condition actor known as MuddyWater has been joined to a new spear-phishing campaign targeting two Israeli entities to eventually deploy a legitimate remote administration tool from N-capable referred to as Innovative Checking Agent.
Cybersecurity firm Deep Instinct, which disclosed facts of the attacks, said the marketing campaign “exhibits updated TTPs to formerly documented MuddyWater activity,” which has, in the earlier, utilised identical attack chains to distribute other remote accessibility applications like ScreenConnect, RemoteUtilities, Syncro, and SimpleHelp.
When the hottest enhancement marks the first time MuddyWater has been noticed working with N-able’s distant checking program, it also underscores the truth that the largely unchanged modus operandi carries on to produce some degree of achievements to the threat actor.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The findings have also been independently verified by cybersecurity company Team-IB in a write-up shared on X (formerly Twitter).
The point out-sponsored team is a cyber espionage crew that is reported to be a subordinate ingredient inside of Iran’s Ministry of Intelligence and Security (MOIS), becoming a member of other MOIS-affiliated clusters like OilRig, Lyceum, Agrius, and Scarred Manticore. It has been lively considering that at least 2017.
Prior attack sequences have entailed sending spear-phishing e-mails with immediate inbound links as properly as HTML, PDF, and RTF attachments made up of hyperlinks to archives hosted on various file-sharing platforms that eventually fall a person of the aforementioned remote administration tools.
The latest methods and instruments symbolize in some means a continuation, and in other ways an evolution, for the group variously recognized as Mango Sandstorm and Static Kitten.
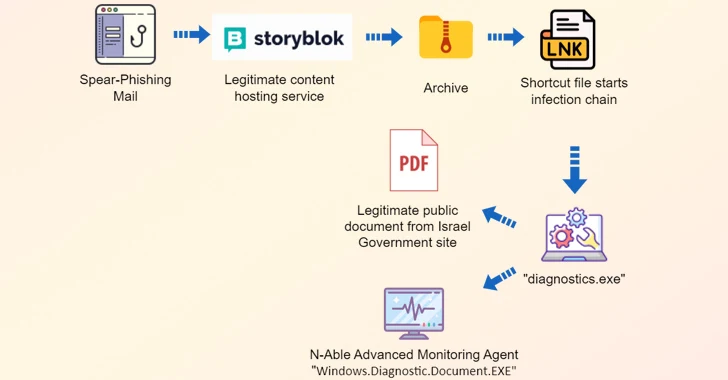
What’s different this time all around is the use of a new file-sharing services identified as Storyblok to initiate a multi-phase an infection vector.
“It consists of hidden documents, an LNK file that initiates the infection, and an executable file built to unhide a decoy doc while executing Advanced Monitoring Agent, a remote administration instrument,” security researcher Simon Kenin reported in a Wednesday examination.

“Immediately after the target has been infected, the MuddyWater operator will link to the infected host applying the legit distant administration software and will get started doing reconnaissance on the focus on.”
The lure doc exhibited to the target is an official memo from the Israeli Civil Services Commission, which can be publicly downloaded from its formal internet site.
In a additional sign of Iran’s quickly increasing malicious cyber abilities, Deep Instinct reported it also noticed the MuddyWater actors leveraging a new command-and-handle (C2) framework termed MuddyC2Go, a successor to MuddyC3 and PhonyC2.
Found this article attention-grabbing? Comply with us on Twitter and LinkedIn to read through more unique content we write-up.
Some elements of this posting are sourced from:
thehackernews.com

 Researchers Find 34 Windows Drivers Vulnerable to Full Device Takeover
Researchers Find 34 Windows Drivers Vulnerable to Full Device Takeover