The North Korea-joined threat actor acknowledged as Kimsuky (aka Black Banshee, Emerald Sleet, or Springtail) has been observed shifting its tactics, leveraging Compiled HTML Assistance (CHM) information as vectors to supply malware for harvesting sensitive info.
Kimsuky, lively because at the very least 2012, is identified to target entities found in South Korea as very well as North The usa, Asia, and Europe.
According to Rapid7, attack chains have leveraged weaponized Microsoft Place of work paperwork, ISO documents, and Windows shortcut (LNK) data files, with the team also using CHM data files to deploy malware on compromised hosts.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The cybersecurity business has attributed the activity to Kimsuky with reasonable confidence, citing comparable tradecraft noticed in the earlier.

“When initially made for aid documentation, CHM information have also been exploited for malicious applications, these kinds of as distributing malware, since they can execute JavaScript when opened,” the enterprise mentioned.
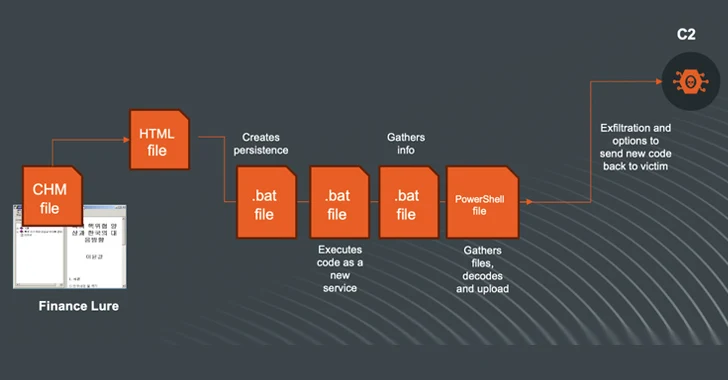
The CHM file is propagated within an ISO, VHD, ZIP, or RAR file, opening which executes a Visual Simple Script (VBScript) to set up persistence and attain out to a distant server to fetch a next-stage payload dependable for accumulating and exfiltrating sensitive data.
Swift7 described the attacks as ongoing and evolving, concentrating on companies based in South Korea. It also recognized an alternate infection sequence that employs a CHM file as a starting up place to drop batch information tasked with harvesting the details and a PowerShell script to hook up to the C2 server and transfer the data.
“The modus operandi and reusing of code and equipment are demonstrating that the risk actor is actively utilizing and refining/reshaping its methods and ways to assemble intelligence from victims,” it claimed.
The development comes as Broadcom-owned Symantec exposed that the Kimsuky actors are distributing malware impersonating an software from a reputable Korean general public entity.
“Once compromised, the dropper installs an Endoor backdoor malware,” Symantec mentioned. “This risk permits attackers to acquire delicate data from the sufferer or set up added malware.”
It’s really worth noting that the Golang-primarily based Endoor, along with Troll Stealer (aka TrollAgent), has been not too long ago deployed in relationship with cyber attacks that concentrate on end users downloading security courses from a Korean design-linked association’s web-site.

The findings also get there amid a probe initiated by the United Nations into 58 suspected cyber attacks carried out by North Korean nation-condition actors involving 2017 and 2023 that netted $3 billion in illegal revenues to assist it additional produce its nuclear weapons program.
“The high quantity of cyber attacks by hacking teams subordinate to the Reconnaissance Normal Bureau reportedly ongoing,” the report explained. “Trends incorporate concentrating on protection firms and supply chains and, more and more, sharing infrastructure and resources.”
The Reconnaissance General Bureau (RGB) is North Korea’s major overseas intelligence support, comprising the menace clusters extensively tracked as the Lazarus Group – and its subordinate features, Andariel and BlueNoroff – and Kimsuky.
“Kimsuky has proven curiosity in making use of generative synthetic intelligence, which include big language types, most likely for coding or composing phishing email messages,” the report more additional. “Kimsuky has been observed utilizing ChatGPT.”
Observed this posting fascinating? Adhere to us on Twitter and LinkedIn to go through much more exceptional articles we article.
Some elements of this report are sourced from:
thehackernews.com

 German Police Seize ‘Nemesis Market’ in Major International Darknet Raid
German Police Seize ‘Nemesis Market’ in Major International Darknet Raid