The North Korean state-sponsored menace actor known as Kimsuky has been found out using a new reconnaissance device known as ReconShark as aspect of an ongoing world campaign.
“[ReconShark] is actively delivered to particularly specific people today as a result of spear-phishing emails, OneDrive backlinks leading to document downloads, and the execution of malicious macros,” SentinelOne researchers Tom Hegel and Aleksandar Milenkoski mentioned.
Kimsuky is also known by the names APT43, ARCHIPELAGO, Black Banshee, Nickel Kimball, Emerald Sleet (beforehand Thallium), and Velvet Chollima.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Lively due to the fact at least 2012, the prolific menace actor has been linked to qualified attacks on non-governmental corporations (NGOs), think tanks, diplomatic agencies, navy corporations, financial groups, and study entities throughout North The united states, Asia, and Europe.

The hottest intrusion set documented by SentinelOne leverages geopolitical themes related to North Korea’s nuclear proliferation to activate the an infection sequence.
“Notably, the spear-phishing e-mails are designed with a degree of structure high quality tuned for particular people, increasing the chance of opening by the focus on,” the researchers said. “This features suitable formatting, grammar, and visual clues, appearing genuine to unsuspecting end users.”
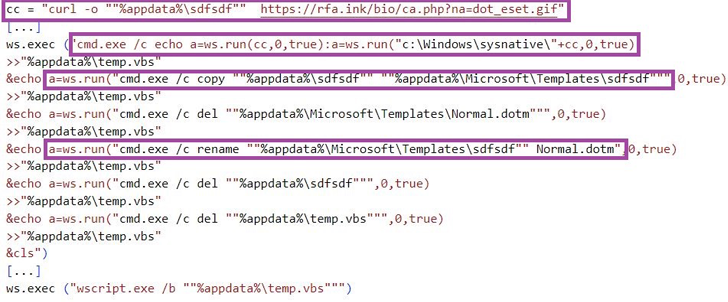
These messages incorporate links to booby-trapped Microsoft Term paperwork hosted on OneDrive to deploy ReconShark, which mainly capabilities as a recon device to execute directions despatched from an actor-managed server. It is also an evolution of the menace actor’s BabyShark malware toolset.
“It exfiltrates process info to C2 server, maintains persistence on the procedure, and waits for further instruction from the operator,” Palo Alto Networks Device 42 mentioned in its evaluation of BabyShark in February 2019.
Upcoming WEBINARLearn to Cease Ransomware with Authentic-Time Defense
Be part of our webinar and discover how to quit ransomware attacks in their tracks with true-time MFA and services account protection.
Preserve My Seat!
ReconShark is particularly developed to exfiltrate aspects about operating procedures, deployed detection mechanisms and components facts, suggesting that information collected from the resource is made use of to carry out “precision attacks” involving malware tailored to the qualified natural environment in a fashion that sidesteps detection.
The malware is also able of deploying added payloads from the server centered on “what detection system processes run on infected machines.”
The conclusions include to developing evidence that the menace actor is actively shifting its methods to get a foothold on compromised hosts, create persistence, and stealthily get intelligence for prolonged periods of time.
“The ongoing attacks from Kimsuky and their use of the new reconnaissance tool, ReconShark, spotlight the evolving character of the North Korean threat landscape,” SentinelOne reported.
Uncovered this write-up interesting? Adhere to us on Twitter and LinkedIn to read much more distinctive information we publish.
Some elements of this short article are sourced from:
thehackernews.com


 Lack of Visibility: The Challenge of Protecting Websites from Third-Party Scripts
Lack of Visibility: The Challenge of Protecting Websites from Third-Party Scripts