Italian company banking shoppers are the target of an ongoing fiscal fraud marketing campaign that has been leveraging a new web-inject toolkit called drIBAN considering the fact that at the very least 2019.
“The main purpose of drIBAN fraud operations is to infect Windows workstations inside of corporate environments making an attempt to alter legit banking transfers executed by the victims by altering the beneficiary and transferring revenue to an illegitimate lender account,” Cleafy scientists Federico Valentini and Alessandro Strino stated.
The financial institution accounts, per the Italian cybersecurity agency, are both managed by the risk actors on their own or their affiliate marketers, who are then tasked with laundering the stolen money.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The use of web injects is a time-tested tactic that tends to make it attainable for malware to inject customized scripts on the consumer facet by means of a male-in-the-browser (MitB) attack and intercept website traffic to and from the server.

The fraudulent transactions are frequently understood by usually means of a approach identified as Automatic Transfer Method (ATS) which is able of bypassing anti-fraud techniques place in place by banking institutions and initiating unauthorized wire transfers from a victim’s possess laptop or computer.
Over the years, the operators powering drIBAN have gotten more savvy at averting detection and acquiring efficient social engineering approaches, in addition to establishing a foothold for prolonged intervals in company lender networks.
Cleafy stated 2021 was the 12 months when the vintage “banking trojan” procedure progressed into an sophisticated persistent danger. Furthermore, there are indications that the exercise cluster overlaps with a 2018 campaign mounted by an actor tracked by Proofpoint as TA554 targeting users in Canada, Italy, and the U.K.
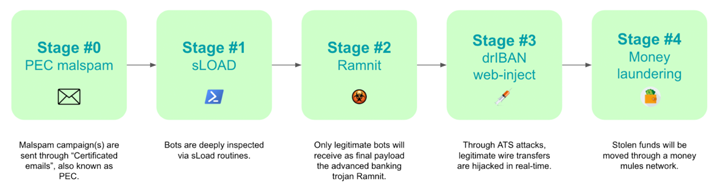
The attack chain commences with a qualified email (or PEC email) in an attempt to lull victims into a fake sense of security. These phishing e-mail arrive bearing an executable file that acts as a downloader for a malware termed sLoad (aka Starslord loader).
A PowerShell loader, sLoad is a reconnaissance device that collects and exfiltrates details from the compromised host, with the function of assessing the concentrate on and dropping a much more major payload like Ramnit if the target is considered worthwhile.
“This ‘enrichment phase’ could continue for days or weeks, depending on the quantity of contaminated devices,” Cleafy noted. “Further data will be exfiltrated to make the ensuing botnet much more and a lot more good and reliable.”
Approaching WEBINARLearn to End Ransomware with True-Time Security
Be a part of our webinar and master how to halt ransomware attacks in their tracks with real-time MFA and service account protection.
Help save My Seat!
sLoad also leverages living-off-the-land (LotL) strategies by abusing reputable Windows resources like PowerShell and BITSAdmin as aspect of its evasion mechanisms.
A further characteristic of the malware is its skill to check from a predefined list of corporate banking establishments to decide if the hacked workstation is a person between the targets, and if so, commence with the infection.
“All the bots that properly pass those people measures will be chosen by botnet operators and regarded as ‘new candidates’ for banking fraud operations moving forward to the up coming stage, in which Ramnit, one particular of the most superior banking trojans, will be set up,” the scientists explained.
Found this post exciting? Follow us on Twitter and LinkedIn to study additional unique information we post.
Some sections of this report are sourced from:
thehackernews.com


 N. Korean Kimsuky Hackers Using New Recon Tool ReconShark in Latest Cyberattacks
N. Korean Kimsuky Hackers Using New Recon Tool ReconShark in Latest Cyberattacks