Various sectors in East Asian marketplaces have been subjected to a new email phishing campaign that distributes a previously undocumented strain of Android malware named FluHorse that abuses the Flutter application development framework.
“The malware attributes a number of destructive Android applications that mimic legitimate apps, most of which have additional than 1,000,000 installs,” Examine Position said in a complex report. “These malicious applications steal the victims’ qualifications and two-factor authentication (2FA) codes.”
The malicious applications have been uncovered to imitate applications like Etcetera and VPBank Neo, which are utilized in Taiwan and Vietnam. Evidence collected so much reveals that the action has been energetic because at least Could 2022.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The phishing plan in by itself is rather uncomplicated, wherein victims are lured with e-mails that contain inbound links to a bogus web-site that hosts destructive APK information. Also additional to the web page are checks that intention to monitor victims and produce the application only if their browser User-Agent string matches that of Android.
At the time put in, the malware requests for SMS permissions and prompts the user to input their qualifications and credit history card info, all of which is subsequently exfiltrated to a distant server in the history when the victim is questioned to wait around for a number of minutes.
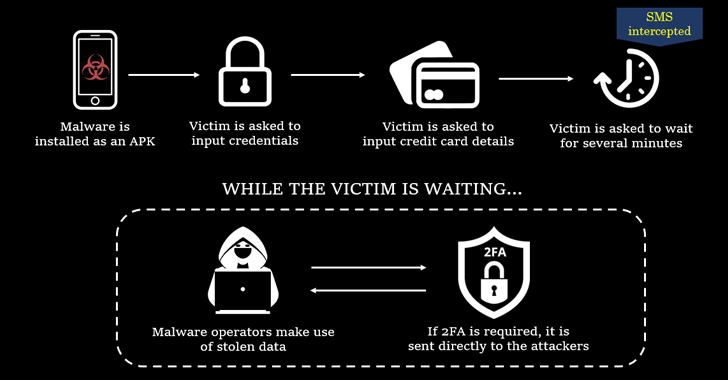
The threat actors also abuse their obtain to SMS messages to intercept all incoming 2FA codes and redirect them to the command-and-manage server.
The Israeli cybersecurity business explained it also recognized a courting app that redirected Chinese-speaking buyers to rogue landing webpages that are developed to capture credit score card information.
Approaching WEBINARLearn to Prevent Ransomware with True-Time Protection
Join our webinar and learn how to prevent ransomware attacks in their tracks with actual-time MFA and provider account defense.
Conserve My Seat!
Interestingly, the malicious features is carried out with Flutter, an open up resource UI software program enhancement package that can be made use of to develop cross-platform applications from a one codebase.
While risk actors are recognized to use a variety of tricks like evasion methods, obfuscation, and very long delays right before execution to resist evaluation and get all-around virtual environments, the use of Flutter marks a new level of sophistication.
“The malware developers did not set a lot hard work into the programming, instead relying on Flutter as a establishing platform,” the researchers concluded.
“This solution authorized them to create dangerous and generally undetected malicious apps. 1 of the rewards of using Flutter is that its really hard-to-review character renders quite a few modern day security remedies worthless.”
Discovered this short article attention-grabbing? Comply with us on Twitter and LinkedIn to browse far more distinctive information we put up.
Some sections of this report are sourced from:
thehackernews.com


 Hackers Targeting Italian Corporate Banking Clients with New Web-Inject Toolkit DrIBAN
Hackers Targeting Italian Corporate Banking Clients with New Web-Inject Toolkit DrIBAN