Cybersecurity scientists have documented a novel article-exploit persistence approach on iOS 16 that could be abused to fly less than the radar and main entry to an Apple gadget even when the target thinks it is offline.
The system “tips the target into thinking their device’s Plane Method functions when in reality the attacker (pursuing effective product exploit) has planted an artificial Plane Manner which edits the UI to show Airplane Mode icon and cuts internet connection to all apps except the attacker software,” Jamf Threat Labs scientists Hu Ke and Nir Avraham stated in a report shared with The Hacker News.
Airplane Manner, as the name implies, enables customers to flip off wireless characteristics in their products, properly blocking them from connecting to Wi-Fi networks, mobile data, and Bluetooth as very well as sending or getting calls and text messages.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The solution devised by Jamf, in a nutshell, offers an illusion to the user that the Plane Mode is on although enabling a destructive actor to stealthily maintain a mobile network connection for a rogue application.
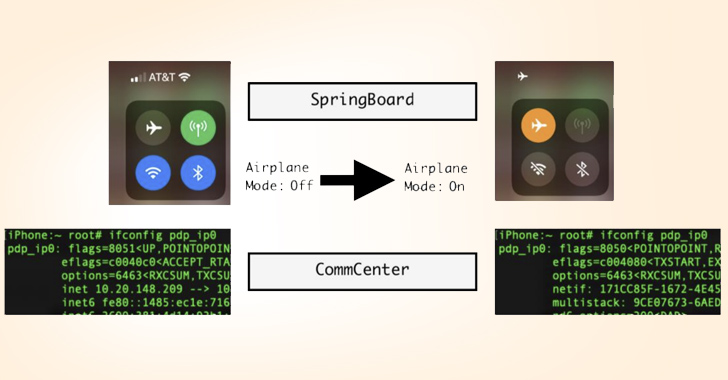
“When the user turns on Airplane Manner, the network interface pdp_ip0 (mobile information) will no extended show ipv4/ipv6 ip addresses,” the scientists explained. “The mobile network is disconnected and unusable, at the very least to the person place level.”
When the underlying improvements are carried out by CommCenter, the person interface (UI) modifications, these as the icon transitions are taken treatment of by the SpringBoard.
The goal of the attack, then, is to devise an synthetic Airplane Method that retains the UI changes intact but retains cellular connectivity for a destructive payload set up on the product by other suggests.
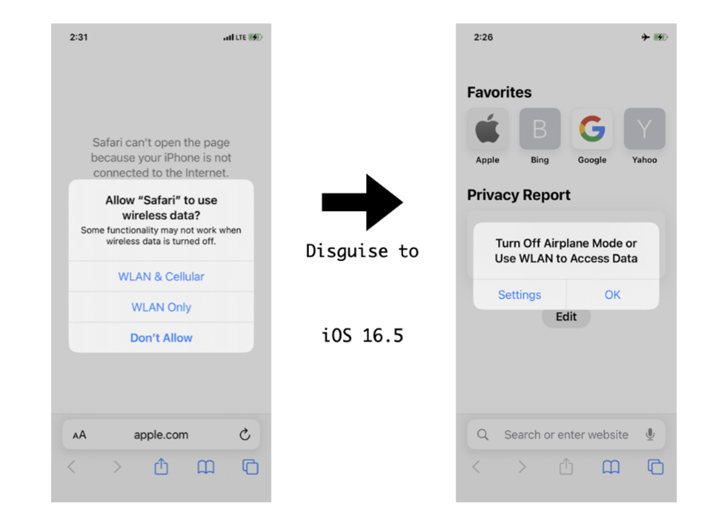
“Soon after enabling Plane Manner without the need of a Wi-Fi relationship, end users would count on that opening Safari would result in no link to the internet,” the researchers claimed. “The standard knowledge is a notification window that prompts a user to ‘Turn Off Plane Method.'”

To pull off the ruse, the CommCenter daemon is used to block cellular facts obtain for distinct applications and disguise it as Airplane Method by implies of a hooked operate that alters the inform window to seem like the placing has been turned on.
It really is really worth noting that the functioning method kernel notifies the CommCenter by way of a callback plan, which, in switch, notifies the SpringBoard to show the pop-up.
A nearer assessment of the CommCenter daemon has also exposed the existence of an SQL databases that’s utilized to document the cellular data access position of just about every application (aka bundle ID), with a flag established to the price “8” if an software is blocked from accessing it.
“Using this databases of mounted software bundle IDs we can now selectively block or permit an app to obtain Wi-Fi or cellular data utilizing the adhering to code,” the researchers claimed.
“When combined with the other methods outlined previously mentioned, the fake Plane Mode now seems to act just as the genuine just one, besides that the internet ban does not use to non-software processes this sort of as a backdoor trojan.”
Observed this short article interesting? Follow us on Twitter and LinkedIn to read through a lot more exclusive information we article.
Some parts of this post are sourced from:
thehackernews.com

 Why You Need Continuous Network Monitoring?
Why You Need Continuous Network Monitoring?