Improvements in the way we get the job done have had substantial implications for cybersecurity, not least in network monitoring. Staff no extended sit safely facet-by-facet on a company network, dev teams regularly spin up and tear down techniques, exposing solutions to the internet. Retaining monitor of these people, modifications and services is tough – internet-experiencing attack surfaces seldom continue to be the very same for prolonged.
But a secure operating network is the backbone of each and every fashionable company, and with so a lot of diverse attack vectors and entry points, relying on firewalls and point-in-time scanning is no for a longer time ample. You have to have to comprehend how your firewalls are currently being changed in true-time, with real-planet validation of how they are configured. You need ongoing network monitoring.
What demands defending in your network?
There is so a lot sprawl in present-day company networks with distant working, cloud computing and third-party integrations, that it really is no longer just the gadgets or systems that you have in your place of work and knowledge middle that need guarding.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
From the components and computer software of the network itself, to all the equipment made use of to obtain it, from IoT endpoints to laptops and smartphones, network security now requires to glimpse outside of the perimeter to your cloud sources, edge units, 3rd-party hosted information, integrations with other components or software program, and assets hosted in dispersed workplaces.
Just to complicate matters further more, some of these companies, especially individuals hosted in the cloud, may perhaps only be energetic for a brief house of time for specific jobs, occasions, deployments, or by style. With this sort of a dispersed network, the castle-and-moat product of network security is no longer fit for function.
What can go mistaken with your network?
Vulnerabilities can be launched to your network in a selection of methods, together with misconfigurations, expiring certificates, new property added to cloud environments, missing patches, or unnecessarily exposing expert services to the internet. In addition, there’s the ever-existing risk of attack from phishing, supply chain compromises and uncovered qualifications.
For case in point, a Windows SMB company on your internal network is not a vulnerability, but exposing just one to the internet is a diverse make any difference solely – which is what led to the WannaCry ransomware attack that distribute throughout the entire world. Equally, Australian telco Optus endured a devastating info breach in 2022 that uncovered specifics of 11 million shoppers. The breach occurred as a result of an unprotected and publicly-uncovered API which failed to need user authentication, so anyone that found out the API on the internet could join to it devoid of a username or password.
How can you guard your network?
Constant network checking supported by normal scanning could have picked up both of those of these vulnerabilities and prevented these breaches. Checking employs automation to detect and establish flaws and weak places in your equipment, application software package and working techniques. It does this by sending probes to glance for open ports and solutions, and the moment the list of companies is identified, probing each and every for much more data, configuration weaknesses or recognised vulnerabilities.
It can be typical to have a vary of programs in your network, from laptops and workstations in the business office or at household, to methods in cloud platforms like AWS, Azure, and Google Cloud. Your staff may properly use a range of functioning programs far too. Selecting what to include in your network scan can be really hard, but there are multiple ways to deal with it: exposure primarily based, sensitivity based mostly and coverage centered.
Why do you require to observe continually?
Your network is often changing. New expert services are spun up, web applications up-to-date, permissions improved, products extra and eradicated. All of these can introduce potential vulnerabilities. The target of steady checking is to give in close proximity to-immediate opinions and insight into these alterations, evaluating and prioritizing vulnerabilities, so you can comprehend the risk across your entire infrastructure.
With this clear photo of what attackers can see and what is actually available in your internet-going through infrastructure, you can very easily tackle any issues as shortly as they occur. Ongoing monitoring not only provides visibility into the vulnerabilities in your IT setting and remote products, but also clarity into how all those vulnerabilities translate into company risk, and which are most possible to be qualified by attackers.
Continual network checking with Intruder
Advanced network checking applications like Intruder operate day-to-day network scans so your network see is usually precise and up to day – displaying active and unresponsive targets, any alterations considering that your final scan, expiring certificates, and the ports and solutions you anticipate – and more importantly, do not hope – to be exposed to the internet.
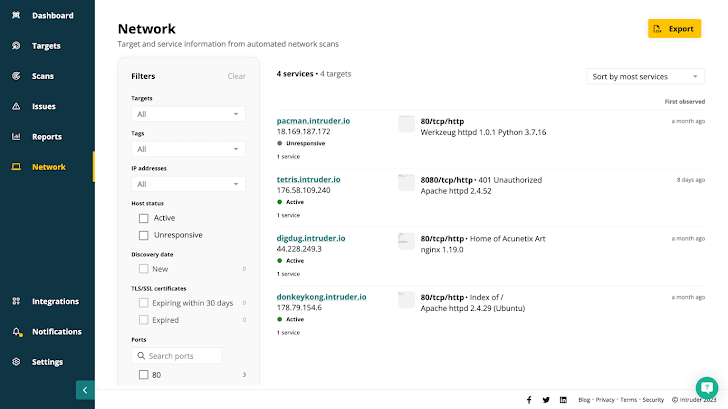 Intruder provides you a serious watch of your attack area combining continuous network monitoring, automatic vulnerability scanning, and proactive menace response in just one platform.
Intruder provides you a serious watch of your attack area combining continuous network monitoring, automatic vulnerability scanning, and proactive menace response in just one platform.
Any targets you incorporate will kick off a scan. Once finished, it adds the focus on to the queue for rescanning at common intervals. Any alterations will mechanically kick off a vulnerability scan, with issues prioritized by context so you can fix what matters most.
If you might be lucky sufficient to have your own network variety, you know how practical it can be but how tricky to manage. You want to make sure your complete vary is coated, but licensing large quantities of inactive IPs can be high-priced. Intruder monitors your external network ranges for lively IPs – but you may only shell out for the types in use.
This constant checking provides comprehensive and up-to-day visibility throughout your entire IT setting to just take your network security to a different level.
Go to Intruder to activate a totally free 14-day trial and working experience constant network monitoring for on your own.
Discovered this short article appealing? Adhere to us on Twitter and LinkedIn to study more exceptional content we write-up.
Some areas of this posting are sourced from:
thehackernews.com


 Russian Hackers Use Zulip Chat App for Covert C&C in Diplomatic Phishing Attacks
Russian Hackers Use Zulip Chat App for Covert C&C in Diplomatic Phishing Attacks