Cybersecurity researchers have identified a new Linux variant of a distant access trojan (RAT) termed BIFROSE (aka Bifrost) that employs a deceptive domain mimicking VMware.
“This latest model of Bifrost aims to bypass security measures and compromise focused units,” Palo Alto Networks Device 42 researchers Anmol Maurya and Siddharth Sharma reported.
BIFROSE is 1 of the long-standing threats that has been energetic since 2004. It has been made available for sale in underground message boards for up to $10,000 in the past, in accordance to a report from Development Micro in December 2015.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The malware has been put to use by a state-backed hacking team from China tracked as BlackTech (aka Circuit Panda, HUAPI, Manga Taurus, Palmerworm, PLEAD, Crimson Djinn, and Temp.Overboard), which has a history of placing organizations in Japan, Taiwan, and the U.S.

It really is suspected that the danger actor ordered the supply code or received accessibility to it close to 2010, and repurposed the malware for use in its very own campaigns by way of custom made backdoors like KIVARS and XBOW.
Linux variants of BIFROSE (aka ELF_BIFROSE) have been noticed given that at the very least 2020 with capabilities to launch distant shells, down load/add documents, and conduct file functions.
“Attackers typically distribute Bifrost by way of email attachments or destructive internet sites,” the researchers mentioned. “Once put in on a victim’s personal computer, Bifrost will allow the attacker to gather delicate facts, like the victim’s hostname and IP deal with.”
What would make the hottest variant noteworthy is that it reaches out to a command-and-handle (C2) server with the identify “down load.vmfare[.]com” in an attempt to masquerade as VMware. The deceptive area is solved by getting in contact with a Taiwan-dependent community DNS resolver with the IP deal with 168.95.1[.]1.
Device 42 stated it detected a spike in Bifrost exercise considering that Oct 2023, identifying no significantly less than 104 artifacts in its telemetry. It even further learned an Arm model of the malware, suggesting the risk actors are probable searching to expand their attack area.

“With new variants that make use of misleading domain approaches like typosquatting, a new spike in Bifrost action highlights the dangerous mother nature of this malware,” the researchers claimed.
The enhancement will come as McAfee Labs in-depth a new GuLoader campaign that propagates the malware via destructive SVG file attachments in email messages. The malware has also been observed being dispersed through VBS scripts as part of a multi-stage payload shipping and delivery.

“This current surge highlights its evolving practices for broader achieve and evasion,” Trustwave SpiderLabs mentioned in a post on X previously this week.
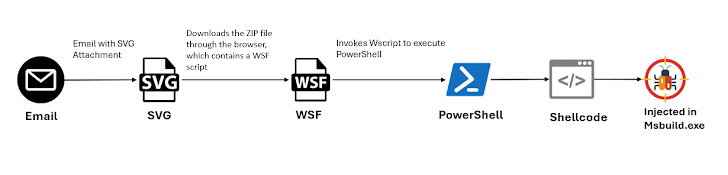
The Bifrost and GuLoader attacks coincide with the release of a new variation of the Warzone RAT, which lately experienced two of its operators arrested and its infrastructure dismantled by the U.S. authorities.
Located this posting appealing? Adhere to us on Twitter and LinkedIn to study additional unique content material we publish.
Some elements of this posting are sourced from:
thehackernews.com


 Five Eyes Agencies Warn of Active Exploitation of Ivanti Gateway Vulnerabilities
Five Eyes Agencies Warn of Active Exploitation of Ivanti Gateway Vulnerabilities