The Five Eyes (FVEY) intelligence alliance has issued a new cybersecurity advisory warning of cyber threat actors exploiting recognised security flaws in Ivanti Hook up Secure and Ivanti Policy Safe gateways, noting that the Integrity Checker Resource (ICT) can be deceived to provide a wrong perception of security.
“Ivanti ICT is not ample to detect compromise and that a cyber danger actor may be in a position to get root-amount persistence in spite of issuing manufacturing unit resets,” the agencies explained.
To day, Ivanti has disclosed 5 security vulnerabilities impacting its goods due to the fact January 10, 2024, out of which 4 have occur below energetic exploitation by numerous menace actors to deploy malware –

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
- CVE-2023-46805 (CVSS score: 8.2) – Authentication bypass vulnerability in web part
- CVE-2024-21887 (CVSS rating: 9.1) – Command injection vulnerability in web component
- CVE-2024-21888 (CVSS rating: 8.8) – Privilege escalation vulnerability in web component
- CVE-2024-21893 (CVSS rating: 8.2) – SSRF vulnerability in the SAML element
- CVE-2024-22024 (CVSS score: 8.3) – XXE vulnerability in the SAML component
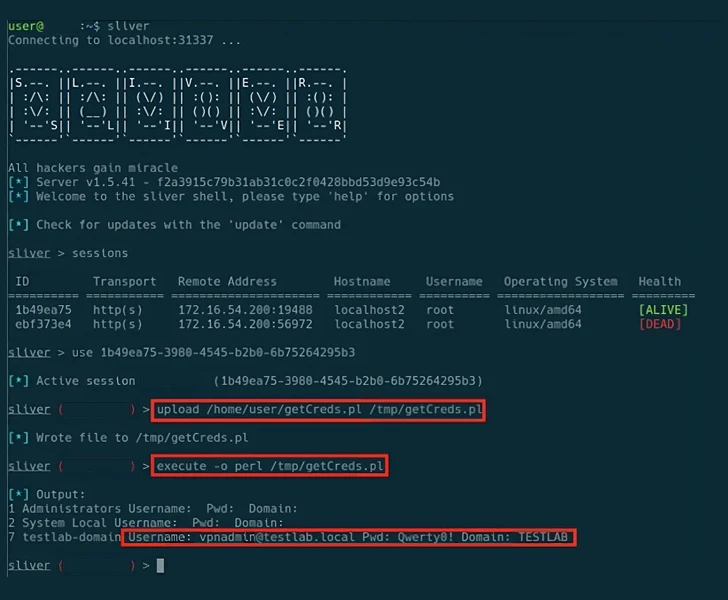
Mandiant, in an analysis printed this 7 days, explained how an encrypted edition of malware identified as BUSHWALK is put in a listing excluded by ICT in /information/runtime/cockpit/diskAnalysis.

The directory exclusions have been also beforehand highlighted by Eclypsium this month, stating the instrument skips a dozen directories from staying scanned, consequently allowing for an attacker to leave guiding backdoors in just one of these paths and nevertheless go the integrity look at.
“The safest program of action for network defenders is to assume a refined threat actor may possibly deploy rootkit degree persistence on a product that has been reset and lay dormant for an arbitrary quantity of time,” businesses from Australia, Canada, New Zealand, the U.K., and the U.S. stated.
They also urged organizations to “take into consideration the major risk of adversary entry to, and persistence on, Ivanti Join Secure and Ivanti Policy Safe gateways when pinpointing regardless of whether to carry on operating these devices in an enterprise surroundings.”
Ivanti, in response to the advisory, mentioned it is not mindful of any occasions of successful threat actor persistence next the implementation of security updates and factory resets. It can be also releasing a new variation of ICT that it mentioned “provides supplemental visibility into a customer’s appliance and all documents that are current on the technique.”
Observed this report fascinating? Comply with us on Twitter and LinkedIn to read additional unique content we article.
Some components of this report are sourced from:
thehackernews.com

 GitHub Rolls Out Default Secret Scanning Push Protection for Public Repositories
GitHub Rolls Out Default Secret Scanning Push Protection for Public Repositories