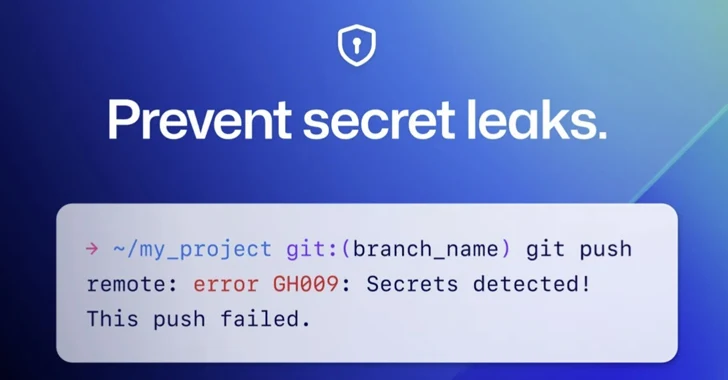
GitHub on Thursday introduced that it truly is enabling key scanning force defense by default for all pushes to community repositories.
“This implies that when a supported secret is detected in any press to a public repository, you will have the option to take out the magic formula from your commits or, if you deem the key risk-free, bypass the block,” Eric Tooley and Courtney Claessens stated.
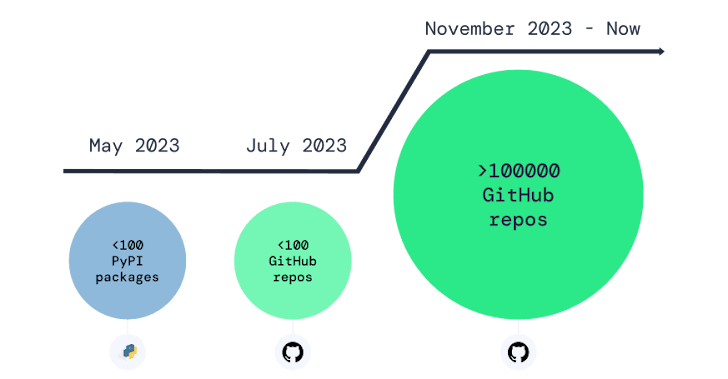
Drive safety was initial piloted as an decide-in attribute in August 2023, although it has been below screening because April 2022. It turned usually available in May possibly 2023.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The magic formula scanning characteristic is intended to determine in excess of 200 token types and patterns from far more than 180 company vendors in order to stop their fraudulent use by malicious actors.

The enhancement will come approximately 5 months immediately after the Microsoft subsidiary expanded magic formula scanning to incorporate validity checks for well known providers such as Amazon Web Solutions (AWS), Microsoft, Google, and Slack.
It also follows the discovery of an ongoing “repo confusion” attack targeting GitHub that’s inundating the supply code hosting platform with thousands of repositories containing obfuscated malware capable of thieving passwords and cryptocurrency from developer devices.
The attacks signify another wave of the similar malware distribution marketing campaign that was disclosed by Phylum and Development Micro very last year, leveraging bogus Python offers hosted on the cloned, trojanized repositories to provide a stealer malware known as BlackCap Grabber.
“Repo confusion attacks simply just rely on human beings to mistakenly select the destructive variation more than the actual a person, from time to time using social engineering methods as properly,” Apiiro said in a report this 7 days.
Identified this report interesting? Follow us on Twitter and LinkedIn to read through much more exceptional information we post.
Some parts of this report are sourced from:
thehackernews.com

 New Silver SAML Attack Evades Golden SAML Defenses in Identity Systems
New Silver SAML Attack Evades Golden SAML Defenses in Identity Systems