Cybersecurity scientists have disclosed a new attack procedure called Silver SAML that can be profitable even in circumstances exactly where mitigations have been utilized against Golden SAML attacks.
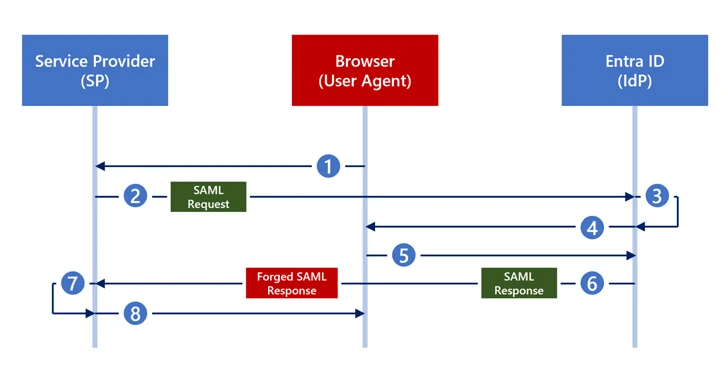
Silver SAML “permits the exploitation of SAML to launch attacks from an id provider like Entra ID from programs configured to use it for authentication, these as Salesforce,” Semperis scientists Tomer Nahum and Eric Woodruff stated in a report shared with The Hacker News.
Golden SAML (limited for Security Assertion Markup Language) was to start with documented by CyberArk in 2017. The attack vector, in a nutshell, entails the abuse of the interoperable authentication normal to impersonate almost any identity in an organization.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
It’s also identical to the Golden Ticket attack in that it grants attackers the ability to achieve unauthorized accessibility to any assistance in a federation with any privileges and to stay persistent in this natural environment in a stealthy manner.

“Golden SAML introduces to a federation the rewards that golden ticket presents in a Kerberos natural environment – from attaining any variety of access to stealthily keeping persistency,” security researcher Shaked Reiner noted at the time.
Serious-world attacks leveraging the method have been exceptional, the very first recorded use becoming the compromise of SolarWinds infrastructure to attain administrative entry by forging SAML tokens utilizing compromised SAML token signing certificates.
Golden SAML has also been weaponized by an Iranian menace actor codenamed Peach Sandstorm in a March 2023 intrusion to obtain an unnamed target’s cloud means sans necessitating any password, Microsoft revealed in September 2023.
The newest method is a spin on Golden SAML that is effective with an identification provider (IdP) like Microsoft Entra ID (formerly Azure Active Listing) and does not need entry to the Active Directory Federation Providers (Advert FS). It has been assessed as a moderate-severity threat to businesses.
“Within Entra ID, Microsoft presents a self-signed certification for SAML reaction signing,” the scientists claimed. “Alternatively, organizations can choose to use an externally generated certificate this kind of as people from Okta. On the other hand, that option introduces a security risk.”
“Any attacker that obtains the private vital of an externally generated certification can forge any SAML reaction they want and sign that reaction with the identical private essential that Entra ID retains. With this kind of solid SAML reaction, the attacker can then accessibility the application — as any person.”
Adhering to accountable disclosure to Microsoft on January 2, 2024, the business claimed the issue does not fulfill its bar for immediate servicing, but noted it will consider appropriate motion as necessary to safeguard clients.

Even though there is no proof that Silver SAML has been exploited in the wild, organizations are expected to use only Entra ID self-signed certificates for SAML signing uses. Semperis has also manufactured accessible a proof-of-principle (PoC) dubbed SilverSAMLForger to develop custom SAML responses.
“Organizations can check Entra ID audit logs for alterations to PreferredTokenSigningKeyThumbprint under ApplicationManagement,” the researchers reported.
“You will need to have to correlate these situations to Increase support principal credential gatherings that relate to the services principal. The rotation of expired certificates is a prevalent process, so you will require to identify irrespective of whether the audit occasions are genuine. Implementing change management processes to doc the rotation can support to decrease confusion during rotation activities.”
Found this report appealing? Adhere to us on Twitter and LinkedIn to examine more distinctive articles we post.
Some components of this write-up are sourced from:
thehackernews.com

 GTPDOOR Linux Malware Targets Telecoms, Exploiting GPRS Roaming Networks
GTPDOOR Linux Malware Targets Telecoms, Exploiting GPRS Roaming Networks