Spanish-speaking customers in Latin The usa have been at the receiving stop of a new botnet malware dubbed Horabot due to the fact at the very least November 2020.
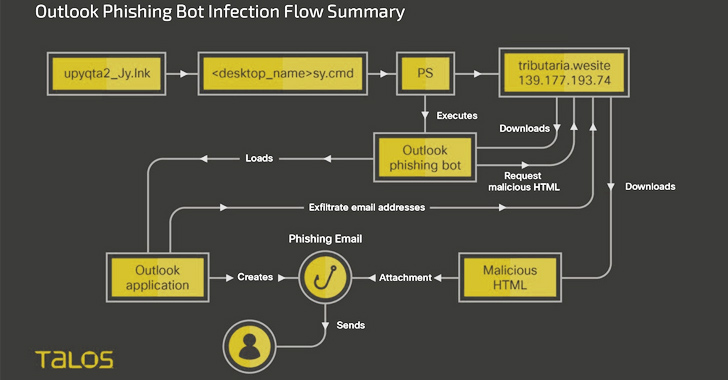
“Horabot enables the risk actor to handle the victim’s Outlook mailbox, exfiltrate contacts’ email addresses, and deliver phishing e-mails with destructive HTML attachments to all addresses in the victim’s mailbox,” Cisco Talos researcher Chetan Raghuprasad reported.
The botnet application also delivers a Windows-centered fiscal trojan and a spam device to harvest on line banking qualifications as nicely as compromise Gmail, Outlook, and Yahoo! webmail accounts to blast spam email messages.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The cybersecurity firm stated a vast majority of the infections are situated in Mexico, with confined victims identified in Uruguay, Brazil, Venezuela, Argentina, Guatemala, and Panama. The threat actor at the rear of the marketing campaign is considered to be in Brazil.
Qualified users of the ongoing marketing campaign principally span accounting, building and engineering, wholesale distribution, and investment decision verticals, despite the fact that it is really suspected that other sectors in the region might also be influenced.
The attacks commence with phishing emails bearing tax-themed lures that entice the recipients into opening an HTML attachment, which, in turn, embeds a website link that contains a RAR archive.
Opening the contents of the file effects in the execution of a PowerShell downloader script that is accountable for retrieving a ZIP file that contains the primary payloads from a remote server and rebooting the device.
The technique restart also serves as a launchpad for the banking trojan and the spam software, permitting the threat actor to steal facts, log keystrokes, seize screenshots, and disseminate additional phishing email messages to the victim’s contacts.
“This marketing campaign will involve a multi-stage attack chain that begins with a phishing email and potential customers to payload supply through the execution of a PowerShell downloader script and sideloading to authentic executables,” Raghuprasad stated.
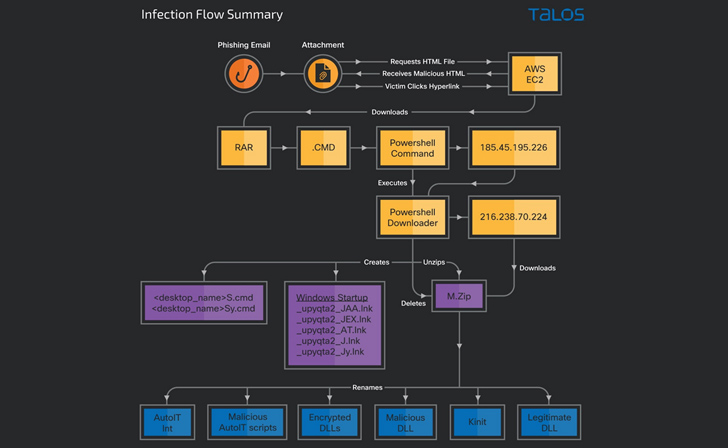
The banking trojan is a 32-bit Windows DLL written in the Delphi programming language, and shares overlaps with other Brazilian malware people like Mekotio and Casbaneiro.
Horabot, for its element, is an Outlook phishing botnet application composed in PowerShell that’s able of sending phishing email messages to all email addresses in the victim’s mailbox to propagate the infection. It’s also a deliberate endeavor to lessen the threat actor’s phishing infrastructure from staying exposed.
Impending WEBINAR 🔐 Mastering API Security: Understanding Your Correct Attack Surface area
Discover the untapped vulnerabilities in your API ecosystem and consider proactive methods in the direction of ironclad security. Join our insightful webinar!
Join the Session.advertisement-button,.ad-label,.advert-label:immediately afterscreen:inline-block.advert_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px solid #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-leading-remaining-radius:25px-moz-border-radius-topleft:25px-webkit-border-bottom-correct-radius:25px-moz-border-radius-bottomright:25px.advertisement-labelfont-dimension:13pxmargin:20px 0font-fat:600letter-spacing:.6pxcolor:#596cec.ad-label:just afterwidth:50pxheight:6pxcontent:”border-best:2px stable #d9deffmargin: 8px.advertisement-titlefont-size:21pxpadding:10px 0font-bodyweight:900textual content-align:leftline-height:33px.ad-descriptiontext-align:leftfont-sizing:15.6pxline-height:26pxmargin:5px !importantcolor:#4e6a8d.advert-buttonpadding:6px 12pxborder-radius:5pxbackground-coloration:#4469f5font-dimension:15pxcolor:#fff!importantborder:0line-height:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-weight:500letter-spacing:.2px
The disclosure comes a week after SentinelOne attributed an not known Brazilian threat actor to a lengthy-jogging campaign targeting extra than 30 Portuguese financial institutions with data-thieving malware considering that 2021.
It also follows the discovery of a new Android banking trojan dubbed PixBankBot that abuses the operating system’s accessibility solutions to perform fraudulent dollars transfers over the Brazilian PIX payments system.
PixBankBot is also the hottest illustration of malware that precisely focuses on Brazilian banking companies, featuring abilities related to BrasDex, PixPirate, and GoatRAT that have been noticed in latest months.
If anything at all, the developments signify nevertheless an additional iteration of a broader group of financially motivated hacking attempts emanating from Brazil, producing it vital that customers continue to be vigilant to avoid slipping prey to these threats.
Located this short article exciting? Follow us on Twitter and LinkedIn to study far more exceptional content we publish.
Some elements of this write-up are sourced from:
thehackernews.com

 The Importance of Managing Your Data Security Posture
The Importance of Managing Your Data Security Posture