Details security is reinventing by itself. As new information security posture management remedies arrive to market, companies are more and more recognizing the option to deliver proof-based security that proves how their information is getting protected. But what specifically is data security posture, and how do you control it?
Info security posture administration (DSPM) became mainstream next the publication of Gartner® Amazing Vendors™ in Knowledge Security—Secure and Speed up Sophisticated Use Situations. In that report, Gartner1 looks to have kicked off the preferred use of the knowledge security posture management phrase and substantial investment decision in this place by every single VC. Considering the fact that that report, Gartner has determined at the very least 16 DSPM distributors, such as Symmetry Programs.
What is Info Security Posture?
There absolutely is a good deal staying marketed and revealed about information security posture administration alternatives themselves, but we to start with preferred to dig into what is details security posture?

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Symmetry Techniques defines data security posture as “…the recent position of the capabilities needed to guard data from unauthorized access, destruction, and/or alteration. Facts security posture is an assessment of an organization’s info retail store or unique facts objects:
Knowledge attack surface: A mapping of the details to the identities, vulnerabilities, and other misconfigurations that can be utilized as entry details to gain obtain to it.
Info security management performance: An evidence-centered evaluation of the information security and privacy controls towards sector most effective techniques and organizational policy.
Data blast radius: A quantifiable assessment of the information at risk or the greatest probable influence of a security breach of a single identity, info shop, vulnerability, or misconfiguration. This includes identifying the varieties and volumes of info that could be impacted, as nicely as the approximated expenses and predicted consequences based on recent handle performance.
General, a robust organizational information security posture includes a complete method to managing the security of an organization’s info, including constant stock and classification of facts, ongoing evaluation and improvement of knowledge security controls, proactive rightsizing of entry to facts, and a commitment to steady monitoring and reaction to strange use of data.”
To keep a superior information security posture, organizations must do the next:
Inventory your details: A knowledge inventory—that is a in depth listing of all info shops and the sensitivity of the information inside them—is an crucial 1st stage in analyzing the existing status of capabilities.
Keep track of information exercise and information flows: An vital upcoming phase is to ensure you have visibility into action and the circulation of your details, mainly because it enhances your capability to detect and answer to any anomalies or indicators of compromise as you enhance your knowledge security posture.
Assess details security controls: Once you have this visibility and insight into your information, you can conduct an evidence-primarily based evaluation of your info security controls. This should really consist of pinpointing the degree of encryption of the facts, the validity of hashing and tokenization of facts in certain environments, and most importantly the validation of cloud configurations and access controls, including authentication demanded to entry data.
Lower info attack surface area: Companies must have procedures in put to use the benefits of this investigation to proactively detect and reduce the facts attack floor. This should really involve making certain multi-factor authentication is required for all identities with accessibility to delicate data and facts merchants that include delicate details and removing dormant accounts from the setting.
Lessen blast radius: Corporations should continuously assess the quantity of data at risk and prioritize pragmatic techniques to lessen the probable effect of a security breach of a single identity, facts keep, vulnerability, or misconfiguration. This ought to include things like eradicating sensitive knowledge from inappropriate environments, figuring out, and removing misconfigurations, and facts minimization by archiving or deleting data or by deleting unused privileges from active accounts.
The Symmetry DataGuard Option
Symmetry DataGuard is a purpose-created information security posture management platform. Symmetry DataGuard doesn’t only increase current SaaS platforms with data classification to assert DSPM coverage rather, it was developed from the floor up to maximize the protection of facts. The system is usually deployed inside the customer’s cloud setting as a way to ensure that knowledge never leaves the customer’s handle. This deployment model is properly suited for dealing with data, irrespective of sensitivity and several compliance laws.
At its main, the Symmetry DataGuard system has a deep graph of data objects, identities, and all permissions to and steps that are performed on the info objects. This interconnected graph is employed to provide the components essential for corporations to deal with their details security posture. We reviewed the Symmetry Remedy to see how it can help organizations tackle a couple of vital parts.
Data Stock
When installed and configured, Symmetry DataGuard gathers info from the cloud environments. This is created easier by setting up inside the customer’s cloud surroundings, but as long as Symmetry DataGuard has ideal permissions to query the facts, it can aggregate data across your cloud environments. To avoid pointless facts egress service fees, Symmetry Units recommends deploying Symmetry DataGuard in each cloud environment (i.e., AWS, Azure, etcetera.). Agentless discovery swiftly collects information about:
- The cloud setting.
- The identities (including consumers, expert services, roles, and teams) with obtain to the ecosystem.
- The datastores in the environment.
Examples of the atmosphere stock info collected by Symmetry DataGuard are proven in the image beneath:
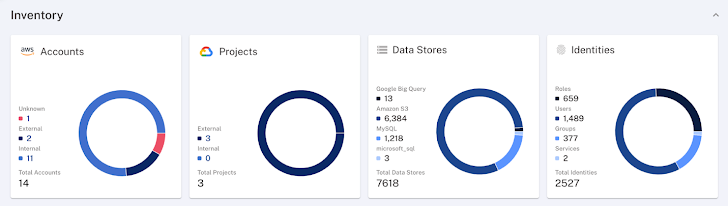 Determine 1: Information setting stock details gathered by Symmetry DataGuard
Determine 1: Information setting stock details gathered by Symmetry DataGuard
Info attained in this article is made use of to kickstart sampling of the details inside of the identified datastores. The sampling technique is absolutely customizable. Symmetry DataGuard provides a strong catalog of prebuilt facts identifiers that use a combination of keyword phrases, regex sample matching, and equipment finding out-dependent matching to determine and classify an organization’s data in just the identified datastores. Symmetry Programs will work with their shoppers to build, customize, and enhance the established of identifiers to raise the precision of their classification method.
This perception into the classification of knowledge in just each knowledge keep is additional to the deep graph and gives corporations with searchable sights and visualizations of their information inventory. Illustrations of this facts stock are amazingly gorgeous and shown in the graphic below:
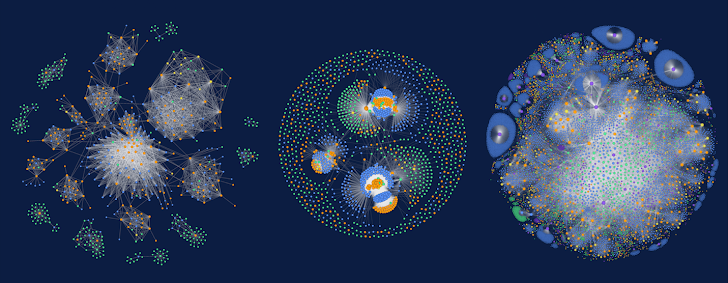 Determine 2: Information visualizations aid improve the precision of the data classification system by mapping identities, accessibility, facts sorts, and exactly where the information is saved.
Determine 2: Information visualizations aid improve the precision of the data classification system by mapping identities, accessibility, facts sorts, and exactly where the information is saved.
Keep track of Information Activity and Facts Flows
As component of the discovery and ongoing monitoring of the atmosphere, Symmetry DataGuard collects telemetry on all the info action or info operations being carried out on info in just your ecosystem. This includes unsuccessful and denied attempts. This telemetry is utilized to deepen the perception supplied on who is accessing an organization’s facts and wherever that facts is flowing to or from as a final result.
This information and facts is cross-correlated with the facts inventory to assistance companies pinpoint external details flows, unsuccessful tries to obtain delicate data, and a selection of other appealing details-centric danger detection eventualities. An illustration visualization of these flows is shown under:
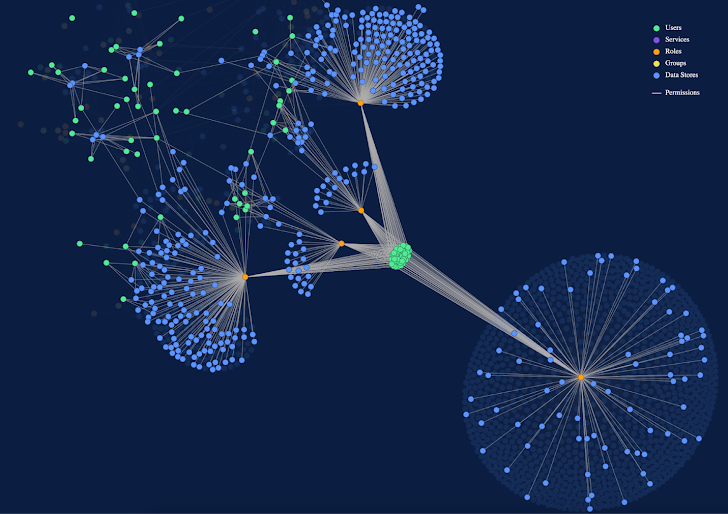 Determine 3: Knowledge flows assistance corporations pinpoint information-centric threat detection eventualities
Determine 3: Knowledge flows assistance corporations pinpoint information-centric threat detection eventualities
Functions are grouped into 4 high-amount courses: development, go through, update, or deletion of information. This will help when prioritizing strange or high-risk activity in opposition to precise info.
Execute Evaluation of Data Security Controls
Symmetry DataGuard also assesses the information security and identification configurations and can raise alerts when configurations are unsuccessful to meet outlined insurance policies or are adjusted. These configurations include things like, but are not limited to, determining regardless of whether:
- Facts is encrypted. (This consists of indigenous.)
- MFA is enabled.
- Checking is enabled.
Symmetry DataGuard has out-of-the-box compliance policies that are employed to check out for compliance with data-centric parts of the Center of Internet Security (CIS) benchmarks and other compliance frameworks. Illustrations of the compliance dashboard are revealed below:
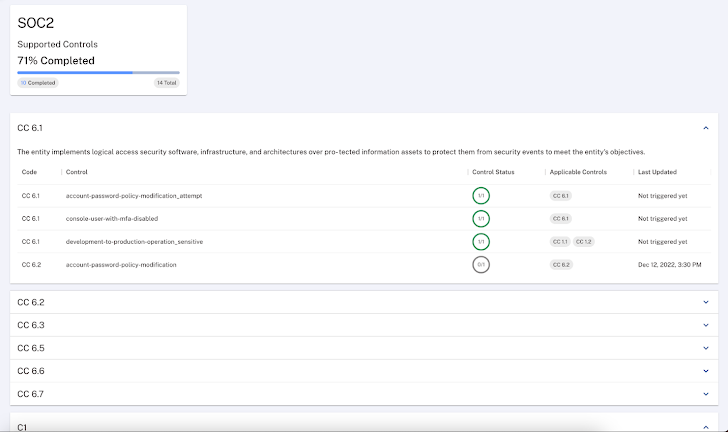 Determine 4:The Symmetry DataGuard compliance dashboards include out-of-the-box compliance procedures that are utilised to check out for compliance with data-centric portions of the Centre of Internet Security (CIS) benchmarks and other compliance frameworks
Determine 4:The Symmetry DataGuard compliance dashboards include out-of-the-box compliance procedures that are utilised to check out for compliance with data-centric portions of the Centre of Internet Security (CIS) benchmarks and other compliance frameworks
Just about every compliance test on the compliance dashboard incorporates details about the configuration that was checked and the remediation actions to tackle it. We extend 1 of the compliance checks and get the adhering to thorough consequence:
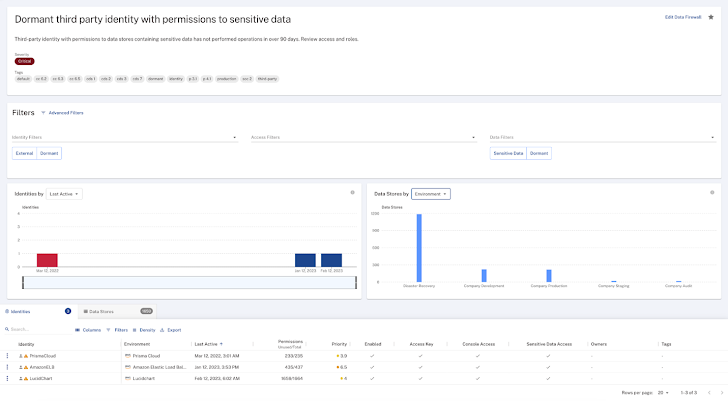 Determine 5: Compliance checks include details on the configuration and remediation ways
Determine 5: Compliance checks include details on the configuration and remediation ways
With the compliance dashboard, corporations are ready to verify their knowledge for misconfigurations and compliance with many regulatory frameworks (PCI DSS, SOC 2 etc.). The compliance checks carried out by Symmetry DataGuard are extra precise than other compliance configurations executed at the cloud infrastructure and are important for corporations in heavily controlled industries.
The Takeaway
A very good details security posture cuts down the attack floor and blast radius of your organization’s details. Accomplishing and protecting a excellent facts security posture calls for a detailed understanding of the knowledge itself, the identities that can obtain it, the controls that shield it and checking of the operations staying done. A main platform like Symmetry DataGuard is capable to manage knowledge inventory, observe operations and exercise and examine for protected knowledge security configuration and compliance, and thus supply evidence-based information security.
If you are fascinated in acquiring out more about Symmetry Devices and their info security posture management alternative, Symmetry DataGuard, You can ask for a demo at Symmetry-Devices.com.
Discovered this posting intriguing? Follow The Hacker Information on Twitter and LinkedIn to read through more exceptional information.
1Gartner, Cool Suppliers in Info Security — Secure and Accelerate Advanced Use Instances, by Joerg Fritsch, Andrew Bales, Ravisha Chugh, Brian Lowans, Mark Horvath, 19 April 2022
Gartner Disclaimer
Gartner does not endorse any seller, products or provider depicted in its study publications, and does not recommend technology users to pick out only all those suppliers with the highest scores or other designation. Gartner exploration publications consist of the opinions of Gartner’s exploration corporation and need to not be construed as statements of point. Gartner disclaims all warranties, expressed or implied, with respect to this exploration, together with any warranties of merchantability or health and fitness for a certain goal.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliate marketers in the U.S. and internationally, Hoopla Cycle and Cool Suppliers are registered trademarks of Gartner, Inc. and/or its affiliate marketers and are utilised herein with authorization. All rights reserved.
Identified this post fascinating? Observe us on Twitter and LinkedIn to study a lot more exceptional content we publish.
Some elements of this article are sourced from:
thehackernews.com


 Camaro Dragon Strikes with New TinyNote Backdoor for Intelligence Gathering
Camaro Dragon Strikes with New TinyNote Backdoor for Intelligence Gathering