Cybersecurity scientists have found out an up-to-date variant of a stealer and malware loader referred to as BunnyLoader that modularizes its numerous functions as effectively as allow for it to evade detection.
“BunnyLoader is dynamically producing malware with the ability to steal data, qualifications and cryptocurrency, as perfectly as deliver additional malware to its victims,” Palo Alto Networks Unit 42 stated in a report released past 7 days.
The new model, dubbed BunnyLoader 3., was announced by its developer named Player (or Player_Bunny) on February 11, 2024, with rewritten modules for knowledge theft, lessened payload dimensions, and increased keylogging capabilities.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
BunnyLoader was 1st documented by Zscaler ThreatLabz in September 2023, describing it as malware-as-a-service (MaaS) developed to harvest qualifications and aid cryptocurrency theft. It was originally available on a membership basis for $250 per thirty day period.

The malware has since undergone repeated updates that are aimed at evading antivirus defenses as well as expanding on its details gathering features, with BunnyLoader 2. unveiled by the finish of the exact month.
The 3rd era of BunnyLoader goes a stage even more by not only incorporating new denial-of-provider (DoS) capabilities to mount HTTP flood attacks from a focus on URL, but also splitting its stealer, clipper, keylogger, and DoS modules into unique binaries.
“Operators of BunnyLoader can opt for to deploy these modules or use BunnyLoader’s developed-in commands to load their choice of malware,” Device 42 defined.
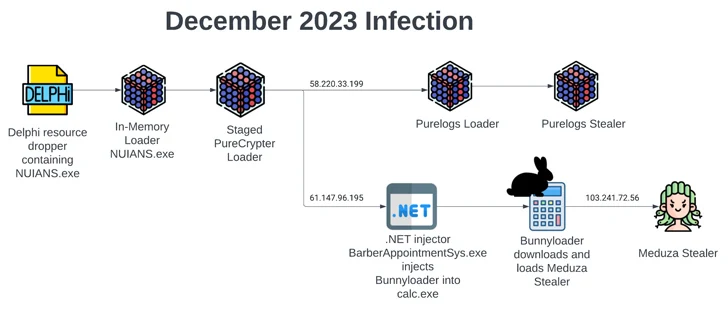
An infection chains providing BunnyLoader have also grow to be progressively additional sophisticated, leveraging a formerly undocumented dropper to loader PureCrypter, which then forks into two different branches.
Even though a person department launches the PureLogs loader to in the long run produce the PureLogs stealer, the next attack sequence drops BunnyLoader to distribute yet another stealer malware termed Meduza.
“In the ever shifting landscape of MaaS, BunnyLoader continues to evolve, demonstrating the need to have for threat actors to often retool to evade detection,” Unit 42 researchers stated.
The advancement will come amid the ongoing use of SmokeLoader malware (aka Dofoil or Sharik) by a suspected Russian cybercrime crew called UAC-006 to target the Ukrainian government and fiscal entities. It is regarded to be active considering the fact that 2011.
As a lot of as 23 phishing attack waves offering SmokeLoader were being recorded in between May perhaps and November 2023, in accordance to an exhaustive report revealed by Ukraine’s State Cyber Protection Heart (SCPC).

“Mainly a loader with extra information and facts-stealing abilities, SmokeLoader has been joined to Russian cybercrime functions and is commonly readily available on Russian cybercrime message boards,” Unit 42 claimed.
Incorporating to BunnyLoader and SmokeLoader is a new facts stealer malware codenamed GlorySprout, which is produced in C++ and provided for $300 for a life time access. In accordance to RussianPanda, the stealer is a clone of Taurus Stealer.
“A notable difference is that GlorySprout, contrary to Taurus Stealer, does not down load supplemental DLL dependencies from C2 servers,” the researcher explained. “Additionally, GlorySprout lacks the Anti-VM characteristic that is existing in Taurus Stealer.”
Uncovered this write-up fascinating? Comply with us on Twitter and LinkedIn to examine more exclusive written content we write-up.
Some areas of this post are sourced from:
thehackernews.com


 Ukraine Arrests Trio for Hijacking Over 100 Million Email and Instagram Accounts
Ukraine Arrests Trio for Hijacking Over 100 Million Email and Instagram Accounts