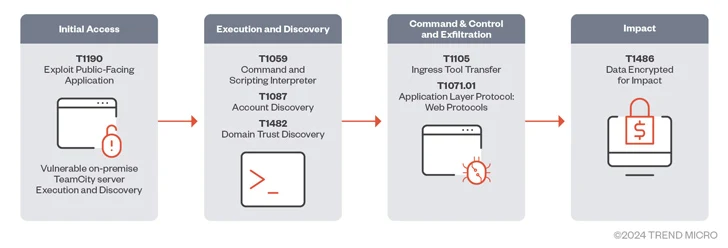
Numerous danger actors are exploiting the not long ago disclosed security flaws in JetBrains TeamCity software to deploy ransomware, cryptocurrency miners, Cobalt Strike beacons, and a Golang-based distant accessibility trojan named Spark RAT.
The attacks entail the exploitation of CVE-2024-27198 (CVSS rating: 9.8) that allows an adversary to bypass authentication measures and achieve administrative regulate more than afflicted servers.
“The attackers are then able to set up malware that can reach out to its command-and-regulate (C&C) server and conduct further instructions these as deploying Cobalt Strike beacons and distant entry trojans (RATs),” Trend Micro said in a new report.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Ransomware can then be put in as a last payload to encrypt documents and demand ransom payments from victims.”
Next public disclosure of the flaw before this month, it has been weaponized by threat actors related with BianLian and Jasmin ransomware households, as properly as to drop the XMRig cryptocurrency miner and Spark RAT.
Corporations relying on TeamCity for their CI/CD processes are recommended to update their software package as shortly as attainable to safeguard against probable threats.

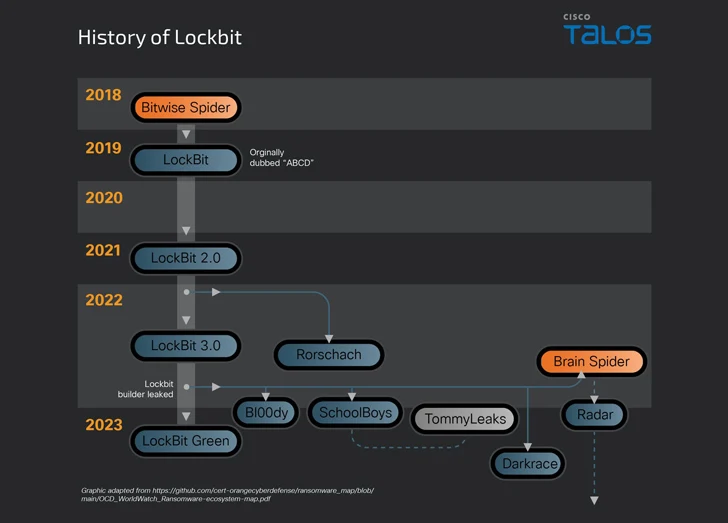
The development will come as ransomware proceeds to be each formidable and profitable, with new strains like DoNex, Evil Ant, Lighter, RA Planet, and WinDestroyer rising in the wild, even as infamous cybercrime crews like LockBit are even now accepting affiliate marketers into their system in spite of law enforcement steps versus them.
WinDestroyer, in individual, stands out for its capability to encrypt data files and render qualified units unusable with no implies to get well the details, increasing the chance that the risk actors behind it are geopolitically inspired.
“Just one of the key issues when tackling ransomware criminal offense is the mother nature of the affiliate plan, with actors normally working for many RaaS outfits at a time,” Cisco Talos mentioned. “It is likely to consider persistent, strategic endeavours to appreciably injury RaaS operations and weaken the regenerative ability of these gangs.”
Facts shared by the U.S. Federal Bureau of Investigation’s (FBI) Internet Criminal offense Grievance Middle (IC3) demonstrates that 2,825 ransomware infections ended up reported in 2023, causing altered losses of extra than $59.6 million. Of these, 1,193 arrived from businesses belonging to a critical infrastructure sector.
The leading five ransomware variants impacting critical infrastructure in the U.S. include LockBit, BlackCat (aka ALPHV or Noberus), Akira, Royal, and Black Basta.
Aside from supplying a bigger chunk of the proceeds to court docket affiliates, the landscape is witnessing elevated collaboration involving distinct ransomware teams that share their destructive tooling with just about every other.
These partnerships also manifest in the kind of ghost teams, in which a person ransomware procedure outsources its competencies to a further, as noticed in the scenario of Zeon, LockBit, and Akira.
Broadcom-owned Symantec, in a report revealed very last week, uncovered that “ransomware activity stays on an upward craze in spite of the number of attacks claimed by ransomware actors lowering by slightly more than 20% in the fourth quarter of 2023.”
According to data posted by NCC Team, the overall amount of ransomware instances in February 2024 enhanced by 46% from January, up from 285 to 416, led by LockBit (33%), Hunters (10%), BlackCat (9%), Qilin (9%), BianLian (8%), Enjoy (7%), and 8Foundation (7%).
“The latest law enforcement activity has the likely to polarize the ransomware landscape, producing clusters of smaller sized RaaS operators that are extremely lively and harder to detect thanks to their agility in underground message boards and marketplaces,” Matt Hull, international head of danger intelligence at NCC Group, reported.

“It appears that the attention drawn by the much larger ‘brand’ ransomware, this sort of as LockBit and Cl0p, is leading to new and modest generic RaaS affiliate partnerships getting to be the norm. As a result, detection and attribution could become harder, and affiliate marketers may perhaps effortlessly change providers due to small entry thresholds and negligible financial involvement.”
This has also been complemented by danger actors obtaining novel methods to infect victims by mostly exploiting vulnerabilities in public-experiencing apps and evade detection, as perfectly as refining their practices by progressively banking on respectable software package and dwelling-off-the-land (LotL) techniques.
Also popular among the ransomware attackers are utilities like TrueSightKiller, GhostDriver, and Terminator, which leverage the Provide Your Have Susceptible Driver (BYOVD) technique to disable security software package.
“BYOVD attacks are appealing to risk actors, as they can offer a means by which to disable AV and EDR methods at the kernel level,” Sophos researchers Andreas Klopsch and Matt Wixey mentioned in a report this thirty day period. “The sheer volume of recognised vulnerable motorists suggests that attackers have a wealth of selections to select from.”
Located this report intriguing? Observe us on Twitter and LinkedIn to go through more special content we publish.
Some areas of this write-up are sourced from:
thehackernews.com


 New BunnyLoader Malware Variant Surfaces with Modular Attack Features
New BunnyLoader Malware Variant Surfaces with Modular Attack Features