Cybersecurity researchers have disclosed particulars of the most current model of the Chaos ransomware line, dubbed Yashma.
“Though Chaos ransomware builder has only been in the wild for a 12 months, Yashma statements to be the sixth model (v6.) of this malware,” BlackBerry investigation and intelligence group mentioned in a report shared with The Hacker Information.
Chaos is a customizable ransomware builder that emerged in underground boards on June 9, 2021, by falsely promoting by itself as the .NET edition of Ryuk even with sharing no these kinds of overlaps with the notorious counterpart.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The fact that it is really provided for sale also implies that any destructive actor can invest in the builder and develop their very own ransomware strains, turning it into a strong menace.
It has since undergone five successive iterations aimed at improving its functionalities: model 2. on June 17, model 3. on July 5, version 4. on August 5, and model 5. in early 2022.

When the initial three variants of Chaos functioned a lot more like a harmful trojan than regular ransomware, Chaos 4. expanded its encryption procedure by increasing the higher limit of files that can be encrypted to 2.1MB.
Model 4. has also been actively weaponized by a ransomware collective regarded as Onyx as of April 2022 by creating use of an up-to-date ransom be aware and a refined record of file extensions that can be focused.
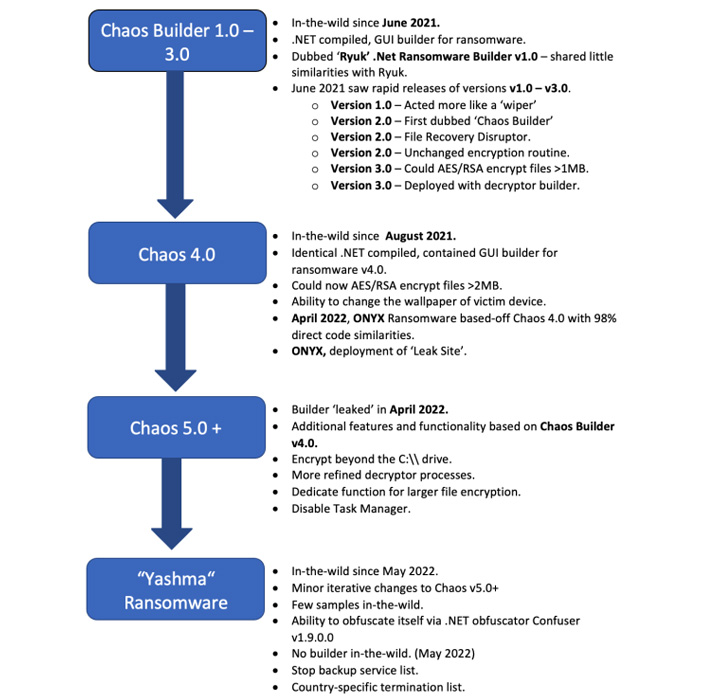
“Chaos 5. tried to take care of the most significant challenge of prior iterations of the threat, namely that it was not able to encrypt data files larger sized than 2MB without having irretrievably corrupting them,” the scientists spelled out.
Yashma is the most recent variation to sign up for this record, showcasing two new improvements, which includes the capacity to stop execution based mostly on a victim’s area and terminate a variety of procedures affiliated with antivirus and backup program.

“Chaos started as a somewhat standard endeavor at a .NET compiled ransomware that in its place functioned as a file-destructor or wiper,” the scientists mentioned. “About time it has developed to come to be a comprehensive-fledged ransomware, including additional attributes and functionality with every single iteration.”
The growth arrives as a Chaos ransomware variant has been spotted siding with Russia in its ongoing war versus Ukraine, with the article-encryption action leading to an inform containing a website link that directs to a website with pro-Russian messages.
“The attacker has no intention of supplying a decryption software or file recovery guidance for its victims to recuperate their affected information,” Fortinet FortiGuard Labs disclosed final week, incorporating it “will make the malware a file destroyer.”
Discovered this posting exciting? Stick to THN on Facebook, Twitter and LinkedIn to examine a lot more distinctive material we post.
Some sections of this short article are sourced from:
thehackernews.com


 Open source packages with millions of installs hacked to harvest AWS credentials
Open source packages with millions of installs hacked to harvest AWS credentials