Microsoft on Tuesday disclosed it took methods to suspend accounts that were used to publish destructive motorists that were being accredited by its Windows Hardware Developer Program ended up applied to signal malware.
The tech giant stated its investigation exposed the exercise was limited to a amount of developer application accounts and that no even further compromise was detected.
Cryptographically signing malware is regarding not minimum for the reason that it not only undermines a vital security mechanism but also will allow danger actors to subvert common detection strategies and infiltrate concentrate on networks to perform highly privileged functions.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The probe, Redmond stated, was initiated right after it was notified of rogue motorists staying used in submit-exploitation attempts, which include deploying ransomware, by cybersecurity corporations Mandiant, SentinelOne, and Sophos on Oct 19, 2022.
One particular notable aspect of these attacks was that the adversary experienced currently obtained administrative privileges on compromised devices right before utilizing the drivers.
“Many developer accounts for the Microsoft Spouse Middle were engaged in distributing malicious motorists to acquire a Microsoft signature,” Microsoft spelled out. “A new try at distributing a malicious driver for signing on September 29, 2022, led to the suspension of the sellers’ accounts in early Oct.”

According to an examination from Sophos menace actors affiliated with the Cuba ransomware (aka COLDDRAW) planted a malicious signed driver in a unsuccessful try at disabling endpoint detection resources by means of a novel malware loader dubbed BURNTCIGAR, which was to start with revealed by Mandiant in February 2022.
The corporation also identified a few variants of the driver signed by code signing certificates that belong to two Chinese companies, Zhuhai Liancheng Technology and Beijing JoinHope Picture Technology.
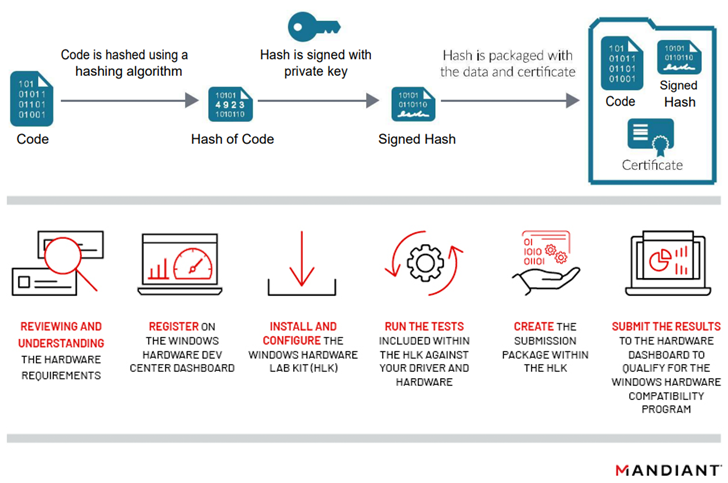
The reasoning driving making use of signed drivers is that it gives a way for menace actors to get around important security steps which demand kernel-mode drivers to be signed in buy for Windows to load the deal. What is a lot more, the approach misuses the de facto rely on security tools location in Microsoft-attested drivers to their edge.
“Menace actors are moving up the belief pyramid, trying to use increasingly much more effectively-reliable cryptographic keys to digitally signal their drivers,” Sophos researchers Andreas Klopsch and Andrew Brandt reported. “Signatures from a substantial, trusted application publisher make it a lot more most likely the driver will load into Windows without having hindrance.”
Google-owned Mandiant, in a coordinate disclosure, said it observed a financially determined threat team recognised as UNC3944 employing a loader named STONESTOP to install a malicious driver dubbed POORTRY which is created to terminate processes involved with security computer software and delete files.
Stating that it has “regularly observed threat actors use compromised, stolen, and illicitly obtained code-signing certificates to indicator malware,” the menace intelligence and incident response company famous that “quite a few distinct malware family members, related with distinctive danger actors, have been signed with this method.”
This has presented rise to the probability that these hacking teams could be leveraging a prison company for code signing (i.e., destructive driver signing as a provider), whereby the provider will get the malware artifacts signed by means of Microsoft’s attestation method on behalf of the actors.
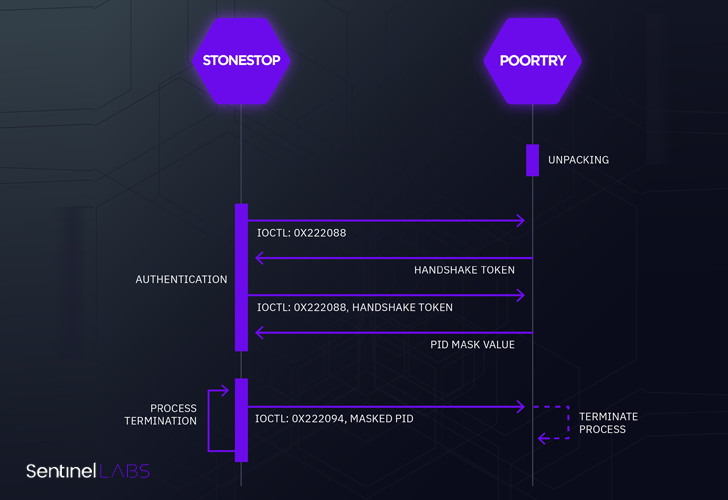
STONESTOP and POORTRY are explained to have been utilized by UNC3944 in attacks aimed at telecommunication, BPO, MSSP, financial companies, cryptocurrency, leisure, and transportation sectors, SentinelOne claimed, adding a distinctive threat actor utilized a identical signed driver that resulted in the deployment of Hive ransomware.
Microsoft has due to the fact revoked the certificates for impacted documents and suspended the partners’ vendor accounts to counter the threats as section of its December 2022 Patch Tuesday update.
This is not the initial time electronic certificates have been abused to sign malware. Final 12 months, a Netfilter driver qualified by Microsoft turned out to be a destructive Windows rootkit that was observed communicating with command-and-management (C2) servers located in China.
It really is not a Windows-only phenomenon, nevertheless, as Google this month printed results that compromised system certificates managed by Android gadget makers which include Samsung and LG experienced been made use of to indication destructive apps distributed by means of unofficial channels.
The progress also comes amid a broader abuse of signed drivers to sabotage security software program in modern months. The attack, referred to as Provide Your Have Susceptible Driver (BYOVD), requires exploiting reputable motorists that consist of identified shortcomings to escalate privileges and execute publish-compromise actions.
Microsoft, in late Oct, mentioned it truly is enabling the susceptible driver blocklist (DriverSiPolicy.p7b) by default for all devices with Windows 11 2022 update, together with validating that it is the very same throughout different running procedure versions, pursuing an Ars Technica report that highlighted inconsistencies in updating the blocklist for Windows 10 equipment.
“Code signing mechanisms are an important function in fashionable running devices,” SentinelOne said. “The introduction of driver signing enforcement was vital in stemming the tide of rootkits for decades. The receding performance of code signing signifies a danger to security and verification mechanisms at all OS levels.”
Observed this write-up exciting? Adhere to us on Twitter and LinkedIn to browse much more special written content we publish.
Some pieces of this write-up are sourced from:
thehackernews.com


 Why PCI DSS 4.0 Should Be on Your Radar in 2023
Why PCI DSS 4.0 Should Be on Your Radar in 2023