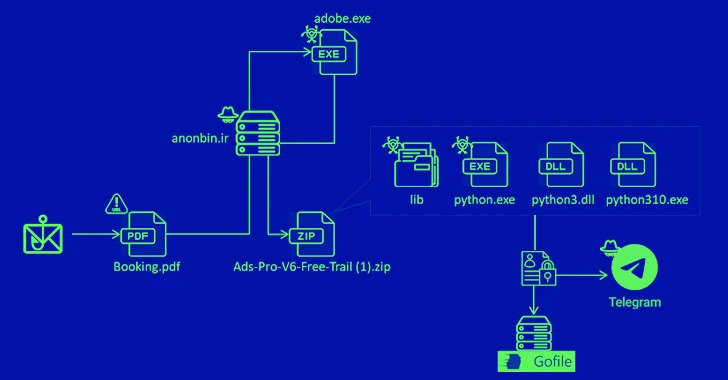
A phishing marketing campaign has been observed delivering an information stealer malware referred to as MrAnon Stealer to unsuspecting victims by means of seemingly benign scheduling-themed PDF lures.
“This malware is a Python-centered data stealer compressed with cx-Freeze to evade detection,” Fortinet FortiGuard Labs researcher Cara Lin said. “MrAnon Stealer steals its victims’ credentials, method information, browser periods, and cryptocurrency extensions.”
There is proof to counsel that Germany is the principal concentrate on of the attack as of November 2023, owing to the range of occasions the downloader URL hosting the payload has been queried.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Masquerading as a firm looking to reserve hotel rooms, the phishing email bears a PDF file that, upon opening, activates the an infection by prompting the receiver to download an current edition of Adobe Flash.

Carrying out so success in the execution of .NET executables and PowerShell scripts to eventually operate a pernicious Python script, which is capable of accumulating information from several apps and exfiltrating it to a public file-sharing web-site and the menace actor’s Telegram channel.
It can be also able of capturing data from fast messaging apps, VPN clientele, and documents matching a sought after listing of extensions.

MrAnon Stealer is made available by the authors for $500 for every thirty day period (or $750 for two months), along with a crypter ($250 per month) and a stealthy loader ($250 for every thirty day period).
“The marketing campaign at first disseminated Cstealer in July and August but transitioned to distributing MrAnon Stealer in October and November,” Lin mentioned. “This sample indicates a strategic approach involving the ongoing use of phishing e-mails to propagate a wide range of Python-based mostly stealers.”
The disclosure will come as the China-joined Mustang Panda is behind a spear-phishing email marketing campaign focusing on the Taiwanese authorities and diplomats with an aim to deploy SmugX, a new variant of the PlugX backdoor that was earlier uncovered by Check Point in July 2023.
Located this report appealing? Adhere to us on Twitter and LinkedIn to examine much more unique material we publish.
Some sections of this short article are sourced from:
thehackernews.com

 Apple Releases Security Updates to Patch Critical iOS and macOS Security Flaws
Apple Releases Security Updates to Patch Critical iOS and macOS Security Flaws