Making certain delicate facts stays confidential, secured from unauthorized entry, and compliant with details privacy restrictions is paramount. Details breaches end result in economical and reputational harm but also direct to legal implications. As a result, strong details access security measures are essential to safeguard an organization’s property, maintain customer have faith in, and fulfill regulatory needs.
A thorough Details Security Platform is vital for total visibility and management of delicate info. A single instance is Satori’s Universal Details Permissions Scanner (UDPS), an open-source authorization evaluation instrument. UDPS, offered on GitHub, enables universal visibility into knowledge entry permissions across numerous information outlets. With this instrument, it truly is less difficult to detect who has the likely to accessibility sensitive details, which can assistance businesses acquire a proactive approach to maximizing their security posture, streamline compliance, and make certain properly-ruled data entry.
Comprehending the Need to have for Common Data Permissions
In managing details obtain permissions throughout significant volumes of facts, facts engineers have to offer with several worries.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
One particular these kinds of obstacle is the complexity of granting and revoking permissions to numerous consumers across numerous knowledge repositories. As corporations scale up their operations and facts grows exponentially, holding track of who has accessibility to what gets significantly complicated.
This complexity can direct to glitches, security vulnerabilities, and difficulties in protecting an audit trail of information obtain, which is critical for compliance and security purposes. Details engineers are often tasked with preserving a good equilibrium in between supplying accessibility to authorized people and safeguarding knowledge from unauthorized entry.
Dispersed Facts Merchants
The info access permissions administration landscape has grow to be additional complicated in modern decades thanks to the popular adoption of cloud computing. Facts engineers facial area a highly dispersed facts landscape, with info now residing in on-prem details centers, a number of cloud platforms, and edge units. Making sure facts security and governance throughout these numerous environments demands a a lot more unified solution to knowledge accessibility permissions.
The dynamic nature of the cloud signifies that standard access management products could no more time suffice, and details engineers have to undertake new paradigms that incorporate granular control, visibility, and governance.
Satori’s UDPS
Satori’s open up-supply UDPS usually takes a proactive and extensive technique to data obtain authorization. It scans and analyzes the permissions model of each and every details platform to retrieve a human-readable checklist of buyers and their access stage to information belongings, like database tables, cloud storage buckets, documents, and more.
Rather of demanding details engineers to navigate the intricacies of each specific knowledge store’s obtain controls, UDPS gives a unified system to see and take care of knowledge permissions throughout all details repositories. Information engineers no for a longer time want to use unique accessibility handle mechanisms, cutting down the likely for glitches and unauthorized obtain.
The standout feature of UDPS is its universal visibility into info accessibility permissions. Soon after scanning all databases, details warehouses, cloud accounts, and information lakes, UDPS analyzes the permissions and retrieves a record of users, their accessibility ranges, and what they have access to.
The Universal Data Permissions Scanner is out there in two methods:
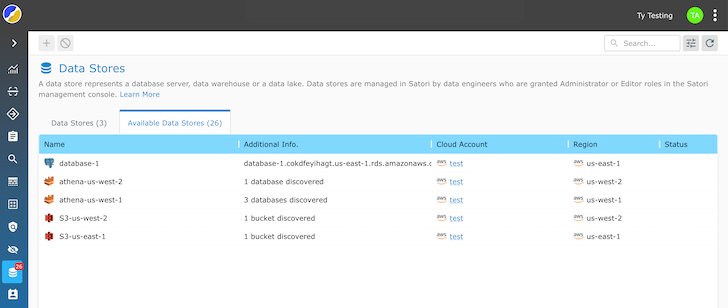
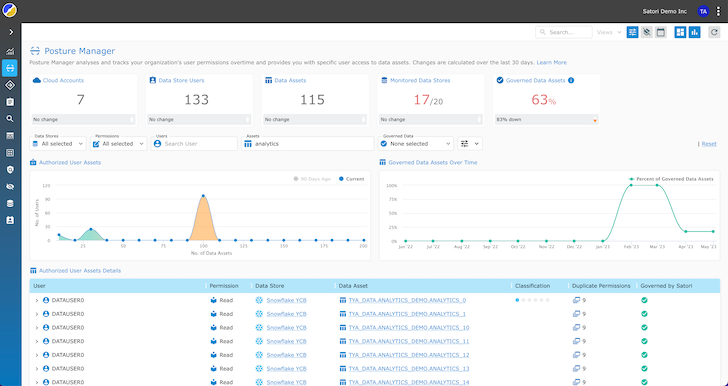
Details engineers get greater visibility, letting them to swiftly discover overprivileged customers, unauthorized accessibility, or strange behavior in true time. Universal visibility simplifies the auditing process and assures that information entry continues to be transparent and compliant with security and privacy restrictions.
Knowledge engineers can efficiently deal with data security and governance, minimizing safe and compliant info entry problems.
Advantages of Making use of an OS UDPS
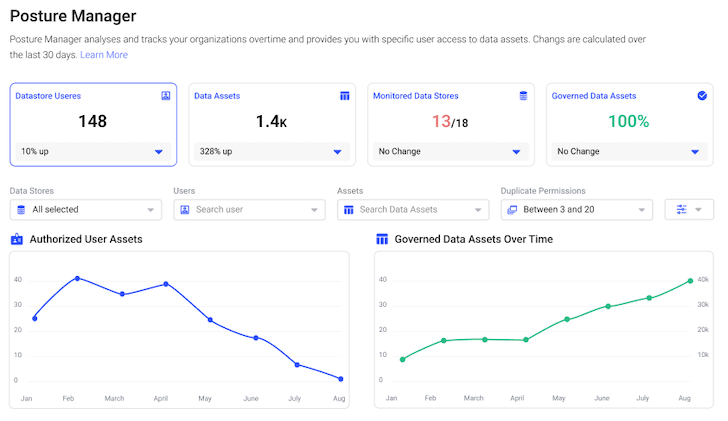
Relieve of Implementation
Some critical insights into the simplicity of applying Satori’s remedy:
- Agentless Deployment: There is no need to have to install agents or further application on your details outlets or methods. This agentless approach simplifies the deployment approach and eliminates the want for complex configurations or alterations to your current infrastructure.
- Zero Code Variations: It does not involve any improvements to existing info structures or schemas. The knowledge continues to be intact and retains its composition.
- Consumer-Welcoming Interface: The interface simplifies the definition and enforcement of knowledge entry insurance policies. Security and information engineering groups can quickly configure and take care of good-grained policies to handle who can obtain unique data aspects without having necessitating specialised coding or intensive technical experience.
- Authentic-time Coverage Updates: Makes it possible for for actual-time policy updates so that security actions are adapted on the fly to handle rising threats or transforming compliance prerequisites. This agility simplifies the ongoing management of info security controls.
- Non-Intrusive Information Encryption: Transparent info encryption that would not disrupt present person interactions. Details stays obtainable to licensed end users without having obvious modifications in how they interact.
- Compatibility and Scalability: Compatible with many information outlets, databases, data lakes, and cloud platforms. It also scales with your organization’s desires.
Implementation is a straightforward and trouble-free of charge approach. It would not need alterations to your information structures or person interactions. The ease of implementation makes Satori an desirable answer for corporations hunting to boost their facts security easily.
Summary
Satori’s Common Facts Permissions Scanner (UDPS) simplifies information access authorization complexities by supplying a centralized, non-intrusive resolution. It presents common visibility into facts entry permissions throughout various data repositories, enabling corporations to recognize overprivileged people, streamline compliance reporting, and enrich knowledge security. It is effortless to put into practice, with no changes to present information constructions or person interactions read far more about the UDPS in the venture documentation.
Companies can detect uncommon habits, track knowledge utilization, and simplify authorization management, contributing to a more powerful security posture and streamlined info governance.
Discovered this post attention-grabbing? Observe us on Twitter and LinkedIn to read much more unique material we post.
Some parts of this article are sourced from:
thehackernews.com


 GitHub’s Secret Scanning Feature Now Covers AWS, Microsoft, Google, and Slack
GitHub’s Secret Scanning Feature Now Covers AWS, Microsoft, Google, and Slack