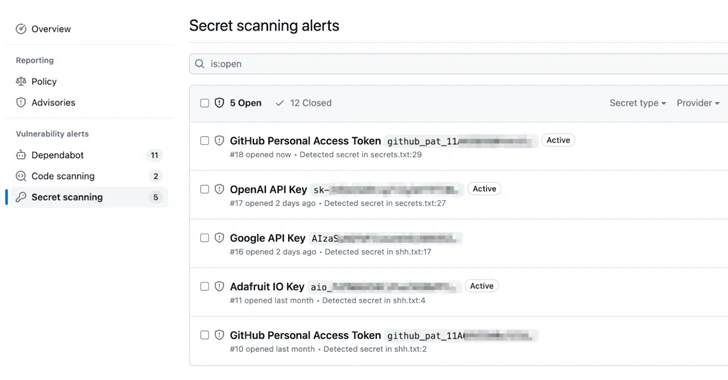
GitHub has announced an improvement to its solution scanning attribute that extends validity checks to preferred products and services these as Amazon Web Solutions (AWS), Microsoft, Google, and Slack.
Validity checks, introduced by the Microsoft subsidiary before this year, notify people whether uncovered tokens discovered by mystery scanning are active, thereby letting for powerful remediation measures. It was first enabled for GitHub tokens.
The cloud-based code hosting and model regulate service reported it intends to support much more tokens in the long term.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
To toggle the environment, business or business house owners and repository administrators can head to Settings > Code security and evaluation > Secret scanning and verify the selection “Quickly verify if a solution is legitimate by sending it to the pertinent spouse.”
Earlier this yr, GitHub also expanded top secret scanning alerts for all general public repositories and declared the availability of press protection to aid builders and maintainers proactively protected their code by scanning for highly identifiable tricks just before they are pushed.

The enhancement will come as Amazon previewed increased account defense requirements that will implement privileged users (aka root users) of an AWS Group account to swap on multi-factor authentication (MFA) commencing in mid-2024.
“MFA is just one of the most basic and most efficient techniques to improve account security, giving an extra layer of security to support protect against unauthorized people today from gaining obtain to systems or data,” Steve Schmidt, main security officer at Amazon, stated.
Weak or misconfigured MFA techniques also discovered a area among the top rated 10 most common network misconfigurations, according to a new joint advisory issued by the U.S. Countrywide Security Agency (NSA) and Cybersecurity and Infrastructure Security Company (CISA).

“Some varieties of MFA are susceptible to phishing, ‘push bombing,’ exploitation of Signaling System 7 (SS7) protocol vulnerabilities, and/or ‘SIM swap’ approaches,” the companies mentioned.
“These tries, if successful, might make it possible for a danger actor to attain access to MFA authentication credentials or bypass MFA and obtain the MFA-shielded programs.”
The other prevalent cybersecurity misconfigurations are as follows –
- Default configurations of program and applications
- Poor separation of consumer/administrator privilege
- Insufficient inside network monitoring
- Deficiency of network segmentation
- Inadequate patch administration
- Bypass of program access controls
- Insufficient access management lists (ACLs) on network shares and products and services
- Lousy credential cleanliness
- Unrestricted code execution
As mitigations, it really is advised that businesses remove default credentials and harden configurations disable unused services and put into action access controls prioritize patching audit and keep an eye on administrative accounts and privileges.

Software distributors have also been urged to apply secure by structure rules, use memory-risk-free programming languages the place probable, stay away from embedding default passwords, offer high-quality audit logs to clients at no additional cost, and mandate phishing-resistant MFA techniques.
“These misconfigurations illustrate (1) a development of systemic weaknesses in many big organizations, which includes individuals with mature cyber postures, and (2) the relevance of software program suppliers embracing safe-by-layout concepts to decrease the load on network defenders,” the organizations pointed out.
Discovered this short article appealing? Adhere to us on Twitter and LinkedIn to study extra special content material we article.
Some pieces of this report are sourced from:
thehackernews.com

 Supermicro’s BMC Firmware Found Vulnerable to Multiple Critical Vulnerabilities
Supermicro’s BMC Firmware Found Vulnerable to Multiple Critical Vulnerabilities