An emerging Python-based credential harvester and a hacking tool named Legion are remaining marketed by using Telegram as a way for risk actors to break into a variety of online companies for further more exploitation.
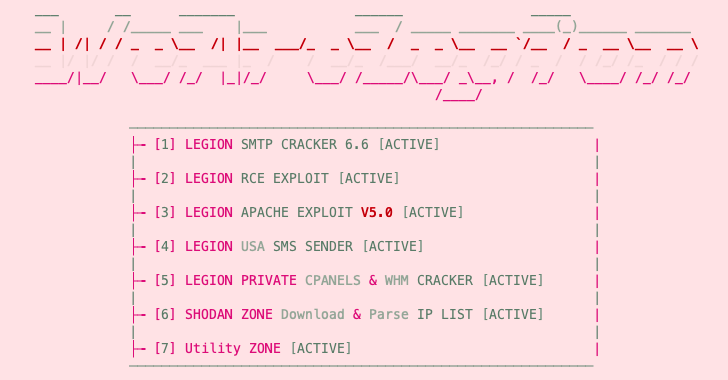
Legion, in accordance to Cado Labs, features modules to enumerate susceptible SMTP servers, perform distant code execution (RCE) attacks, exploit unpatched versions of Apache, and brute-pressure cPanel and WebHost Manager (WHM) accounts.
The malware is suspected to be connected to an additional malware relatives called AndroxGh0st that was initial documented by cloud security solutions providerLacework in December 2022.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Cybersecurity business SentinelOne, in an analysis released late very last month, exposed that AndroxGh0st is section of a complete toolset identified as AlienFox which is provided to threat actors to steal API keys and strategies from cloud services.
Apart from employing Telegram as a facts exfiltration position, Legion is created to exploit web servers jogging material administration systems (CMS), PHP, or PHP-primarily based frameworks like Laravel.
“It can retrieve qualifications for a extensive selection of web providers, this sort of as email suppliers, cloud services providers, server management programs, databases, and payment platforms like Stripe and PayPal,” Cado Labs mentioned.
Some of the other qualified providers include SendGrid, Twilio, Nexmo, AWS, Mailgun, Plivo, ClickSend, Mandrill, Mailjet, MessageBird, Vonage, Exotel, OneSignal, Clickatell, and TokBox.
The most important goal of the malware is to enable danger actors to hijack the solutions and weaponize the infrastructure for stick to-on attacks, like mounting opportunistic phishing campaigns.
The cybersecurity company explained it also discovered a YouTube channel that contains tutorial movies on how to use Legion, suggesting that the “software is greatly dispersed and is probably paid malware.” The YouTube channel, which was produced on June 15, 2021, stays active as of composing.
In addition, Legion retrieves AWS credentials from insecure or misconfigured web servers and produce SMS spam messages to users of U.S. mobile networks this kind of as AT&T, Sprint, T-Mobile, Verizon, and Virgin.
Forthcoming WEBINARLearn to Safe the Identity Perimeter – Proven Approaches
Strengthen your business security with our forthcoming qualified-led cybersecurity webinar: Explore Identification Perimeter tactics!
Never Miss out on Out – Conserve Your Seat!
“To do this, the malware retrieves the region code for a U.S. point out of the user’s deciding upon from the web-site www.randomphonenumbers.com,” security researcher Matt Muir said. “A rudimentary number generator functionality is then applied to create up a record of phone figures to goal.”
Yet another noteworthy facet of Legion is its skill to exploit very well-identified PHP vulnerabilities to sign-up a web shell for persistent distant access or execute destructive code.
The origins of the danger actor at the rear of the software, who goes by the alias “forzatools” on Telegram, remain not known, whilst the presence of Indonesian-language feedback in the source code suggests that the developer might be Indonesian or based in the country.
“Because this malware depends intensely on misconfigurations in web server technologies and frameworks these as Laravel, it is advised that users of these systems review their present security processes and make sure that insider secrets are correctly saved,” Muir claimed.
Found this report fascinating? Follow us on Twitter and LinkedIn to browse a lot more exceptional material we submit.
Some sections of this posting are sourced from:
thehackernews.com

 Pakistan-based Transparent Tribe Hackers Targeting Indian Educational Institutions
Pakistan-based Transparent Tribe Hackers Targeting Indian Educational Institutions