Banking and logistics industries are under the onslaught of a reworked variant of a malware termed Chaes.
“It has been through main overhauls: from currently being rewritten totally in Python, which resulted in decrease detection rates by standard defense systems, to a complete redesign and an improved communication protocol,” Morphisec stated in a new thorough complex create-up shared with The Hacker Information.
Chaes, which very first emerged in 2020, is known to target e-commerce prospects in Latin The us, especially Brazil, to steal sensitive monetary information and facts.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
A subsequent analysis from Avast in early 2022 discovered that the risk actors behind the operation, who simply call on their own Lucifer, experienced breached far more than 800 WordPress web-sites to supply Chaes to end users of Banco do Brasil, Loja Integrada, Mercado Bitcoin, Mercado Livre, and Mercado Pago.
Further more updates were detected in December 2022, when Brazilian cybersecurity enterprise Tempest Security Intelligence uncovered the malware’s use of Windows Administration Instrumentation (WMI) in its an infection chain to aid the collection of method metadata, this sort of as BIOS, processor, disk dimension, and memory info.

The most current iteration of the malware, dubbed Chae$ 4 in reference to debug log messages existing in the supply code, packs in “substantial transformations and enhancements,” together with an expanded catalog of products and services focused for credential theft as very well as clipper functionalities.
Inspite of the changes in the malware architecture, the overall supply system has remained the identical in attacks that were identified in January 2023.
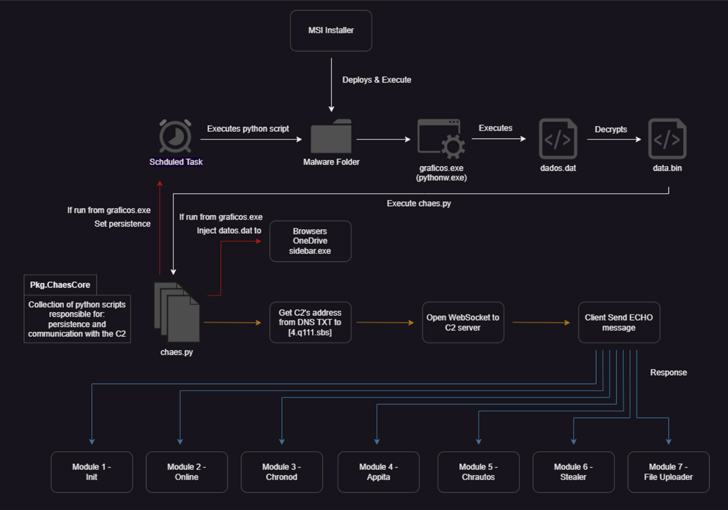
Possible victims landing on 1 of the compromised web sites are greeted by a pop-up concept inquiring them to download an installer for Java Runtime or an antivirus remedy, triggering the deployment of a destructive MSI file that, in change, launches a main orchestrator module regarded as ChaesCore.
The element is dependable for setting up a communication channel with the command-and-regulate (C2) server from where it fetches further modules that help write-up-compromise exercise and details theft –
- Init, which gathers intensive data about the system
- On the internet, which acts as a beacon to transmit a concept back to the attacker that the malware is running on the machine
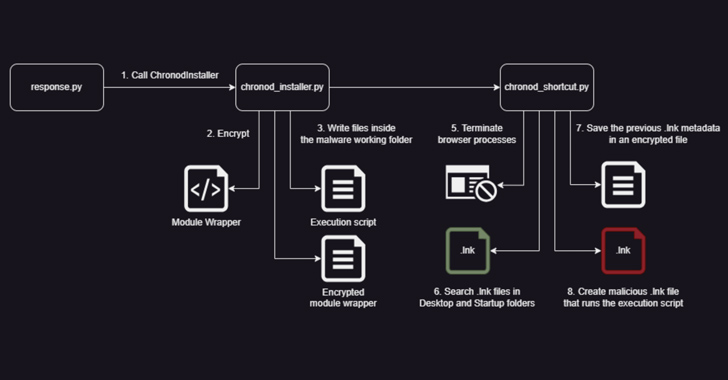
- Chronod, which steals login credentials entered in web browsers and intercept BTC, ETH, and PIX payment transfers
- Appita, a module with comparable capabilities as that of Chronod but especially developed to goal Itaú Unibanco’s desktop application (“itauaplicativo.exe”)
- Chrautos, an up-to-date version of Chronod and Appita that focuses on gathering data from Mercado Libre, Mercado Pago, and WhatsApp
- Stealer, an enhanced variant of Chrolog which plunders credit history card details, cookies, autofill, and other data stored in web browsers, and
- File Uploader, which uploads information relevant to MetaMask’s Chrome extension
Persistence on the host is accomplished by suggests of a scheduled endeavor, while C2 communications entail the use of WebSockets, with the implant working in an infinite loop to await even more guidance from the distant server.
The focusing on of cryptocurrency transfers and quick payments through Brazils’ PIX system is a noteworthy addition that underscores the risk actors’ fiscal motivations.
Impending WEBINARDetect, Reply, Protect: ITDR and SSPM for Total SaaS Security
Explore how Identification Danger Detection & Reaction (ITDR) identifies and mitigates threats with the support of SSPM. Learn how to protected your corporate SaaS programs and guard your details, even soon after a breach.
Supercharge Your Competencies
“The Chronod module introduces yet another ingredient used in the framework, a ingredient referred to as Module Packer,” Morphisec described. “This part offers the module its own persistence and migration mechanisms, doing work substantially like the ChaesCore’s one.”
This process involves altering all shortcut files (LNK) connected with web browsers (e.g., Google Chrome, Microsoft Edge, Courageous, and Avast Secure Browser) to execute the Chronod module as an alternative of the precise browser.
“The malware works by using Google’s DevTools Protocol to hook up to the present browser occasion,” the company stated. “This protocol permits direct conversation with the interior browser’s operation in excess of WebSockets.”
“The broad array of abilities exposed by this protocol lets the attacker to run scripts, intercept network requests, read through Post bodies prior to becoming encrypted, and a great deal more.”
Observed this write-up fascinating? Stick to us on Twitter and LinkedIn to browse a lot more unique content material we write-up.
Some elements of this short article are sourced from:
thehackernews.com

 Way Too Vulnerable: Join this Webinar to Understand and Strengthen Identity Attack Surface
Way Too Vulnerable: Join this Webinar to Understand and Strengthen Identity Attack Surface