A new malware software that allows cybercriminal actors to establish malicious Windows shortcut (.LNK) files has been noticed for sale on cybercrime boards.
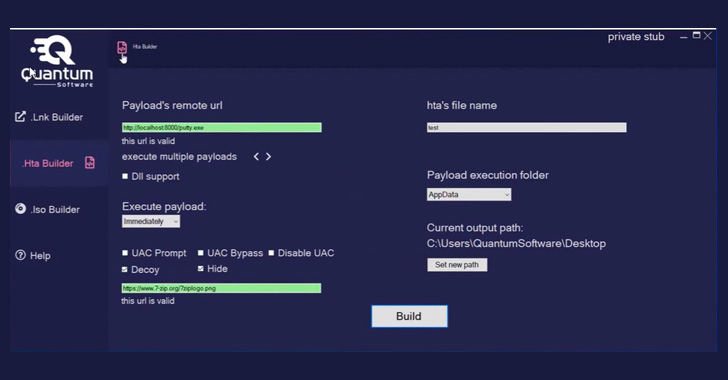
Dubbed Quantum Lnk Builder, the software program tends to make it doable to spoof any extension and choose from more than 300 icons, not to point out assist UAC and Windows SmartScreen bypass as nicely as “numerous payloads per .LNK” file. Also available are abilities to create .HTA and disk impression (.ISO) payloads.
Quantum Builder is readily available for lease at different selling price points: €189 a month, €355 for two months, €899 for 6 months, or as a one-off life span purchase for €1,500.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“.LNK documents are shortcut data files that reference other information, folders, or programs to open up them,” Cyble scientists stated in a report. “The [threat actor] leverages the .LNK documents and drops destructive payloads working with LOLBins [living-off-the-land binaries].”
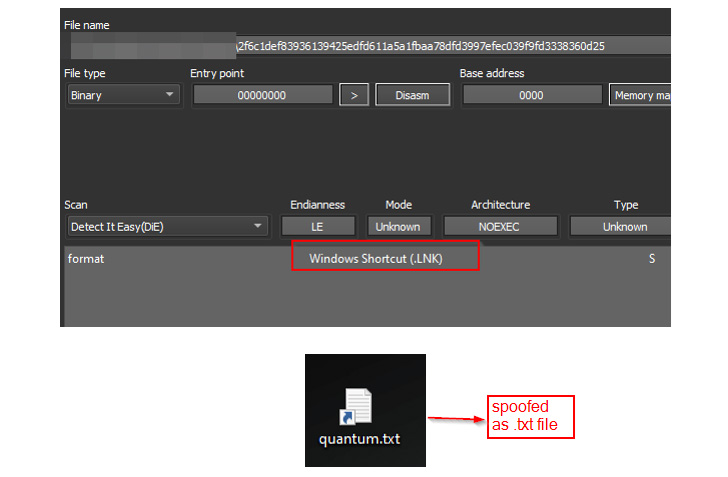
Early evidence of malware samples employing Quantum Builder in the wild is said to date back to May perhaps 24, masquerading as harmless-seeking text documents (“exam.txt.lnk”).
“By default, Windows hides the .LNK extension, so if a file is named as file_name.txt.lnk, then only file_name.txt will be obvious to the consumer even if the show file extension solution is enabled,” the researchers said. “For this kind of reasons, this could be an interesting option for TAs, utilizing the .LNK information as a disguise or smokescreen.”
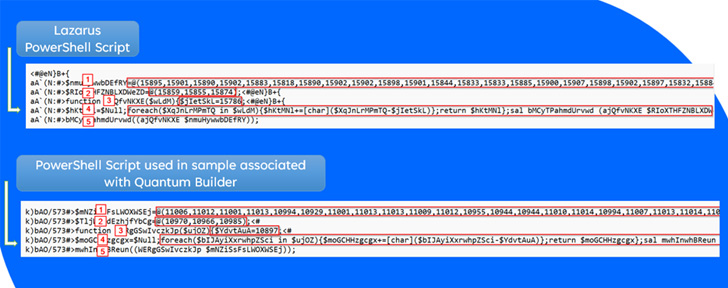
Launching the .LNK file executes PowerShell code that, in switch, runs a HTML application (“bdg.hta”) file hosted on Quantum’s web site (“quantum-software program[.]on line”) employing MSHTA, a legitimate Windows utility that’s utilized to operate HTA files.
Quantum Builder is stated to share ties with the North Korean-centered Lazarus Group primarily based on source code-level overlaps in the software and the latter’s modus operandi of leveraging .LNK files for delivering more phase payloads, indicating its prospective use by APT actors in their attacks.

The growth arrives as operators guiding Bumblebee and Emotet are shifting to .LNK information as a conduit to trigger the an infection chains following Microsoft’s conclusion to disable Visual Essential for Programs (VBA) macros by default across its products and solutions before this 12 months.
Bumblebee, a replacement for BazarLoader malware 1st noticed in March, features as a backdoor made to give the attackers persistent obtain to compromised systems and a downloader for other malware, which include Cobalt Strike and Sliver.
The malware’s abilities have also manufactured it a tool of choice for menace actors, with 413 incidents of Bumblebee an infection documented in May well 2022, up from 41 in April, in accordance to Cyble.
“Bumblebee is a new and extremely advanced malware loader that employs considerable evasive maneuvers and anti-examination methods, which includes complicated anti-virtualization approaches,” the researchers said. “It is very likely to come to be a well known instrument for ransomware groups to provide their payload.”
Identified this report intriguing? Adhere to THN on Fb, Twitter and LinkedIn to browse more distinctive material we post.
Some elements of this posting are sourced from:
thehackernews.com

 Log4Shell Still Being Exploited to Hack VMWare Servers to Exfiltrate Sensitive Data
Log4Shell Still Being Exploited to Hack VMWare Servers to Exfiltrate Sensitive Data