A China-dependent highly developed persistent risk (APT) team is possibly deploying short-lived ransomware households as a decoy to protect up the genuine operational and tactical goals guiding its campaigns.
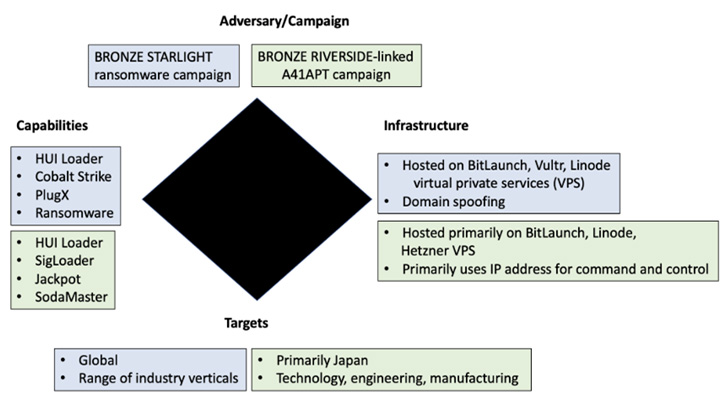
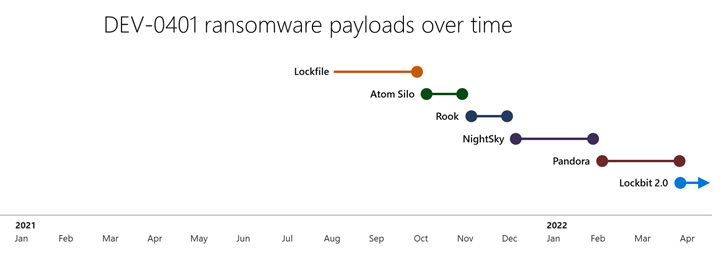
The activity cluster, attributed to a hacking group dubbed Bronze Starlight by Secureworks, will involve the deployment of post-intrusion ransomware such as LockFile, Atom Silo, Rook, Evening Sky, Pandora, and LockBit 2..
“The ransomware could distract incident responders from figuring out the menace actors’ correct intent and minimize the likelihood of attributing the destructive activity to a government-sponsored Chinese threat group,” the researchers mentioned in a new report. “In each circumstance, the ransomware targets a little quantity of victims about a reasonably quick period of time of time ahead of it ceases operations, apparently completely.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Bronze Starlight, energetic because mid-2021, is also tracked by Microsoft less than the emerging risk cluster moniker DEV-0401, with the tech big emphasizing its involvement in all phases of the ransomware attack cycle suitable from original obtain to the payload deployment.
Compared with other RaaS teams that purchase access from original access brokers (IABs) to enter a network, attacks mounted by the actor are characterized by the use of unpatched vulnerabilities affecting Exchange Server, Zoho ManageEngine ADSelfService Plus, Atlassian Confluence (such as the newly disclosed flaw), and Apache Log4j.
Considering the fact that August 2021, the team is claimed to have cycled via as numerous as six unique ransomware strains these as LockFile (August), Atom Silo (October), Rook (November), Night Sky (December), Pandora (February 2022), and most a short while ago LockBit 2. (April).
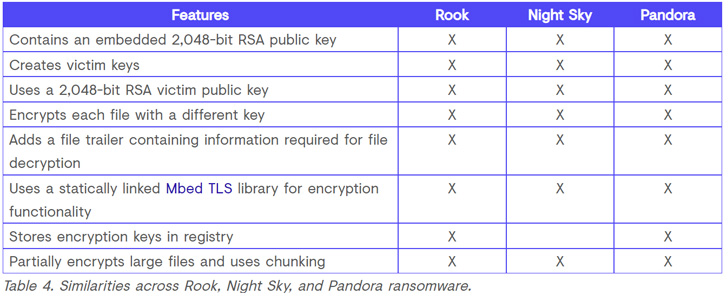
What is actually much more, similarities have been uncovered amongst LockFile and Atom Silo as effectively as involving Rook, Night time Sky, and Pandora — the latter 3 derived from Babuk ransomware, whose supply code leaked in September 2021 — indicating the operate of a popular actor.
“Mainly because DEV-0401 maintains and frequently rebrands their very own ransomware payloads, they can seem as different teams in payload-driven reporting and evade detections and steps versus them,” Microsoft noted previous thirty day period.
Upon attaining a foothold inside a network, Bronze Starlight is identified to count on approaches like employing Cobalt Strike and Windows Management Instrumentation (WMI) for lateral motion, though starting off this month, the team has begun replacing Cobalt Strike with the Sliver framework in their attacks.
Other observed tradecraft relates to the use of HUI Loader to launch future-phase encrypted payloads these types of as PlugX and Cobalt Strike Beacons, the latter of which is employed to supply the ransomware, but not prior to acquiring privileged Area Administrator qualifications.
“The use of HUI Loader to load Cobalt Strike Beacon, the Cobalt Strike Beacon configuration data, the C2 infrastructure, and the code overlap suggest that the exact same threat team is connected with these 5 ransomware families,” the researchers spelled out.

It is really worthy of pointing out that equally HUI Loader and PlugX, along with ShadowPad, are malware historically set to use by Chinese nation-condition adversarial collectives, lending credence to the chance that Bronze Starlight is far more geared in direction of espionage than rapid monetary positive aspects.
On major of that, the victimology sample spanning across the distinctive ransomware strains exhibits that a bulk of the targets are probably to be of a lot more curiosity to Chinese government-sponsored groups focused on extensive-phrase intelligence accumulating.
The critical victims encompass pharmaceutical corporations in Brazil and the U.S., a U.S.-based mostly media organization with workplaces in China and Hong Kong, electronic part designers and makers in Lithuania and Japan, a law company in the U.S., and an aerospace and protection division of an Indian conglomerate.
To that conclude, the ransomware operations, in addition to furnishing a implies to exfiltrate facts as element of the double extortion “title-and-shame” plan, also offer you twin rewards in that it lets the menace actor to demolish forensic evidence of their malicious functions and act as a distraction from knowledge theft.
“It is plausible that Bronze Starlight deploys ransomware as a smokescreen instead than for fiscal acquire, with the fundamental commitment of stealing mental assets or conducting espionage,” the researchers explained.
Located this posting exciting? Observe THN on Facebook, Twitter and LinkedIn to study extra special articles we put up.
Some parts of this article are sourced from:
thehackernews.com


 New ‘Quantum’ Builder Lets Attackers Easily Create Malicious Windows Shortcuts
New ‘Quantum’ Builder Lets Attackers Easily Create Malicious Windows Shortcuts