A new information stealer has been found leveraging Lua bytecode for extra stealth and sophistication, conclusions from McAfee Labs expose.
The cybersecurity agency has assessed it to be a variant of a regarded malware referred to as RedLine Stealer owing to the actuality that the command-and-management (C2) server IP handle has been beforehand identified as associated with the malware.
RedLine Stealer, very first documented in March 2020, is normally delivered via email and malvertising strategies, either straight or by way of exploit kits and loader malware like dotRunpeX and HijackLoader.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The off-the-shelf malware is able of harvesting facts from cryptocurrency wallets, VPN software, and web browsers, such as saved qualifications, autocomplete knowledge, credit rating card facts, and geolocations based on the victims’ IP addresses.
In excess of the decades, RedLine Stealer has been co-opted by numerous danger actors into their attack chains, producing it a commonplace strain spanning North The us, South The usa, Europe, Asia, and Australia.
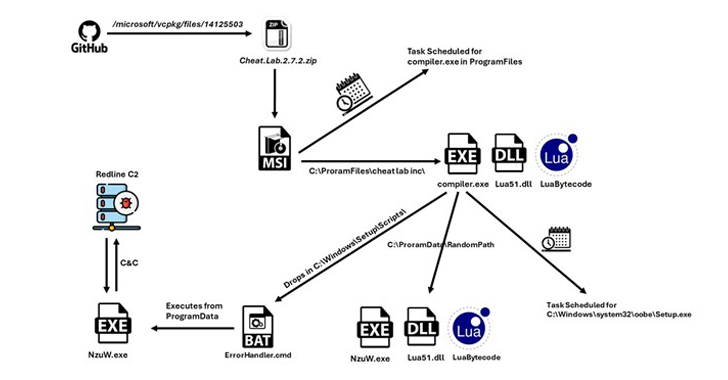
The an infection sequence recognized by McAfee abuses GitHub, employing two of Microsoft’s official repositories for its implementation of the C++ Conventional Library (STL) and vcpkg to host the malware-laden payload in the kind of ZIP archives.

It is now not identified how the information came to be uploaded to the repository, but the approach is a signal that threat actors are weaponizing the trust connected with reputable repositories to distribute malware. The ZIP documents are no for a longer time offered for obtain from the Microsoft repositories.
The ZIP archive (“Cheat.Lab.2.7.2.zip” and “Cheater.Pro.1.6..zip”) masquerades as a match cheat, indicating that players are very likely the goal of the marketing campaign. It will come fitted with an MSI installer which is made to run the destructive Lua bytecode.
“This solution supplies the gain of obfuscating destructive stings and steering clear of the use of very easily recognizable scripts like wscript, JScript, or PowerShell script, therefore maximizing stealth and evasion capabilities for the menace actor,” researchers Mohansundaram M. and Neil Tyagi stated.
In an attempt to pass the malware to other programs, the MSI installer displays a concept urging the target to share the system with their buddies in buy to get the unlocked model of the computer software.
The “compiler.exe” executable within just the installer, upon operating the Lua bytecode embedded inside of the “readme.txt” file present in the ZIP archive, sets up persistence on the host utilizing a scheduled endeavor and drops a CMD file, which, in change, runs “compiler.exe” below a further identify “NzUw.exe.”
In the ultimate phase, “NzUw.exe” initiates communications with a command-and-control (C2) server more than HTTP, the aforementioned IP address attributed to RedLine.
The malware functions a lot more like a backdoor, carrying out responsibilities fetched from the C2 server (e.g., using screenshots) and exfiltrating the outcomes again to it.
The specific strategy by which the hyperlinks to the ZIP archives are dispersed is presently mysterious. Previously this month, Checkmarx revealed how risk actors are using gain of GitHub’s search operation to trick unsuspecting people into downloading malware-laden repositories.
The enhancement comes as Recorded Future in-depth a “large-scale Russian-language cybercrime operation” that singles out the gaming community and leverages faux Web3 gaming lures to deliver malware capable of stealing sensitive data from macOS and Windows buyers, a technique referred to as lure phishing.
“The campaign includes building imitation Web3 gaming assignments with slight identify and branding modifications to seem respectable, along with fake social media accounts to bolster their authenticity,” Insikt Team stated.

“The key webpages of these assignments provide downloads that, when put in, infect products with several types of “infostealer” malware these kinds of as Atomic macOS Stealer (AMOS), Stealc, Rhadamanthys, or RisePro, relying on the working process.”
It also follows a wave of malware campaigns targeting enterprise environments with loaders this kind of as PikaBot and a new pressure termed NewBot Loader.
“Attackers shown a various array of techniques and an infection vectors in each and every campaign, aiming to produce the PikaBot payload,” McAfee reported.
This features a phishing attack that takes benefit of email dialogue hijacking and a Microsoft Outlook flaw referred to as MonikerLink (CVE-2024-21413) to entice victims into downloading the malware from an SMB share.
Discovered this post exciting? Abide by us on Twitter and LinkedIn to read more unique articles we write-up.
Some components of this report are sourced from:
thehackernews.com

 Palo Alto Networks Discloses More Details on Critical PAN-OS Flaw Under Attack
Palo Alto Networks Discloses More Details on Critical PAN-OS Flaw Under Attack