People of the CrushFTP company file transfer computer software are being urged to update to the most up-to-date edition next the discovery of a security flaw that has come less than focused exploitation in the wild.
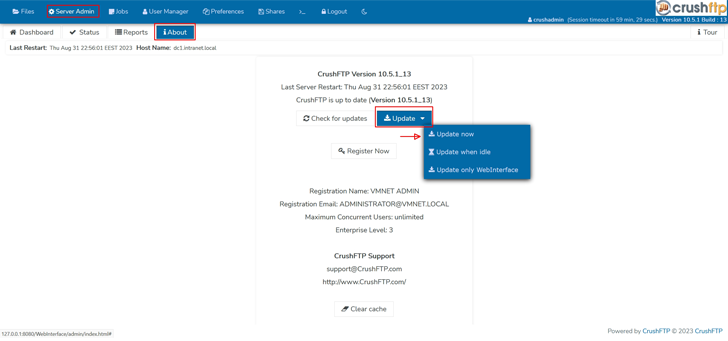
“CrushFTP v11 versions underneath 11.1 have a vulnerability exactly where users can escape their VFS and obtain process data files,” CrushFTP reported in an advisory produced Friday. “This has been patched in v11.1..”
That reported, prospects who are operating their CrushFTP circumstances within a DMZ (demilitarized zone) limited environment are safeguarded from the attacks.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Simon Garrelou of Airbus CERT has been credited with getting and reporting the flaw. It has nevertheless to be assigned a CVE identifier.
Cybersecurity enterprise CrowdStrike, in a article shared on Reddit, said it has noticed an exploit for the flaw staying made use of in the wild in a “targeted trend.”
These intrusions are reported to have generally qualified U.S. entities, with the intelligence gathering action suspected to be politically motivated.
“CrushFTP customers should really keep on to comply with the vendor’s web page for the most up-to-date guidance and prioritize patching,” CrowdStrike explained.
Uncovered this report intriguing? Observe us on Twitter and LinkedIn to study more exclusive articles we publish.
Some areas of this report are sourced from:
thehackernews.com


 BlackTech Targets Tech, Research, and Gov Sectors New ‘Deuterbear’ Tool
BlackTech Targets Tech, Research, and Gov Sectors New ‘Deuterbear’ Tool